-
Prototype board
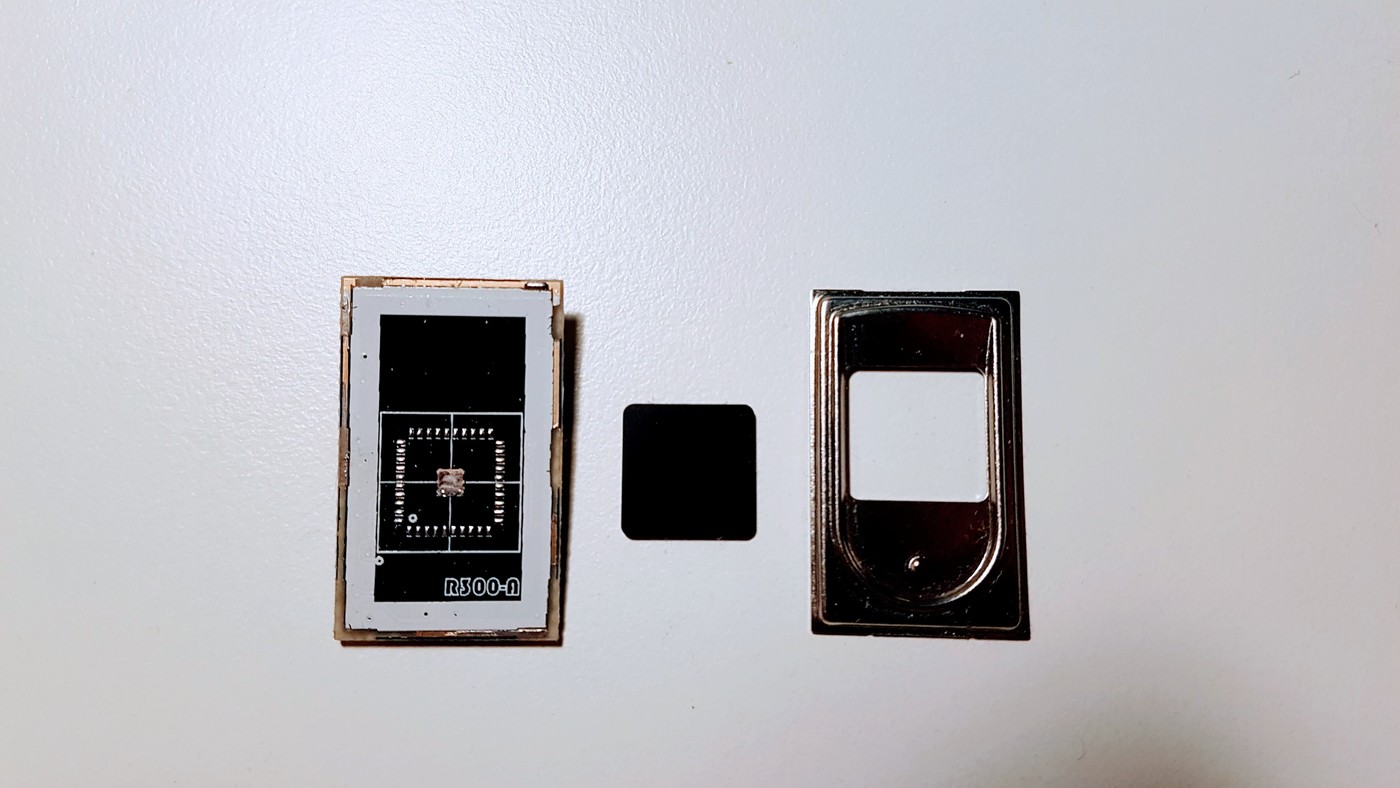
10/14/2019 at 19:39 • 0 commentsIt is sad, but not everything went smooth during my experiments with fingerprint scanners. I have desoldered fingerprint scanner from the GROW R300 device wanting to find a way to connect it to the MCU directly.
![]()
Unfortunately the pad arrangement on the bottom side does not match any of the scanner datasheets I have found so far. And at the moment I have no idea how to connect it. Definitely I will continue my searches but I guess purchasing scanner of other kind will be a much better idea.
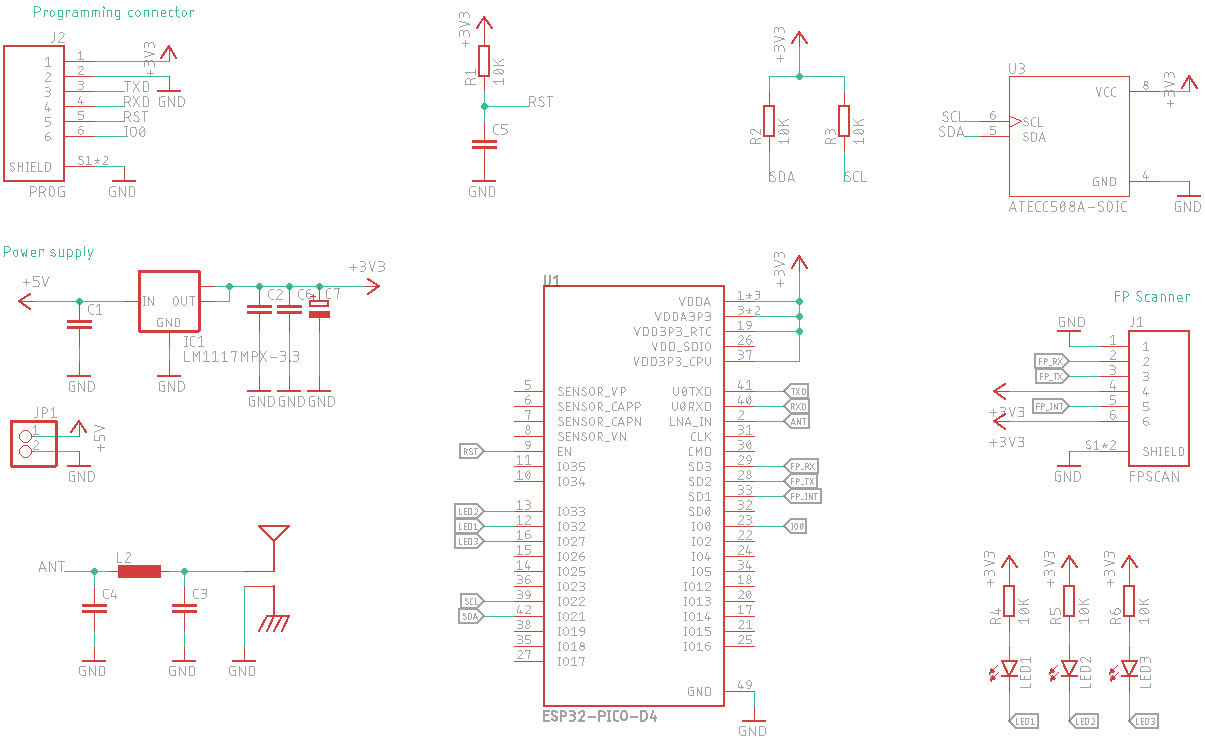
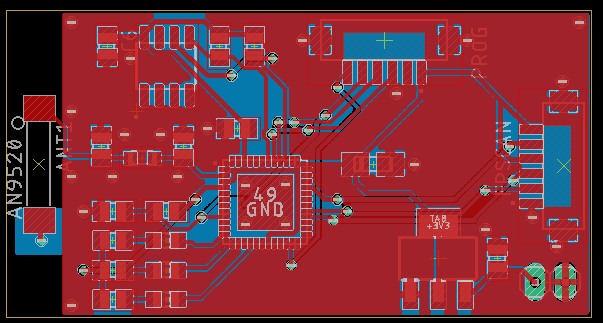
On the other hand I have decided to make custom development board for the authenticator device. It will feature ESP32 Pico D4 microcontroller, ATECC508a security chip, few LEDs and connectors for programming and connecting UART fingerprint scanner.
![]()
The design is not ideal but as a first step towards making my own authenticator it should be enough. I am going to improve it step by step until I have working device.
![]()
So, the boards and chips are ordered and I’m waiting for the delivery.
-
User Verification Problem
09/30/2019 at 14:59 • 0 commentsWhile working on ESP32 based Authenticator device I came into an interesting problem - User Verification. At the moment it is implemented really simple - just a button connected to the IO0 port. However, anybody is able to push this button and therefore authenticate with the device. Then I came to idea of adding some biometric authentication for the user.
I have ordered two fingerprint sensor modules capable to perform the user validation.
First one is GROW R300:
![GROW R300 Fingerprint Scanner]()
Second one is FPC1020:
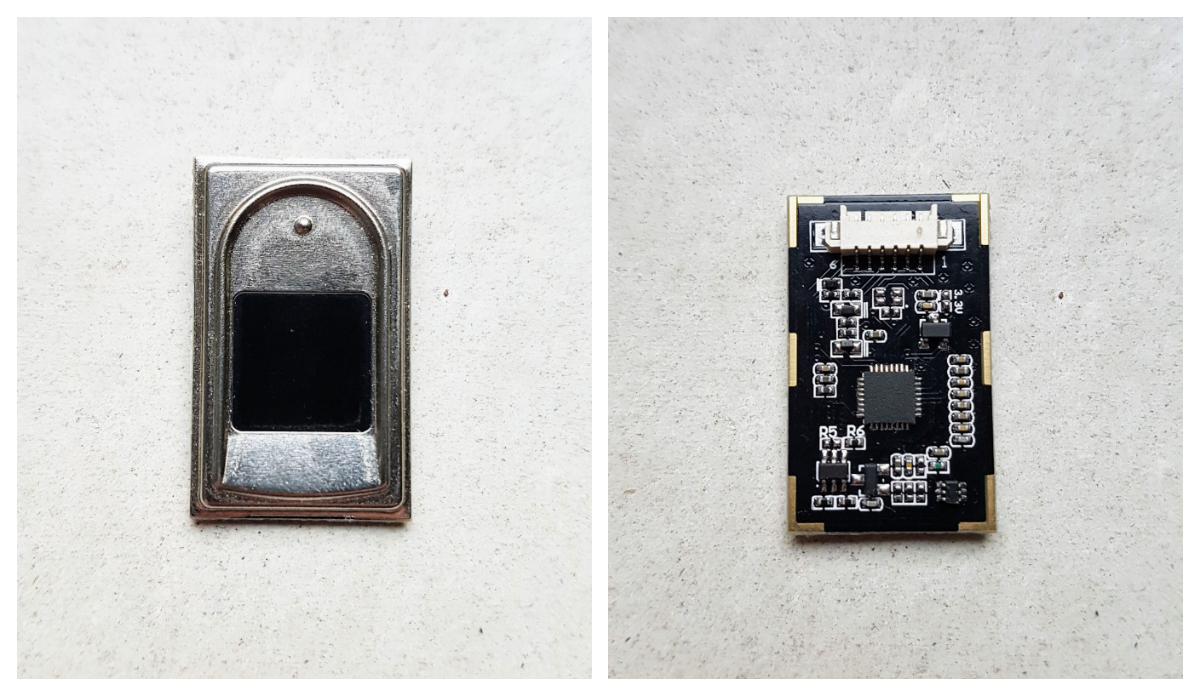
![FPC1020 Fingerprint Scanner]()
Both modules operate at 5V, have UART interface to communicate and their price including delivery is around 12€. Modules have STM32 MCUs on board to implement all required operations from storing fingerprint data to authenticate users.
What I like about these modules is that it’s relatively easy to add user verification procedure to my project. What I dislike is that simple Arduino based sketch can simulate fingerprint scanner like this and become an easy way to hacking security of the device - one can just replace the scanner module with this Arduino device.
However, R300 module seems to provide way to transfer scanned finger image to the MCU. It closes the security issue, but means need of writing own fingerprint recognition and matching algorithm. But then I do not need the MCU located at the module itself, all I need is the actual fingerprint scanner to scan and process images.
So, at the moment my plan is - try to implement fingerprint scanning with R300 module and try to find algorithm for authentication and validation. If I succeed I plan to desolder fingerprint scanner from the module board and try to communicate it directly, without MCU in between.
-
Working prototype
09/16/2019 at 10:19 • 0 commentsFinally I have managed to make ESP32 development board to work as FIDO2 Authenticator device. I have trimmed a lot of functionality to achieve this. For example, I have implemented only one credential which is stored in volatile memory. User validation and presence is implemented as click with single button.
Nevertheless, I was able to pass both "Make Credential" and "Get Assertion" procedures on https://webauthn.bin.coffee/ webpage.
So, so far I have almost all required pieces to continue with the build of personal Authenticator device.
-
Next boring update
08/19/2019 at 08:45 • 0 commentsDuring last two weeks I continued to work on ESP32 part of this project. I needed to figure out how notification system works internally (could not make it work properly) and has to check the source code of the Arduino BLE library. In fact it's a very thin wrapper around functions provided by ESP IDF framework and I have tried to run some examples from there. Worked really good and I have rewritten the whole project without Arduino framework. The footprint of the application became 30% smaller with the same functionality.
So, at the moment ESP32 advertises itself as FIDO2 device, handles BLE connection and receives commands from the browser. I was able to process GetInfo command and respond with device's capabilities.
Next step would be to process MakeCredential command and create new credential for the user. It's more complex and I assume it'll take few weeks to complete.
-
(Bi)Weekly Update
08/05/2019 at 09:49 • 0 commentsLast (and previous) weekends I've spend on real implementation of FIDO2 WebAuthN protocol. In reality the problem is more deep and difficult than I was thinking before, so I have re-implemented the GATT server on Android to have higher level language and libraries and better debugging capabilities.
At the moment I have fully working "Make Credential" workflow with proper certificate generation and response signing.
Meanwhile I have found two interesting glitches in google's implementation of FIDO2.
First one is more likely not accurate protocol definition. In the authenticatorMakeCredential section in response definition we have parameters authData and fmt with respective map indexes (0x01) and (0x02). In reality Chrome requires response with these parameters swapped - fmt parameter should have index 0x01 and authData paramter should have index 0x02. Hopefully the documentation and implementation will be more consistent in the future.
Second glitch is related to the user's interface and you clearly can see it in the video. When communication with Authenticator is about to start Chrome displays dialog window asking which authenticator device should be used. But in the background the communication with paired device is already performed. So, the user interface is totally misleading. The user has no clue they already have to open the Authenticator device and perform all necessary steps with it. But this is question to the Chrome dev team how to improve the interface.
-
Weekly update
07/22/2019 at 08:27 • 0 commentsLast weekend I could play a bit more with the ESP32 board to implement BLE transport for FIDO2 WebAuthN protocol. The great BLE library https://github.com/nkolban/ESP32_BLE_Arduino helped me a lot. Now my developer board advertises itself as Authenticator and provides four required endpoint to communicate. Google Chrome is able to detect the device and tries to connect to it. However, the endpoints just do nothing at the moment and authentication fails with error.
As well I have discovered a great chip for Secure Authentication - ATECC508A. From the datasheet details looks like it could provide all the necessary security procedures and store 16 user keys.
I'm thinking if 16 keys is enough or not. From my perspective it's quite a decent amount - user can use secure authenticator device to login to major and most important accounts like Google or Github and use them as OAuth provider later. If not - ESP32 board has 4Mb flash memory onboard which can be used to store more keys but not as secure.
-
Starting the project
07/18/2019 at 10:01 • 0 commentsI am working with web authentication at work and recently I have started to play with ESP32 development board. The device has Bluetooth Low Energy (BLE) feature which is supported by FIDO2 WebAuthN specification as communication protocol. Now I'm curious if one can build secure web authentication device.
FIDO2 Web Authentication specification is available here.
From my understanding I need to implement two information profiles - 'Device Information' and 'FIDO2'. The great tutorial how to implement BLE server can be found here. Following this tutorial I could make ESP32 visible through Bluetooth connection and expose device information.
The next steps should be FIDO2 implementation.
URU Key
URU Key - a biometric FIDO2 Authenticator built with ESP32 / ATECC508A / FPC1020
 Andrey Ovcharov
Andrey Ovcharov