Deviant Ollam12:26 PM
when i say "any one" i mean any super clear one
 silly question, do you ever use a stethoscope ?
silly question, do you ever use a stethoscope ?
 @anfractuosity something similar! i use an audio pickup amp at times
@anfractuosity something similar! i use an audio pickup amp at times
 ooh, cool i wasn't sure if they where really used
ooh, cool i wasn't sure if they where really used
 i saw some safe locks which claim to be resistant against x-ray which sounds interesting i thought
i saw some safe locks which claim to be resistant against x-ray which sounds interesting i thought
 think of it as a stethoscope but it mag-mounts to the safe door. and it's not like a little cup on the end... it has a metal probe that hears vibrations within the safe. (and you're mostly hearing contact points where the nose interacts with the drive cam, as opposed to hearing the "wheels" as it were)
think of it as a stethoscope but it mag-mounts to the safe door. and it's not like a little cup on the end... it has a metal probe that hears vibrations within the safe. (and you're mostly hearing contact points where the nose interacts with the drive cam, as opposed to hearing the "wheels" as it were)
 I'd buy safe cracking 101 if I could. I have a couple of tell coin safes I'd like to open and put to use.
I'd buy safe cracking 101 if I could. I have a couple of tell coin safes I'd like to open and put to use.
 neat @Deviant Ollam :)
neat @Deviant Ollam :)
 Do you have any tools that caused a "where has this been all my life?" moment. (For me, the recent answers are Knipex cutters and step drills.)
Do you have any tools that caused a "where has this been all my life?" moment. (For me, the recent answers are Knipex cutters and step drills.)
 @anfractuosity Grade 1R safes, yes. "resistant to Radiographic attack" ... often Delrin plastic wheels. they have other vulnerabilities
@anfractuosity Grade 1R safes, yes. "resistant to Radiographic attack" ... often Delrin plastic wheels. they have other vulnerabilities
 Safe against x-rays could just mean they're lead lined.
Safe against x-rays could just mean they're lead lined.
 @Douglas Henke the A-1 pak-a-punch and the new Lishi 2-in-1 decoder picks
@Douglas Henke the A-1 pak-a-punch and the new Lishi 2-in-1 decoder picks
 @Deviant Ollam heh neat, could you expand on other vulnerabilities, if you can
@Deviant Ollam heh neat, could you expand on other vulnerabilities, if you can
 @Tametomo shielding became a ladders-and-walls game during the cold war. new materials, like polymer wheels, were the solution
@Tametomo shielding became a ladders-and-walls game during the cold war. new materials, like polymer wheels, were the solution
 @anfractuosity you can melt the wheels... enough heat or even acid injected in the right spot, and the wheels just fall apart, lol
@anfractuosity you can melt the wheels... enough heat or even acid injected in the right spot, and the wheels just fall apart, lol
 haha wow
haha wow
 that's very cool
that's very cool
 Aren't most modern containers electronic locks?
Aren't most modern containers electronic locks?
![]() @Deviant Ollam Can you point me to any case studies or news articles where poor physical security practices have directly led to thefts or data breaches? I know it's implied, but sometimes its good to have independent sources to show that not focusing on this stuff has real consequences.
@Deviant Ollam Can you point me to any case studies or news articles where poor physical security practices have directly led to thefts or data breaches? I know it's implied, but sometimes its good to have independent sources to show that not focusing on this stuff has real consequences.
![]() Get the safe too hot and the fusible link goes and triggers relockers and no one is opening that safe!
Get the safe too hot and the fusible link goes and triggers relockers and no one is opening that safe!
![]() Management folks are not always the most tech savvy
Management folks are not always the most tech savvy
 @oz i would say that most modern "building security solutions" are moving to electronic. and electronic locks are making in-roads even in residential spaces, yes. but mechanical locks will still be with us for quite a while
@oz i would say that most modern "building security solutions" are moving to electronic. and electronic locks are making in-roads even in residential spaces, yes. but mechanical locks will still be with us for quite a while
 @thomas.august most stories like that are ones that entail stolen laptops or other endpoints
@thomas.august most stories like that are ones that entail stolen laptops or other endpoints
![]() To anyone who thinks they might try drilling a quality safe, watch out for tempered glass between the door and the lock. Break it and relockers trigger.
To anyone who thinks they might try drilling a quality safe, watch out for tempered glass between the door and the lock. Break it and relockers trigger.
 @Eric yes, it's a delicate balance, that kind of attack
@Eric yes, it's a delicate balance, that kind of attack
 The security industry isn't often what outsiders think it is. You have to deal with risk bars, which are just a way of saying "will the solution cost more than the potential problem"? So depending who does the calculations, something can either be critical to fix, or something just worth ignoring.
The security industry isn't often what outsiders think it is. You have to deal with risk bars, which are just a way of saying "will the solution cost more than the potential problem"? So depending who does the calculations, something can either be critical to fix, or something just worth ignoring.
![]() Do you think that electronic systems have higher a higher barrier to entry for the common criminal?
Do you think that electronic systems have higher a higher barrier to entry for the common criminal?
 Here's a question: do electronic safes have built-in back doors, like service technician codes so they can get in no matter what the owner does?
Here's a question: do electronic safes have built-in back doors, like service technician codes so they can get in no matter what the owner does?
 @Deviant Ollam I was thinking of modern classified document storage containers. I thought that mechanical locks could not meet the requirements. \
@Deviant Ollam I was thinking of modern classified document storage containers. I thought that mechanical locks could not meet the requirements. \
![]() Really really really old safes had explosives loaded in them. Watch out.
Really really really old safes had explosives loaded in them. Watch out.
 here's another interesting kind of auto lock with a specialized entry pick tool...
here's another interesting kind of auto lock with a specialized entry pick tool...
 @oz this is correct as of FF-L-2740
@oz this is correct as of FF-L-2740
![]()

 I get clients all the time trying to come up with the dumbest ways to explain away why they can safely ignore something, or try to fault the method in which the vulnerability was found. Until a company gets seriously bitten, security is something often seen as something which can be argued away.
I get clients all the time trying to come up with the dumbest ways to explain away why they can safely ignore something, or try to fault the method in which the vulnerability was found. Until a company gets seriously bitten, security is something often seen as something which can be argued away.
![]() Any experience with those?
Any experience with those?
 @oz all modern containers for C, S, or TS materials must support "true" million combinations and auditing capability so for those reasons alone, effectively electro-mechanical locks are the only ones allowed on GSA containers now, etc
@oz all modern containers for C, S, or TS materials must support "true" million combinations and auditing capability so for those reasons alone, effectively electro-mechanical locks are the only ones allowed on GSA containers now, etc
 @Nicolas Tremblay that looks like a kind of clone of the Mul-T-Lock MT5
@Nicolas Tremblay that looks like a kind of clone of the Mul-T-Lock MT5
![]() Dev - when we get back to in-person CONs, what are you most interested to talk about?
Dev - when we get back to in-person CONs, what are you most interested to talk about?
 (but a cheaper clone... without the interactive element on the key tip)
(but a cheaper clone... without the interactive element on the key tip)
![]() I'd say the electronic physical locking systems can be more secure when installed properly. But all too often, it's low bidders and low skill hacking the thing into a working state. Not bothering to connect tamper switches to 24hr alarm zones, drilling incorrectly, skipping 'unneeded' connections.
I'd say the electronic physical locking systems can be more secure when installed properly. But all too often, it's low bidders and low skill hacking the thing into a working state. Not bothering to connect tamper switches to 24hr alarm zones, drilling incorrectly, skipping 'unneeded' connections.
![]() Chinese Euro-lock
Chinese Euro-lock
 I wonder how much those requirements contribute to real security. It's finite, but I wonder what the real contribution is vs how much is "fighting the last war"
I wonder how much those requirements contribute to real security. It's finite, but I wonder what the real contribution is vs how much is "fighting the last war"
 @Scott H that's a good question, hah. i am not sure right now. we've had some good RFID content for a while that we'll release eventually
@Scott H that's a good question, hah. i am not sure right now. we've had some good RFID content for a while that we'll release eventually
![]() RFID as in hacking entry locks? Or ???
RFID as in hacking entry locks? Or ???
 @eric Yeah, things are often about trying to save a few dollars here or there. Tends to take a major security event and a culture change to get a company to care about actual security. Until then, it's basically about trying to justify doing nothing or as little as possible.
@eric Yeah, things are often about trying to save a few dollars here or there. Tends to take a major security event and a culture change to get a company to care about actual security. Until then, it's basically about trying to justify doing nothing or as little as possible.
 Cooper (From Dangerous Things), Max (from TOOOL), and I have an implantable RFID talk
Cooper (From Dangerous Things), Max (from TOOOL), and I have an implantable RFID talk
 but my team is also doing things in the entry space a great deal, too
but my team is also doing things in the entry space a great deal, too
 Always more fun to deal with clients who understand the value of the service being provided, rather than seeing it as a necessary regulation hurdle that needs to be muffled as much as possible.
Always more fun to deal with clients who understand the value of the service being provided, rather than seeing it as a necessary regulation hurdle that needs to be muffled as much as possible.
![]() @Deviant Ollam is there a good guide to getting started with RFID?
@Deviant Ollam is there a good guide to getting started with RFID?
 @Tametomo most definitely
@Tametomo most definitely
 @tonkas64 i'd sound self-serving if i said "Red Team Alliance has a terrific 2-day Access Control training" =)
@tonkas64 i'd sound self-serving if i said "Red Team Alliance has a terrific 2-day Access Control training" =)
![]() @Deviant Ollam ;-) do you run them in the UK?
@Deviant Ollam ;-) do you run them in the UK?
![]() Is it just me, but I find HF RFID very confusing
Is it just me, but I find HF RFID very confusing
![]() There is NFC, mifare, the stuff credit cards use
There is NFC, mifare, the stuff credit cards use
 i have a venn diagram or two that can help...
i have a venn diagram or two that can help...
 @Tametomo Always better to deal with a truly informed client regardless of the topic. I consult for a living, and I'll pick a skilled client over a clueless one (even a benign clueless one) and day
@Tametomo Always better to deal with a truly informed client regardless of the topic. I consult for a living, and I'll pick a skilled client over a clueless one (even a benign clueless one) and day
![]() Cool
Cool

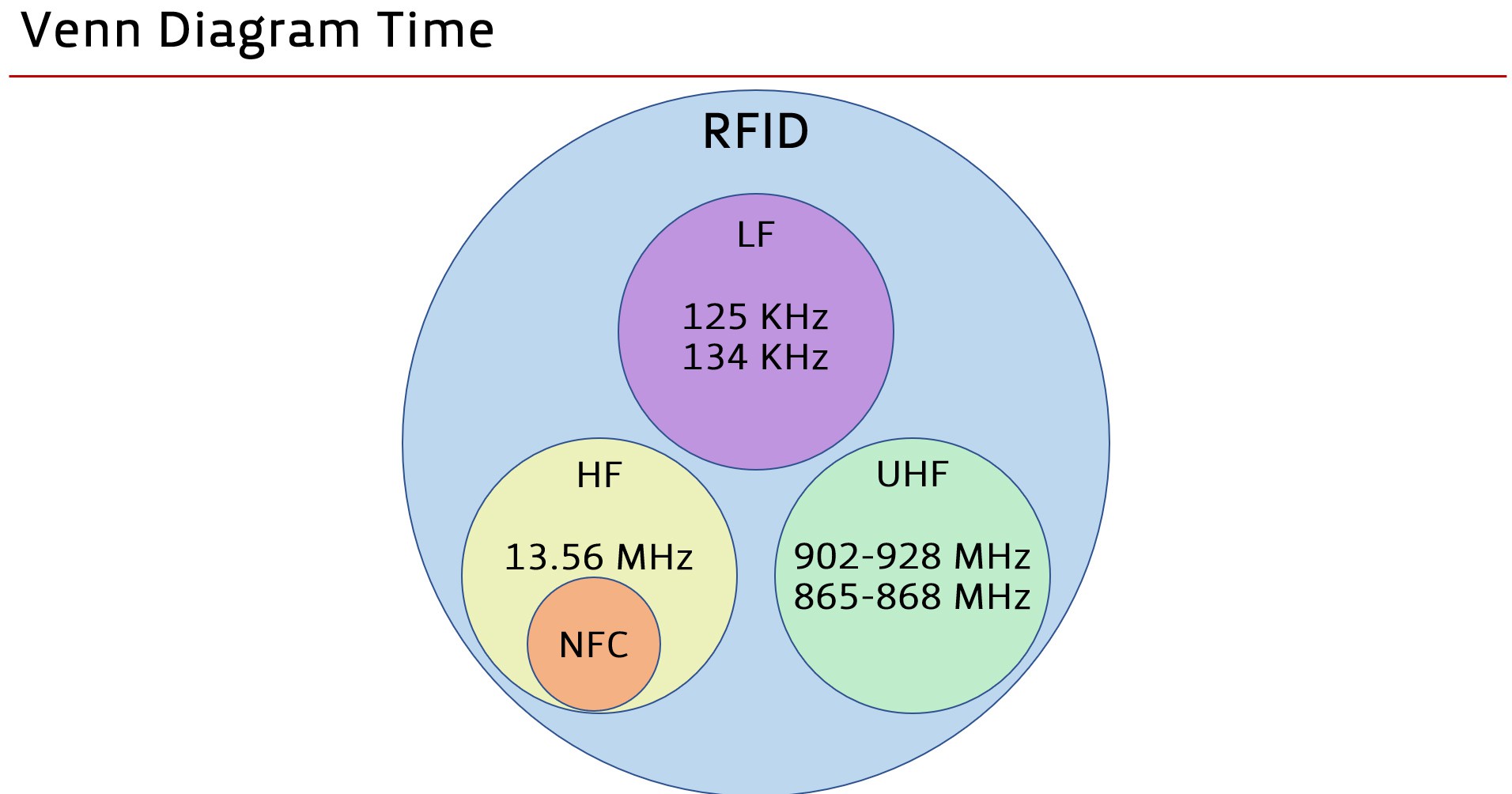
 from my slides
from my slides
 it's helpful to first recognize that "RFID" is, broadly, in three groups: Low Frequency, High Frequency, and Ultra High Frequency. (the latter is basically never used for access control, etc, so we'll leave that aside... that's a tech used in things like tracking tags... think warehouse inventory, luggage, etc)
it's helpful to first recognize that "RFID" is, broadly, in three groups: Low Frequency, High Frequency, and Ultra High Frequency. (the latter is basically never used for access control, etc, so we'll leave that aside... that's a tech used in things like tracking tags... think warehouse inventory, luggage, etc)

![]() Wow, didn't know the freq. were all over. I really need to start working with RFID
Wow, didn't know the freq. were all over. I really need to start working with RFID
 @oz Yup, but you don't always get to choose the whole chain. Sometimes the client you're working with is subcontracting with someone else, who is the one being the pill. Always can tell the client that they suck, but sometimes they're large companies themselves, so... yeah.
@oz Yup, but you don't always get to choose the whole chain. Sometimes the client you're working with is subcontracting with someone else, who is the one being the pill. Always can tell the client that they suck, but sometimes they're large companies themselves, so... yeah.
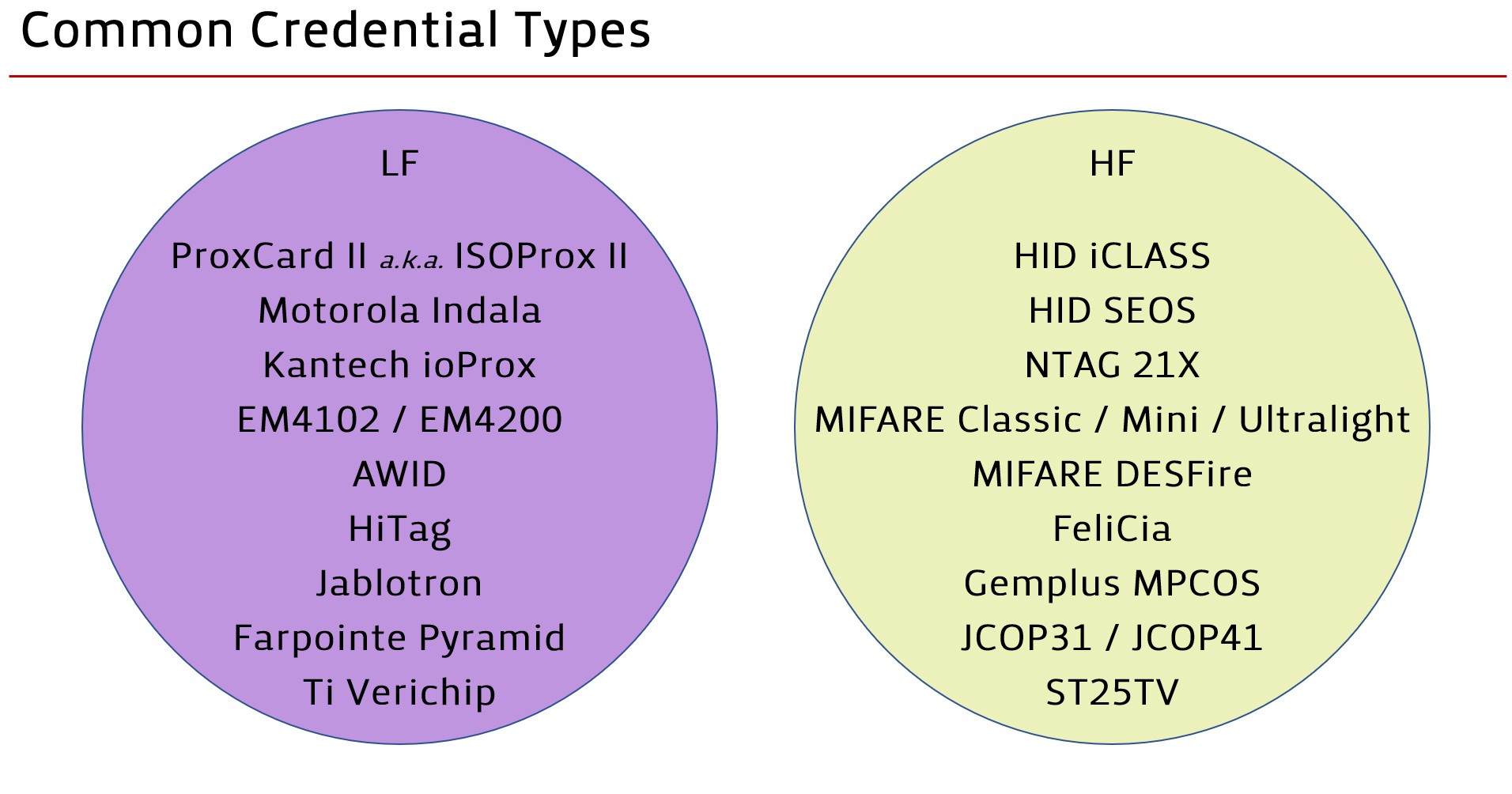
 among Low Frequency and High Frequency tags, there are a wide array of different credential technologies (and protocols, effectively)
among Low Frequency and High Frequency tags, there are a wide array of different credential technologies (and protocols, effectively)
![]() Cool, did you do a talk about just RFID hacking? Would love to watch it
Cool, did you do a talk about just RFID hacking? Would love to watch it
 you may recognize some of those names in the second slide with two circles
you may recognize some of those names in the second slide with two circles
![]() @Deviant Ollam nice they help a lot, there's just so much to find out
@Deviant Ollam nice they help a lot, there's just so much to find out
 Like I said, it usually takes getting hit seriously and a culture change to really get that attitude cemented.
Like I said, it usually takes getting hit seriously and a culture change to really get that attitude cemented.
 but i can simplify this a lot for you folk who are looking to acquire tools or RFID tags for hacking...
but i can simplify this a lot for you folk who are looking to acquire tools or RFID tags for hacking...
 And then sometimes it's even more complicated than that too. Might just be specific divisions that suck.
And then sometimes it's even more complicated than that too. Might just be specific divisions that suck.
 Especially for global companies.
Especially for global companies.

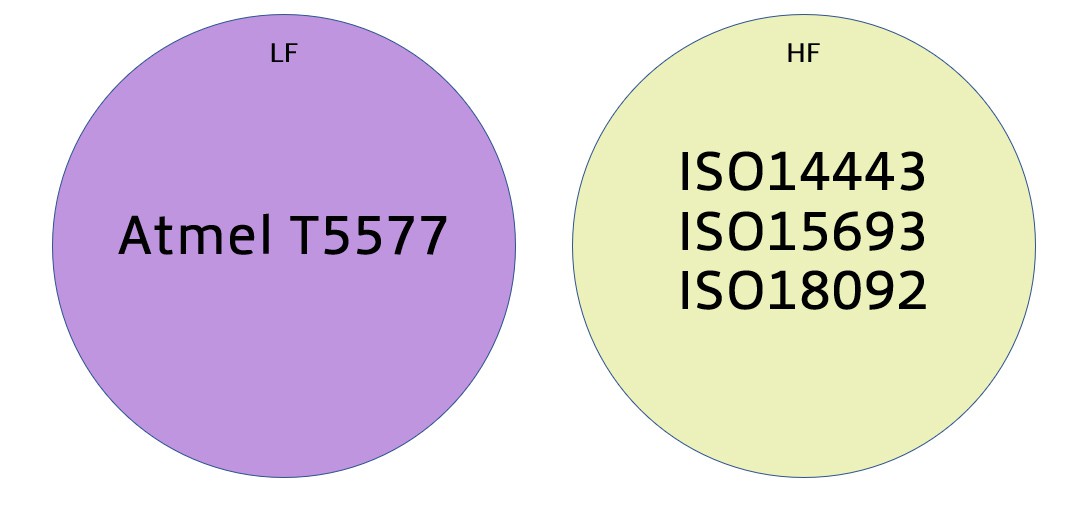
 boom... simplified
boom... simplified
 on the Low Freq side, the Atmel T5577 chip can emulate almost all existing, common-use credential types
on the Low Freq side, the Atmel T5577 chip can emulate almost all existing, common-use credential types
 on the high frequency side, while there are many technologies, there are at least some real standards bodies overseeing them
on the high frequency side, while there are many technologies, there are at least some real standards bodies overseeing them
![]() Was there any research into using phones with NFC as a proxmark for HF tags?
Was there any research into using phones with NFC as a proxmark for HF tags?
![]() So the black hats are using these too - are there common types of targets, or is it more of a, "we want to break into abc company for xyz reason" ?
So the black hats are using these too - are there common types of targets, or is it more of a, "we want to break into abc company for xyz reason" ?
 What would you recommend for a HF implantable chip? I've been looking at the Dangerous Things xNT. Ideally I'd like something that would be programmable or upgradable, if they exist.
What would you recommend for a HF implantable chip? I've been looking at the Dangerous Things xNT. Ideally I'd like something that would be programmable or upgradable, if they exist.
 @pop13 proxmark?
@pop13 proxmark?
 @thomc the xNT is great, but have you seen the NExT ? (it's the xNT and the low freq xEM in the same package)
@thomc the xNT is great, but have you seen the NExT ? (it's the xNT and the low freq xEM in the same package)
 @pop13 say again? phones with NFC as proxmark?
@pop13 say again? phones with NFC as proxmark?
 @Deviant Ollam Oh I haven't seen that, that sounds fantastic. Many thanks
@Deviant Ollam Oh I haven't seen that, that sounds fantastic. Many thanks
 @thomc you bet! https://dangerousthings.com/product/next/
@thomc you bet! https://dangerousthings.com/product/next/
 Thanks for taking the time to be here and answer all of our questions @Deviant Ollam !! I love your work! ... One question for you: I know alarm systems are nearly impossible to bypass (perhaps considered holy grails?), unless mitm before trigger goes to central ... anyways, have you ever encountered one on an engagement?
Thanks for taking the time to be here and answer all of our questions @Deviant Ollam !! I love your work! ... One question for you: I know alarm systems are nearly impossible to bypass (perhaps considered holy grails?), unless mitm before trigger goes to central ... anyways, have you ever encountered one on an engagement?
![]() Yeah, was there any research into emulating tags and cloning tags discreetly?
Yeah, was there any research into emulating tags and cloning tags discreetly?
 @0xOverflow imma leave this here... https://redteamalliance.com/Red%20Team%20Alliance%20Alarm%20Bypass%20(2-day).pdf =)
@0xOverflow imma leave this here... https://redteamalliance.com/Red%20Team%20Alliance%20Alarm%20Bypass%20(2-day).pdf =)
 @OxOverflow Might depend on what type of alarm it is.
@OxOverflow Might depend on what type of alarm it is.
 Would you be able to point me in the right direction for the term to search for, for probing vibrations from a safe lock, my googling is failing me. And also are there 'cheap' group 1 safe locks i could search for on fleabay?
Would you be able to point me in the right direction for the term to search for, for probing vibrations from a safe lock, my googling is failing me. And also are there 'cheap' group 1 safe locks i could search for on fleabay?
 @anfractuosity when you say "probing" the vibrations... what you mean, specifically? learning how to feel the contact points?
@anfractuosity when you say "probing" the vibrations... what you mean, specifically? learning how to feel the contact points?
 to listen acoustically i mean sorry
to listen acoustically i mean sorry
 search eBay for a LaGard 3330 or an S&G 6700 series. then you may need a mount, etc.
search eBay for a LaGard 3330 or an S&G 6700 series. then you may need a mount, etc.
 cheers
cheers
 On a related note, do alarm systems come with a back-door code that service techs or law enforcement can use for bypassing? Same question applies to electronic combo locks like the ones on some safes. Talking consumer-grade stuff here.
On a related note, do alarm systems come with a back-door code that service techs or law enforcement can use for bypassing? Same question applies to electronic combo locks like the ones on some safes. Talking consumer-grade stuff here.
 ah... so most safe lock cases are Zamak, not ferrous. I wound up epoxying some small metal plate to some in order to test out the ear amp device i have
ah... so most safe lock cases are Zamak, not ferrous. I wound up epoxying some small metal plate to some in order to test out the ear amp device i have
 @Dan Maloney 4140 is a popular installer code, often left enabled
@Dan Maloney 4140 is a popular installer code, often left enabled
 @Dan Maloney There might be a default manufacturer code that the company never bothered to change on installation.
@Dan Maloney There might be a default manufacturer code that the company never bothered to change on installation.
 What @Deviant Ollam said.
What @Deviant Ollam said.
 also, on many access control gates, 911 or 911# is sometimes in the system for emergency access
also, on many access control gates, 911 or 911# is sometimes in the system for emergency access
![]() Most alarm panels will not accept the dealer/installer code while armed.
Most alarm panels will not accept the dealer/installer code while armed.
 heh, classic 'get into the gated community party' trick
heh, classic 'get into the gated community party' trick
 Which is why I installed my own ;-) Just wondering if there are any undocumented surprises that got slipped in there
Which is why I installed my own ;-) Just wondering if there are any undocumented surprises that got slipped in there
 sorry, i'm a bit confused you mean, you attach a metal plate, and use a microphone + amp? What's the metal for?
sorry, i'm a bit confused you mean, you attach a metal plate, and use a microphone + amp? What's the metal for?
![]() Speaking of default codes. Many safes use 50-25-50 before installation... Also common but less so, 25-50-25 and I've seen 25-50-75 in one case
Speaking of default codes. Many safes use 50-25-50 before installation... Also common but less so, 25-50-25 and I've seen 25-50-75 in one case
 @Eric this is correct... but we've used it when in a building during the daytime to add a new user =)
@Eric this is correct... but we've used it when in a building during the daytime to add a new user =)

 Dan Maloney
Dan Maloney
Discussions
Become a Hackaday.io Member
Create an account to leave a comment. Already have an account? Log In.