Before we start, I did some research on Amazon FreeRTOS and how Amazon IoT/MQTT works
- https://www.embedded.com/a-peek-inside-amazon-freertos-publishing-messages-to-the-cloud/
- https://www.hivemq.com/blog/mqtt-essentials-part-1-introducing-mqtt/
- https://s3.amazonaws.com/awsdfwmeetup/AWS+IoT+Meetup_final.pdf
I previously confirmed that MQTT messages are sent successfully with the demo code. From the AWS website, we can monitor it too:
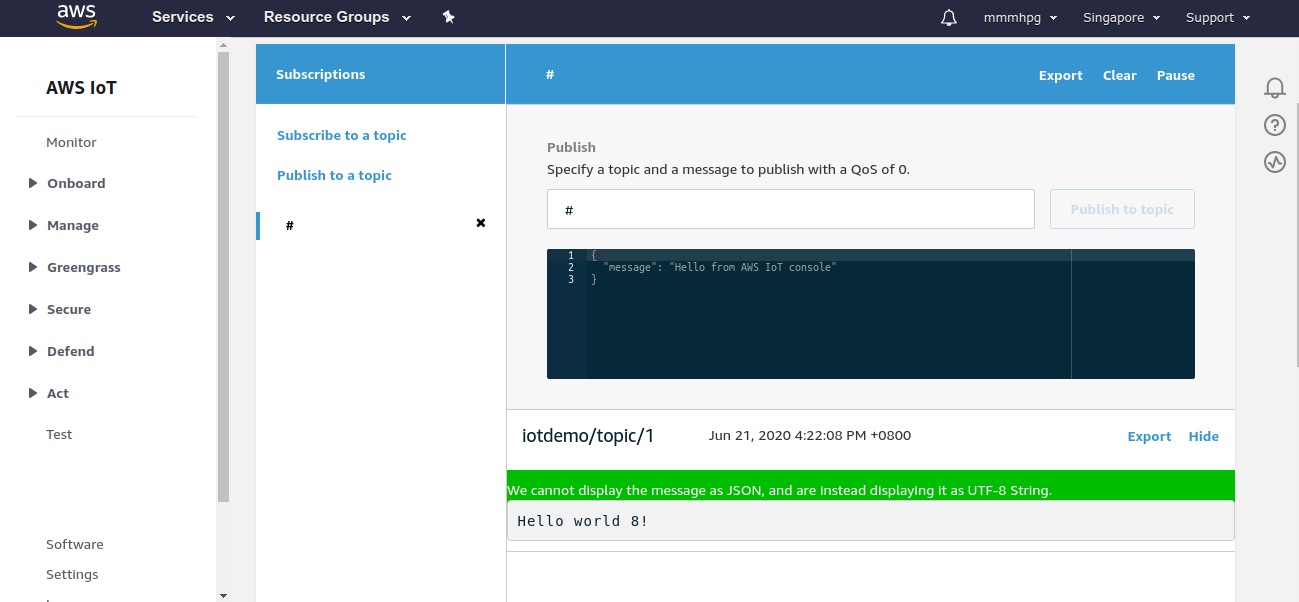
Since my application is to do inventory tracking, I will need to use my IoT device to update a database.
In AWS, I see that I can do this from IoT core -> Lambda -> DynamoDB. I followed this guide.
Connect IoT core to Lambda using IoT Rules.
- https://docs.aws.amazon.com/iot/latest/developerguide/iot-lambda-rule.html
- https://docs.aws.amazon.com/iot/latest/developerguide/iot-rule-actions.html#lambda-rule
- https://docs.aws.amazon.com/lambda/latest/dg/services-iot.html
Go to Act > Rule > Create a rule.
I used this query string SELECT * FROM '#'
Go to Add Action > Send a message to a Lambda function > Create a new Lambda function > Select your function > Create rule.
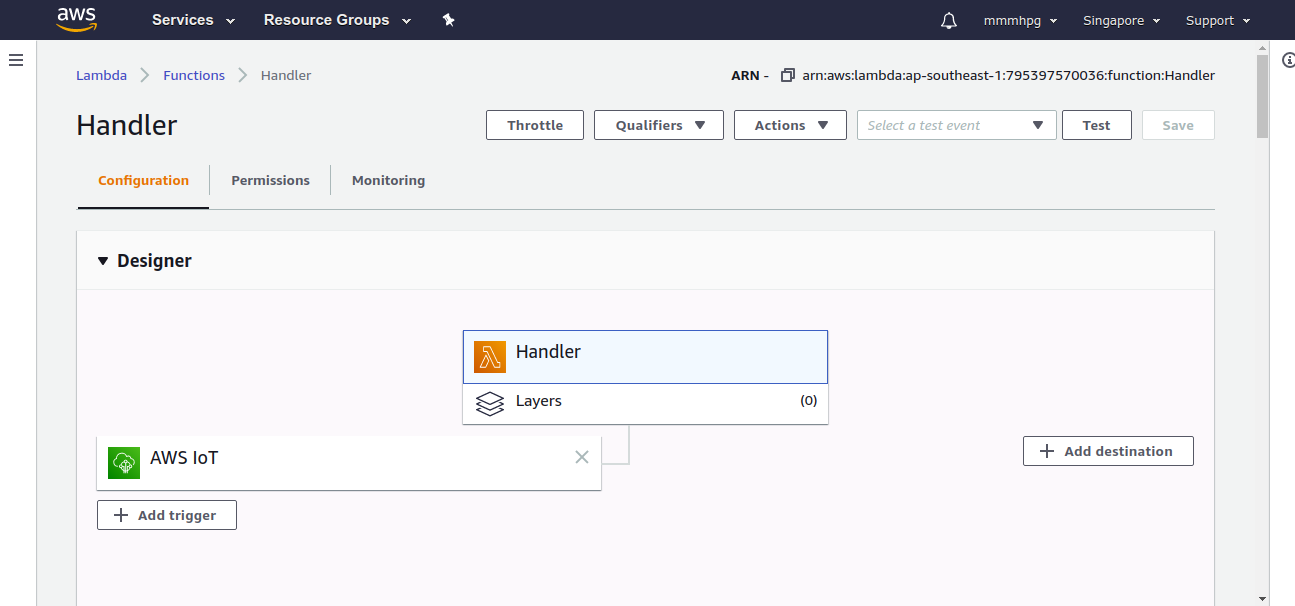
In order for AWS IoT to call a Lambda function, you must configure a policy granting the lambda:InvokeFunction permission to AWS IoT.
- aws lambda add-permission --function-name my-function --statement-id iot-events --action "lambda:InvokeFunction" --principal iotevents.amazonaws.com
But when I run this command I get an error
- An error occurred (AccessDeniedException) when calling the AddPermission operation: User: cypress-psoc is not authorized to perform: lambda:AddPermission on resource:
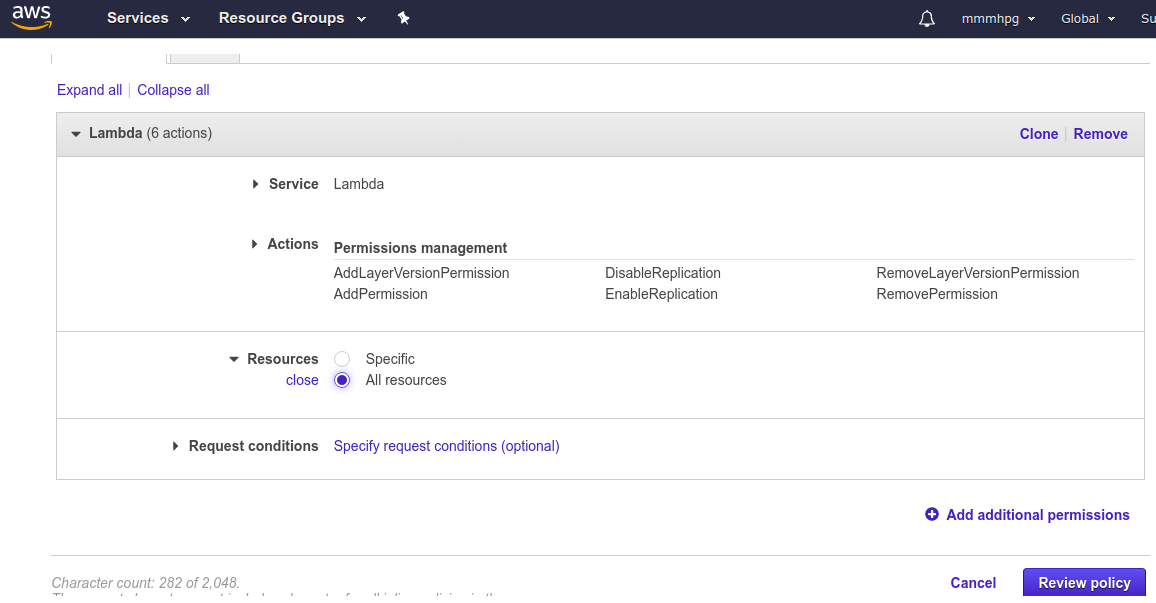
To solve this, find your user in the IAM management console > Permissions > Add inline policies. Use these settings:
- Service: Lambda
- Actions: Permission management
- Resource: all resources
Now when I run the command again, it works.
From lambda, when I used the “Test” button in Lambda, I got another “AccessDeniedException”.
From lambda to dynamodb, we also need to add permissions. I solved this by adding “AmazonDynamoDBFullAccess” permission.
- Attach the IAM policy to an IAM role
- https://aws.amazon.com/blogs/security/how-to-create-an-aws-iam-policy-to-grant-aws-lambda-access-to-an-amazon-dynamodb-table/
Go to your IAM console > Access management > Roles
Find the role for your lambda. When I created mine, I left it as the the default name so it is Handler-role-0cwysi5m.
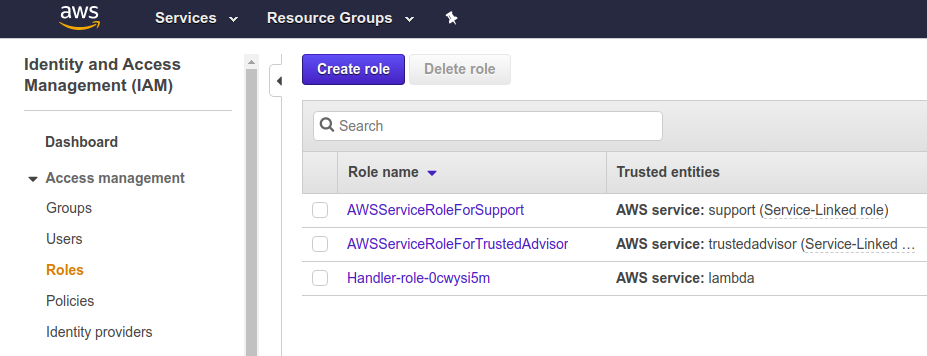
Go to Permissions > Attach policies, and find “AmazonDynamoDBFullAccess”.
After this, I can successfully write to DynamoDB
 zst123
zst123
Discussions
Become a Hackaday.io Member
Create an account to leave a comment. Already have an account? Log In.