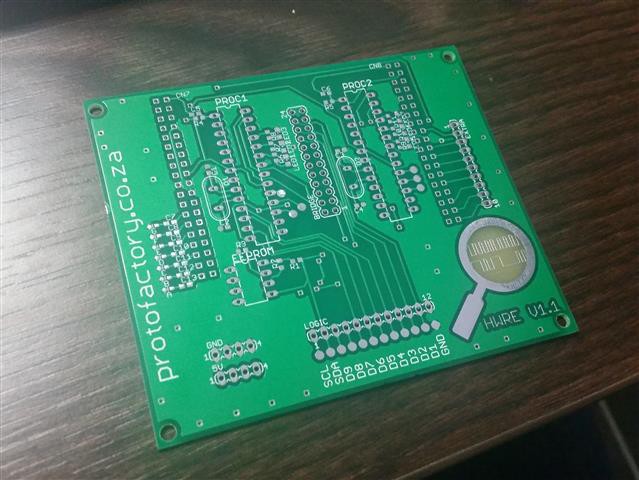
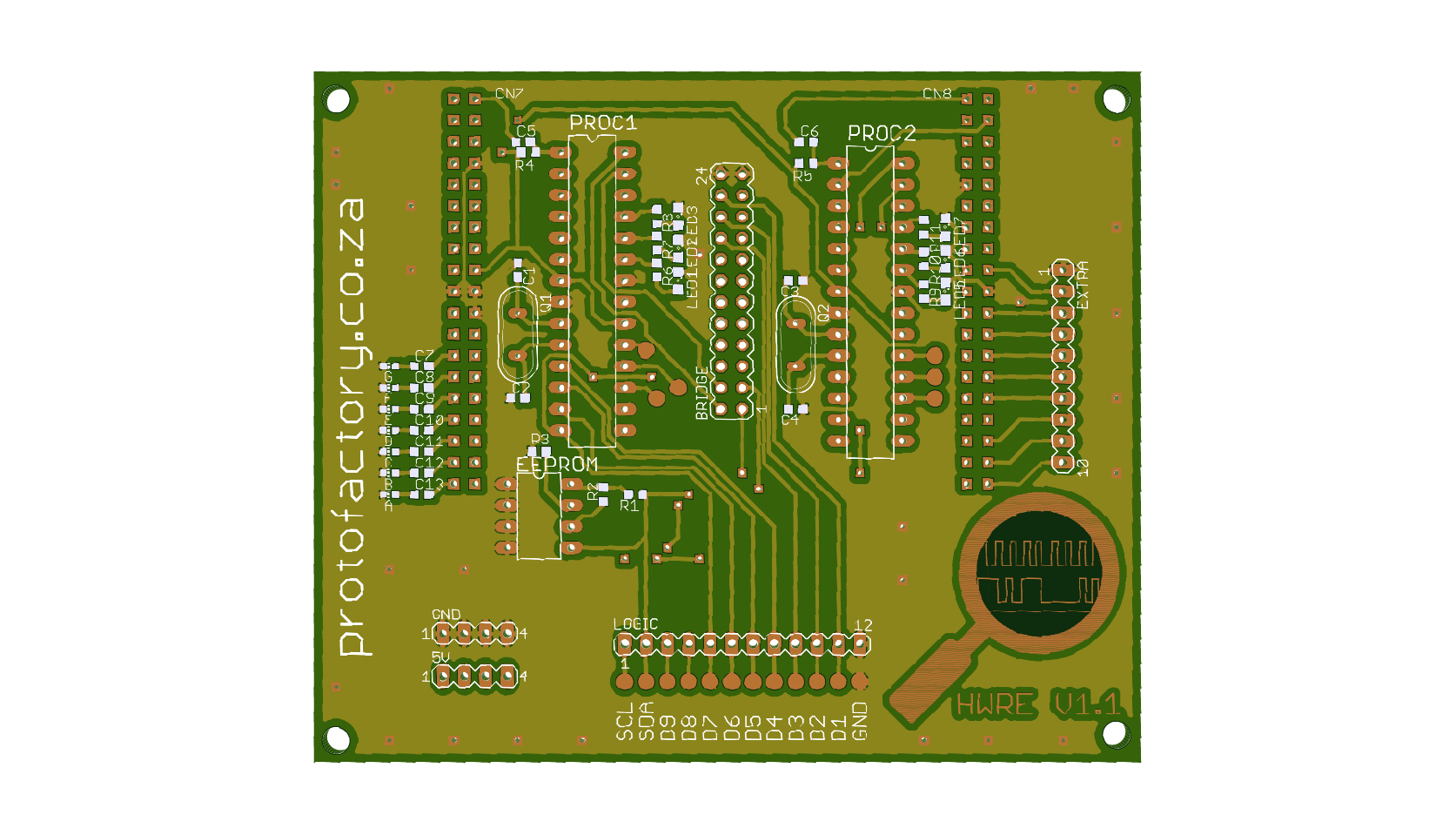
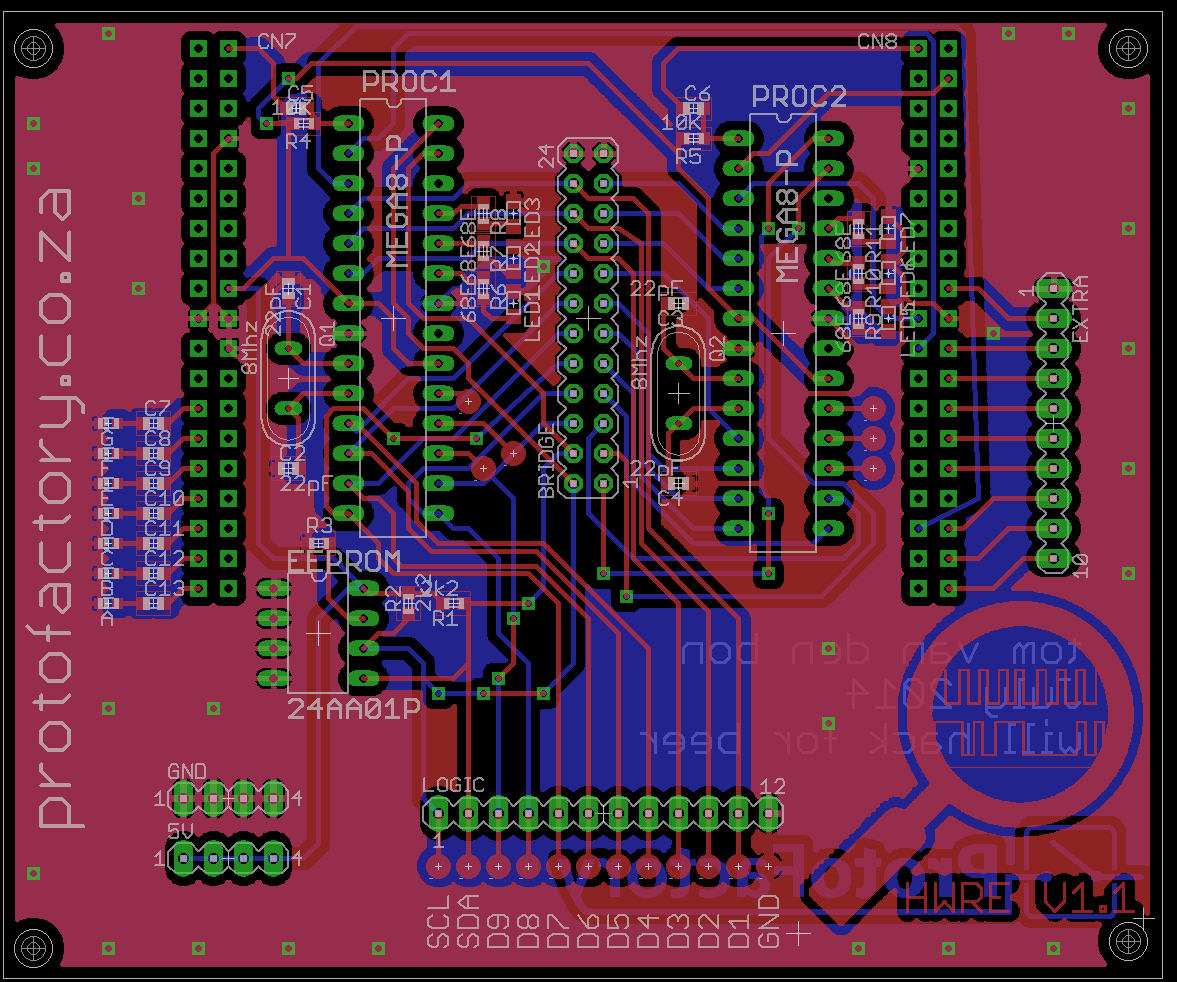
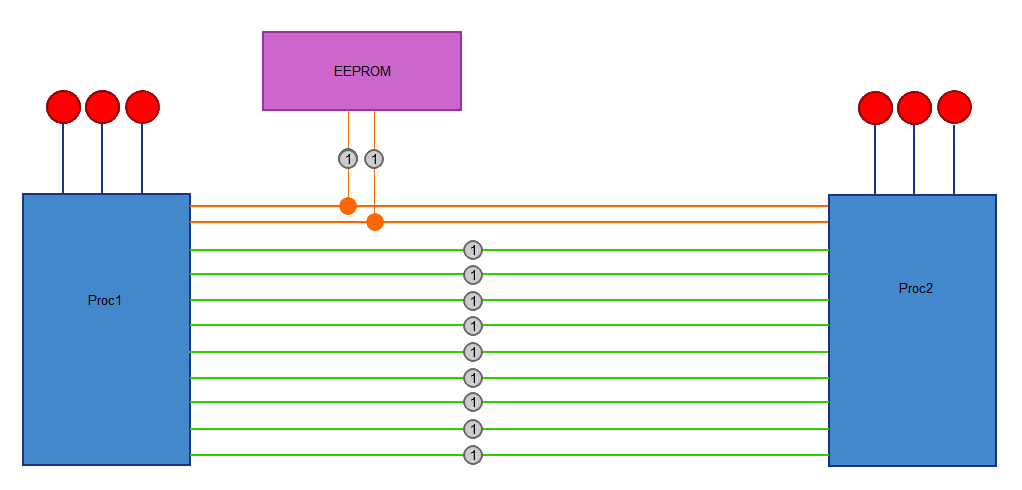
The hardware reverse engineering platform is basically a shield for the new stm32 nucleo boards using the st-morpho connectors. It contains two arduino compatible microcontrollers and an eeprom. There are 9 data lines connected between the two microcontrollers and there is also i2c lines connecting the mcu's with an eeprom. The nucleo board handles loading the reverse engineering scenario on the shield (firmware on the avr's and data on the eeprom).
Design Overview
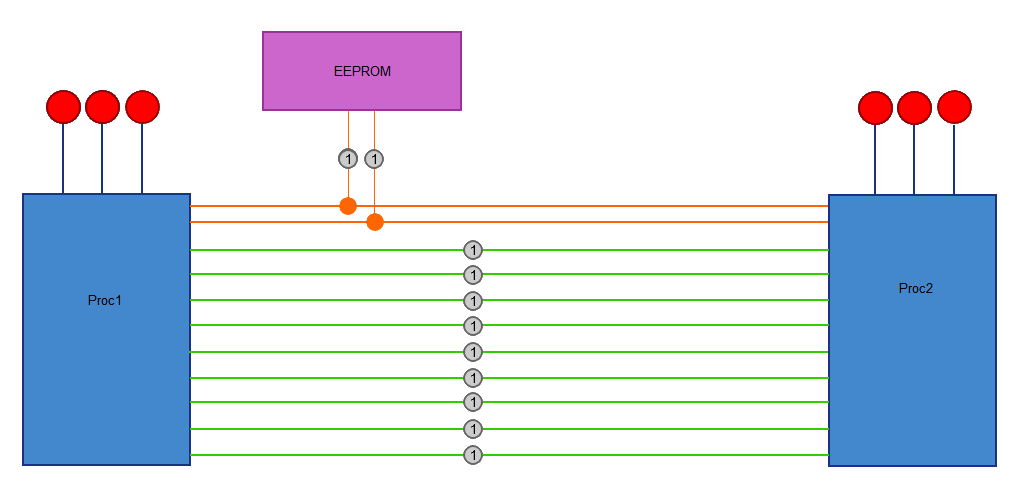
This allows anyone to easily create firmware that depicts a possible RE situation. For example the two mcu's can communicate with each other using a certain protocol.
Test pins are added on all the data lines for connection to RE tools. There are also jumpers for breaking connecting between the two mcu's or to connect your own tools for inserting data to 'crack' the scenario.
Arduino was chosen for the target mcu's because anyone needs to be able to create new RE scenario's without having to spend too much time getting the hardware to work. It's all about the reverse engineering and not firmware development.
The nucleo shield handles the setup of each RE scenario, basically on the pc side it will accept the firmware files and setup the avr mcu's with the new code for reverse engineering.
So it's re-usable for different scenario's and slow enough to use cheap tools :)
For updates you can also join the mailinglist.
 Tom Van den Bon
Tom Van den Bon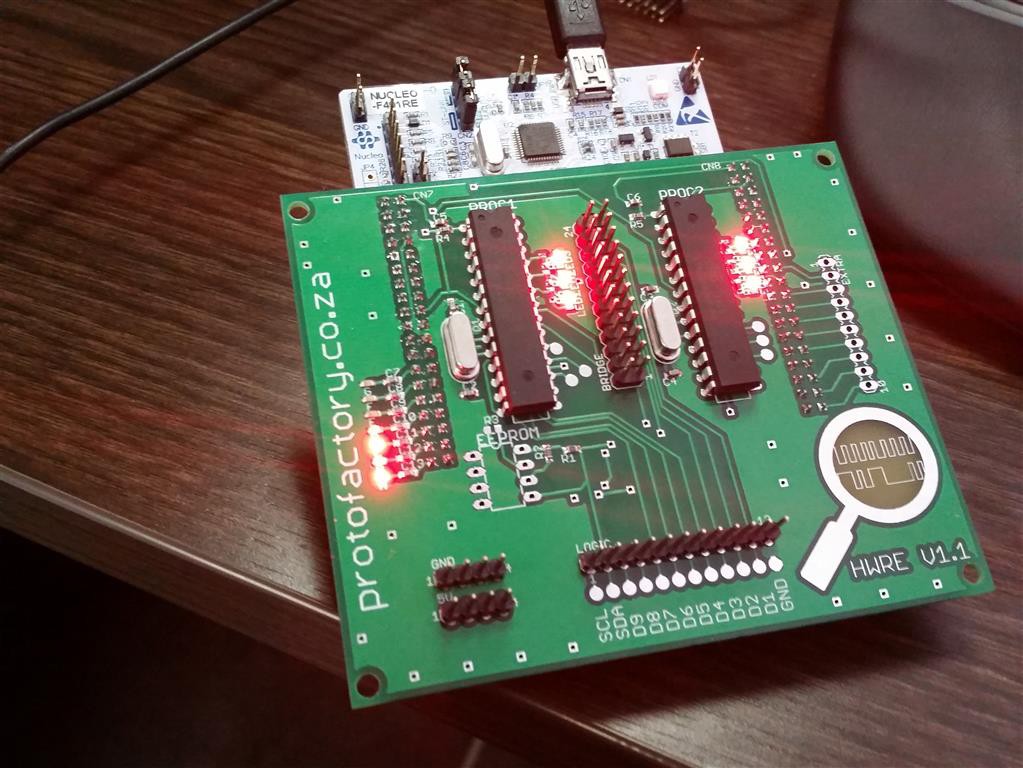




 Arya
Arya

 Denver
Denver
 jlbrian7
jlbrian7
If I look in the Eagle PCB design you posted I can see one OVERLAP!