Hi there,
I thought I would talk a bit about my strategy for testing and verifying the operation of the modules.
Firstly, I have two Moteino R4 boards with RFM69HW radio modules installed on them. By putting these modules into monitor mode (disabling the packet address checks), I can examine the packets that are traversing the network. I will attempt to attack the Nodes using a PC and Moteino, by maliciously crafting packets, attempting replay attacks, and exercising other protocol attack strategies.
I have written up a model for a protocol fuzzer/test suite, which will iterate through the possible transaction scenarios (i.e. Dropped ACK, Transmit failure, ACK receive failure, Out of range, Bad destination, etc...) to exercise all of the paths. It can be run from a Linux system, with a SubModule connected to it (for -> Gateway tests), or straight from the Gateway (for -> Node tests).
It should be possible to detect obnoxious style attacks, such as general packet flood, excessive malformed packets (fuzzing), failed replay attacks, etc. Notifications could be dispatched to a particular Node when these events occur. There's an absolute limit to the power available on the Nodes, so the network will always be somewhat vulnerable to DoS style attacks. But, these attacks will be included in the testing, regardless.
I also have an RTL-SDR setup that I can use for light RF analysis and deep packet decoding, if need be. For the time being, I don't think I will need this level of inspection. This will help when I perform absolute range tests.
 Phil Herlihy
Phil Herlihy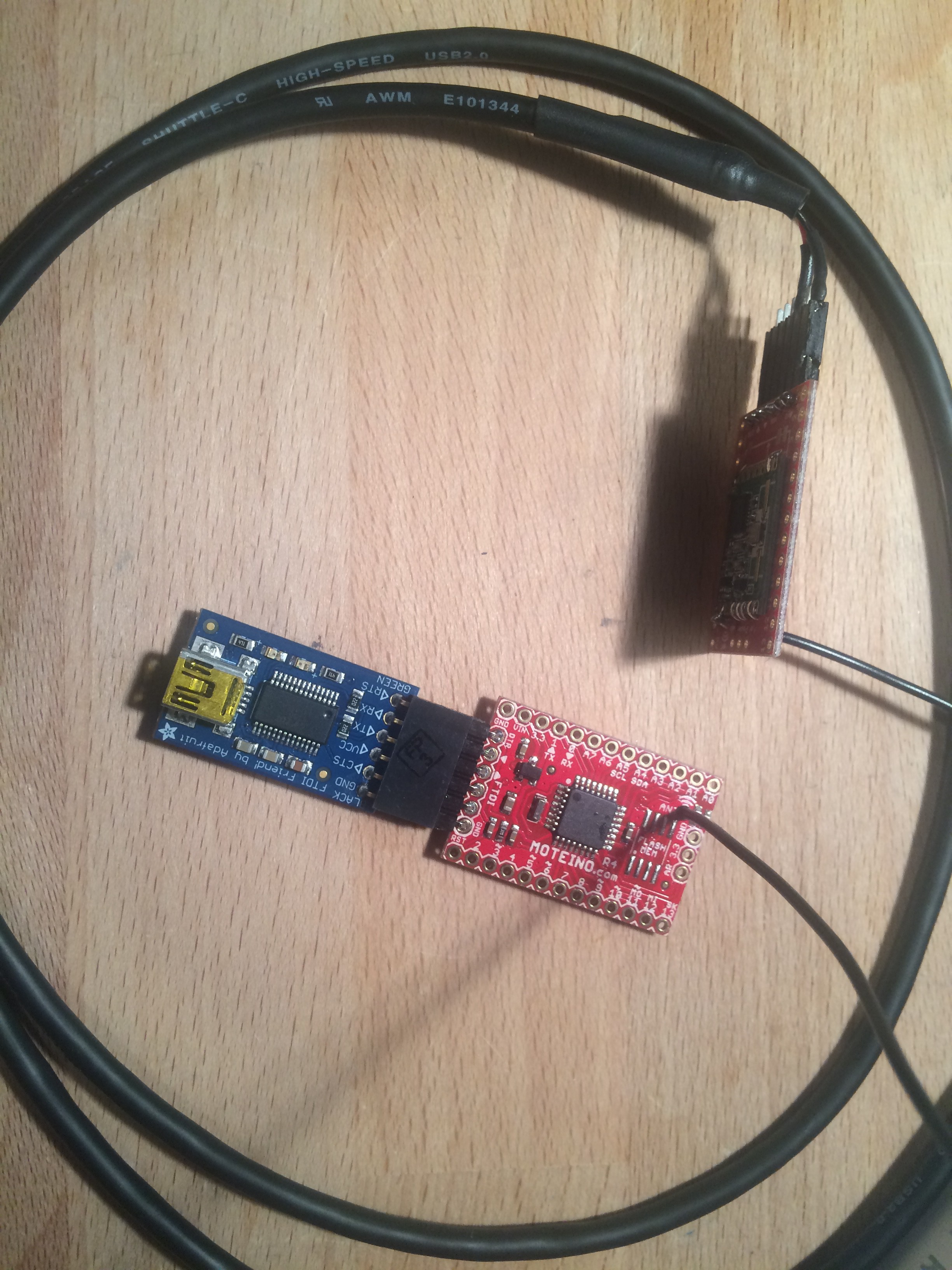
Discussions
Become a Hackaday.io Member
Create an account to leave a comment. Already have an account? Log In.