Laura can be used in many different scenarios, but it's core purpose is
to provide human to human communication. It can be used for secure
communication in harsh and/or remote areas without (or with poor)
cellular service, can be used to securely exchange files (albeit very
slowly) across long distances, can be used as a paging device, and many
others. In an emergency, it could provide long range local
communication in place of cellular infrastructure. The devices will be
cheap, reasonably robust and have good battery life.
Laura's overall goal is to create a (small) or (large) scale communication network for people to talk to one another. A Laura Gateway can be carried in a bag, suitcase or car, and run for long periods of time on battery. It's range, security, asynchronous nature (being able to leave messages waiting if a node is unavailable), battery life and relative size make it superior to other pop-up forms of portable communication. It could easily sustain itself on a small solar panel, and is also easily compatible with people's existing devices (smartphones, laptops, etc). There should also be less collisions in the 915MHz range than commonly used higher frequencies.
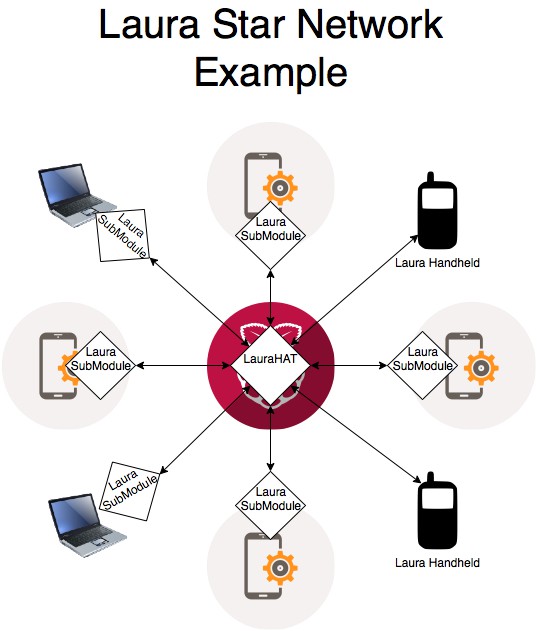
Laura has several network modes. There's Star mode, where a single Gateway services all Nodes that join it. Laura also has an Internet Star mode, where multiple Star networks can link together through the Internet. Want to create your own Laura Carrier? You'd use this. The Gateways can be automatically ganged using the Laura Sync service, or can be manually linked. Then, there's Point to Point Mode, in which (only) two Laura Nodes talk to one another directly, without a Gateway.
Each Node on the network has an individual Secret Key, which protects the other Nodes if a single Node is broken. Encrypted messages have a MAC, Secret Keys are exchanged securely using Public/Private Key Encryption with the Gateway, and all messages contain anti-replay measures (Sync Secret). Every Node has a guaranteed unique serial number, also called it's UUID. It's keys are stored in the extremely secure Atmel ATAES132A Secure EEPROM. The network can be configured as "untrusted", and allow new Nodes to join seamlessly, or "trusted" where Node UUIDs are subject to approval. Message and system security are extremely important in Laura.
The Laura hardware devices are designed so they can serve as an independent Nodes, or be connected to a smarter device (computer, smartphone, etc.) for seamless communication with a Laura network.
There are two different types of Nodes. The SubModule is designed to interface with a smarter device, such as a smartphone. The Smartphone will run a Laura Client for it's platform, which will allow it to send and receive messages from the network (through the SubModule). The SubModule could also be connected to a regular laptop or desktop system, which runs the Laura Client for the same purpose. The SubModule can also be used on it's own. In this mode, the SubModule will only be able to receive messages, and send a canned reply (OK or NOK). The SubModule supports a battery, but does not yet have a battery charger.
The other type of Node is the Handheld. The Handheld is a device with a full keypad, vibration motor, buzzer and screen. The Handheld is designed to be a more phone-like device, with T9-style text input and text messaging features. It supports a battery and has a built-in battery charger.
You can read all about the protocol in the protocol specification document attached to the project! It goes into detail on the important bits and bobs of the protocol.
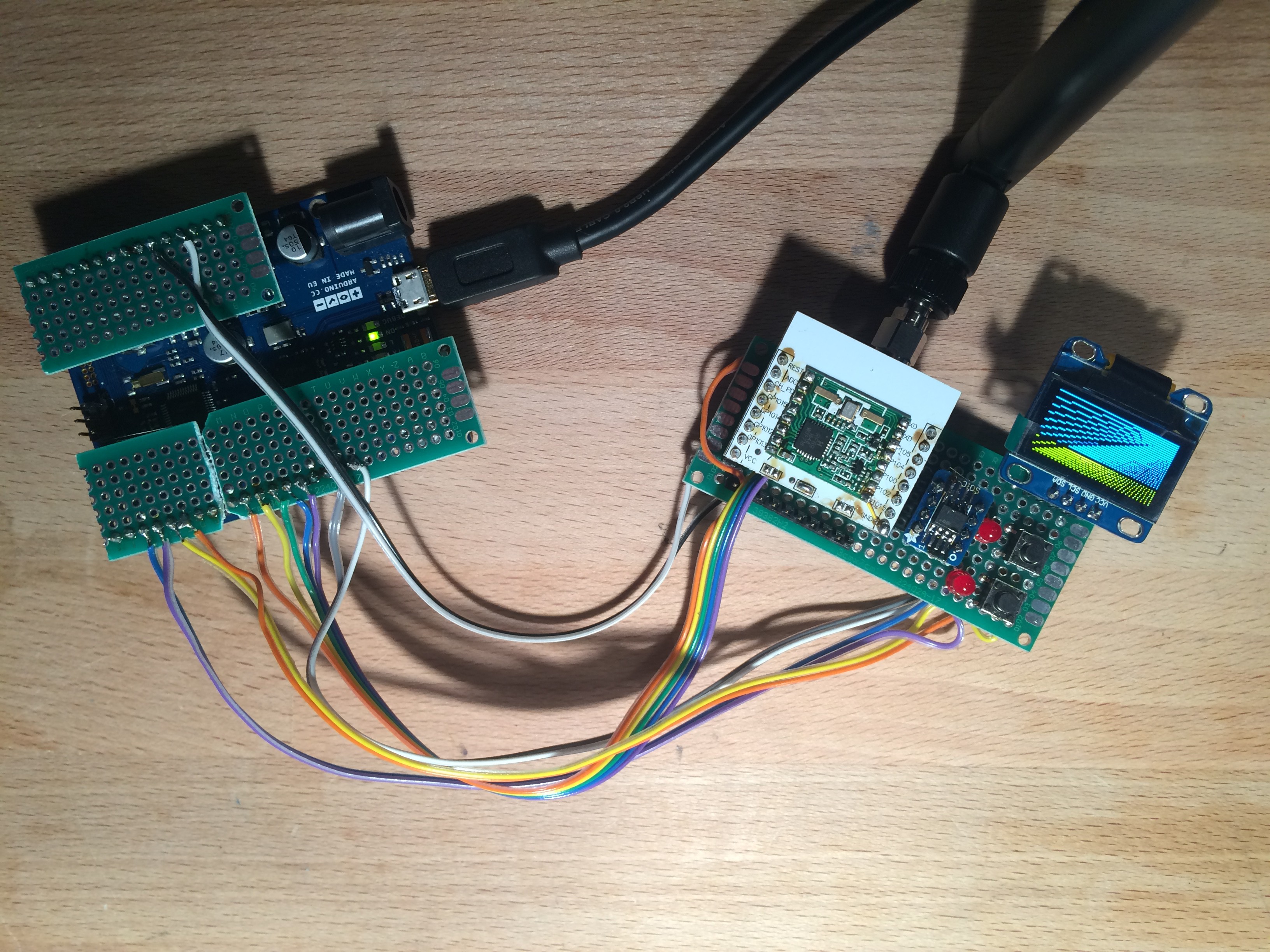
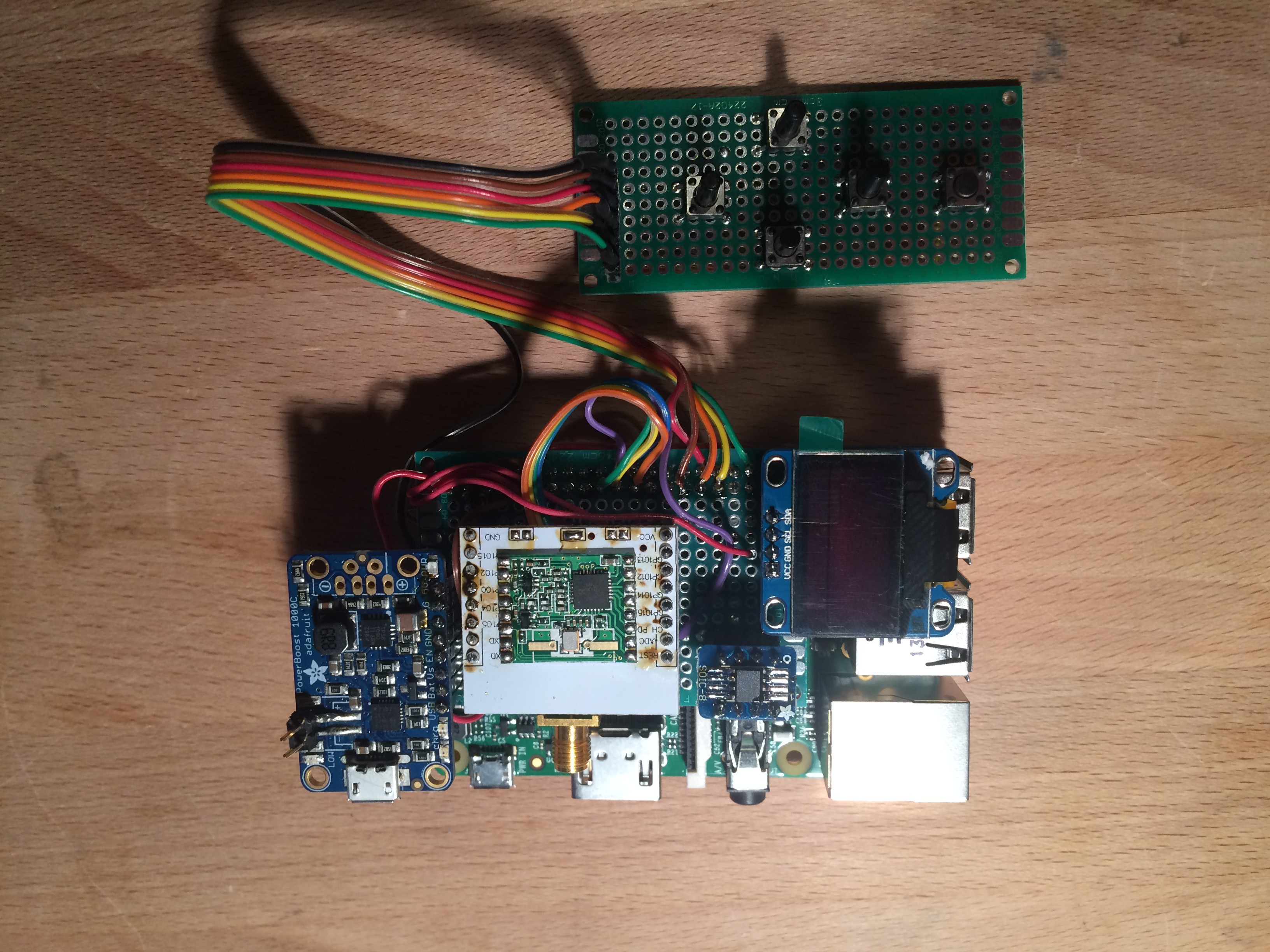
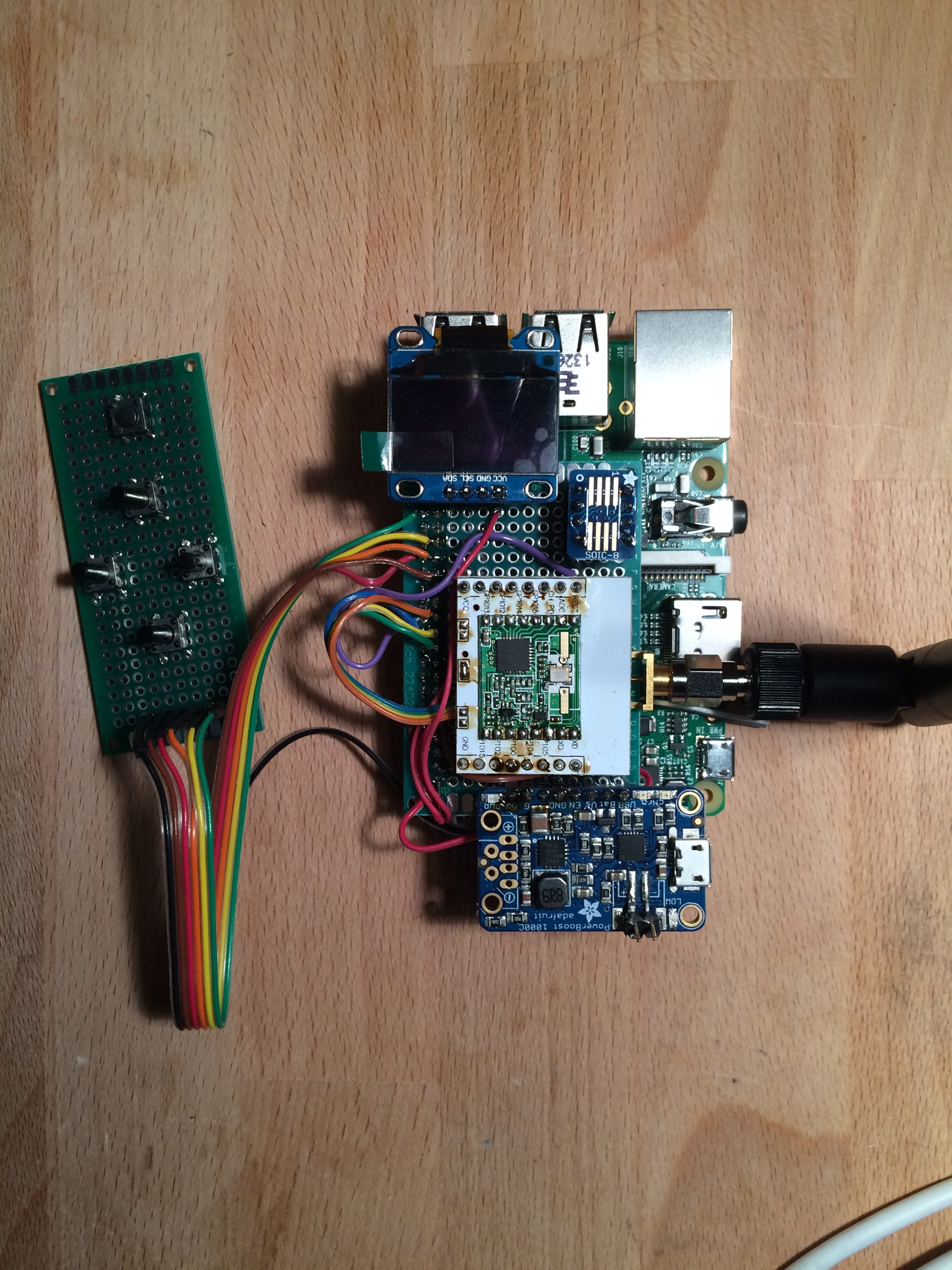
Laura HAT v1.0 (Gateway):
- DS1307 i2C RTC
- LoRa Radio
- 0.96" OLED
- ATAES132A CryptoAuthentication Chip
- 5-Way Joy
- SMA Connector
- (PowerBoost 1000C Connector)
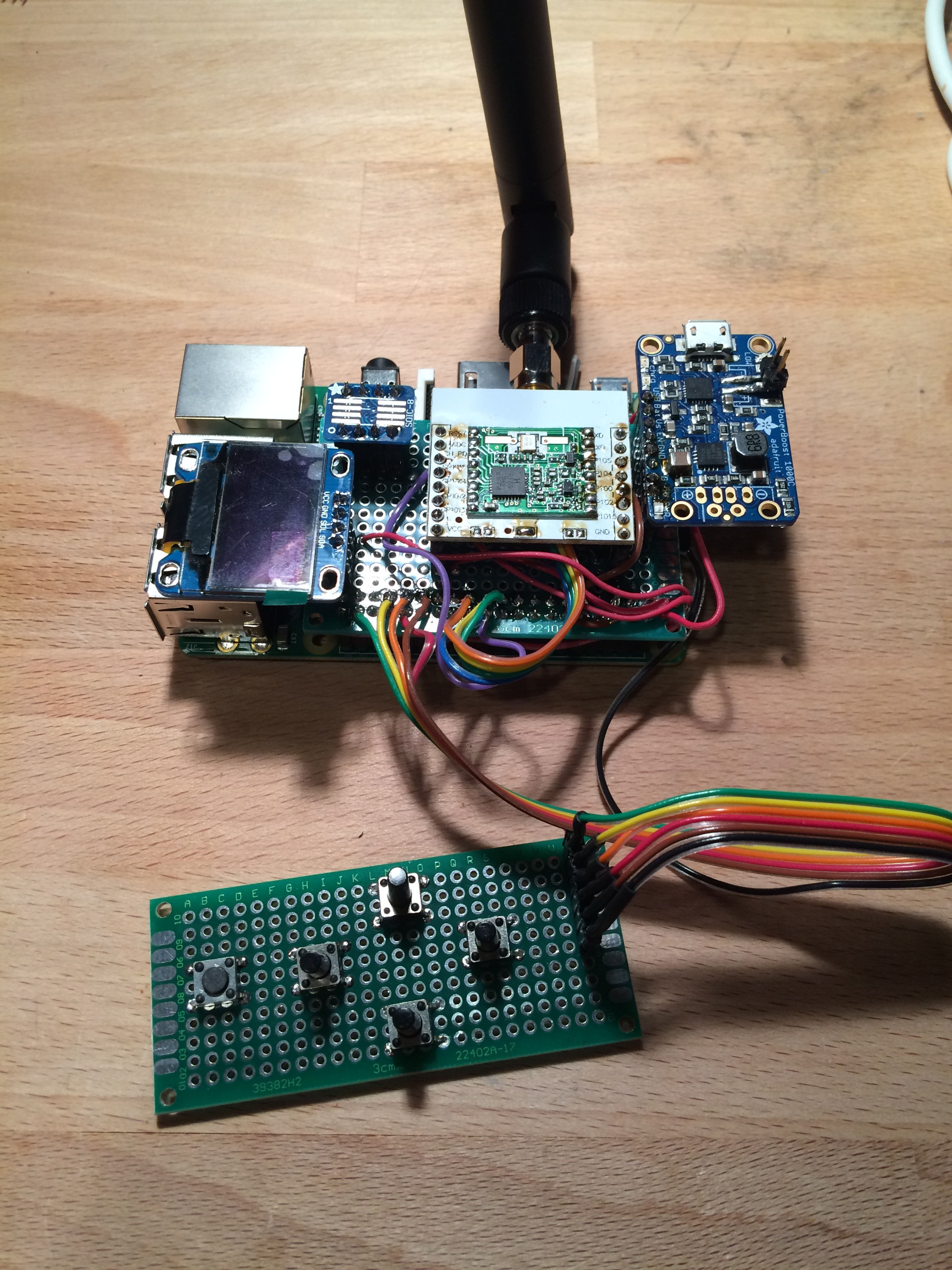
Laura Handheld v1.0 (Node):
- 0.96" OLED
- 12 Button Keypad
- 1 Status LED
- Atmel SAMD21
- Vibration Motor
- Piezo Buzzer
- Atmel ATAES132A CryptoAuthentication Chip
- MCP73871 LiPo Charger
- SMA Connector
- JST LiPo Connector
- 32KHz Crystal for RTC (Built Into SAMD21)
- LoRa Radio...
 Phil Herlihy
Phil Herlihy




 Jonathan Kelly
Jonathan Kelly
 Matias N.
Matias N.
 Mastro Gippo
Mastro Gippo
 Sergio Demian Lerner
Sergio Demian Lerner
please search rnode/reticullum https://reticulum.network/index_pl.html