First of all, this is a Bluetooth Low Energy device, detected as "L5_TOUCH_RW".
Using NRF Connect app, you can see which service it offers; It has 5.
- Generic Access (contains Device Name, Appearance, Peripheral Preferred Connection Parameter)
- Unknown Service 1 (the characteristic that has the property "READ, WRITE NO RESPONSE" is the NFC tag info this has detected)
- Battery Service (Self-explanatory)
- Device Information (Self-explanatory)
- Unknown Service 2 (contains 4 characteristics, which I assume is its serial number and other information)
My test unit has this information shown on the app:
- L5_TOUCH_RW (device name)
- [576] Generic Keyring (Appearance)
- Everything set to 0 (PPCP)
- Tag's data, which in my case was 00 00 04 a6 41 9a 7b 2b 80
- 108% (Battery Level)
- Realtek BT (Manufacturer Name)
- Model Nbr 1.0 (Model Number)
- RTKBeeHardwareRev1.0 (HW Revision)
- Toytec FW1.0.1 (FW Revision)
- Toytec SW1.0.2 (SW Revision)
- 00 01 02 00 00 03 04 05 (System ID)
- RTKBeeIEEEDatalist (IEEE 11073-20601 Regulatory Certificate)
- 0 (PnP ID)
- ac ab fa 33 37 07 (0xFFD2, Bluetooth device UUID)
- 4c 32 "L2" (0xFFD3)
- 5e 31 "^1" (0xFFD4)
And according to Furui NFC-PM5, the tag's contents are as follows:
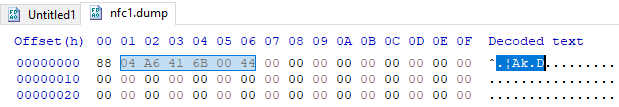
It seems to agree on the first 4 (minus 1) bytes, but then it starts reading something else.
 Torbjörn Lindholm
Torbjörn Lindholm
Discussions
Become a Hackaday.io Member
Create an account to leave a comment. Already have an account? Log In.