You might also want to try MOSH.
- OpenSSH security and hardening
- 5 Linux SSH Security Best Practices to Secure Your Systems
- How To Configure SSH Key-Based Authentication on a Linux Server
Checking SSH key-fingerprints
christoph@christoph-ThinkPad-L580:~$ ssh -o "ProxyCommand nc -X 5 -x 127.0.0.1:9050 %h %p" af66kcmtrfqp6de7wfmfhou5pfrtxqbxtbwpryxl4tuixa5qfe55kkid.onion
The authenticity of host 'af66kcmtrfqp6de7wfmfhou5pfrtxqbxtbwpryxl4tuixa5qfe55kkid.onion (<no hostip for proxy command>)' can't be established.
ECDSA key fingerprint is SHA256:DsYVUlf605cdhz55Anl14mqYHqnV7ZKEcm4O0xyTaOk.
Are you sure you want to continue connecting (yes/no)? yes
You should only type "yes" after verifying the key fingerprint of the host. This can be done by typing the following command on the host side. First check the correct key algorithm and then show its fingerprint.
ubuntu@wandboard:~$ sudo ssh-keygen -l -f /etc/ssh/
moduli ssh_config.d/ ssh_host_ecdsa_key.pub ssh_host_ed25519_key.pub ssh_host_rsa_key.pub sshd_config.d/
ssh_config ssh_host_ecdsa_key ssh_host_ed25519_key ssh_host_rsa_key sshd_config
ubuntu@wandboard:~$ sudo ssh-keygen -l -f /etc/ssh/ssh_host_ecdsa_key
256 SHA256:DsYVUlf605cdhz55Anl14mqYHqnV7ZKEcm4O0xyTaOk root@arm (ECDSA)
Creating SSH-keys
christoph@christoph-ThinkPad-L580:~$ ssh-keygen -b 4096 -t rsa -C "myKey" -f ~/.ssh/sshhs1.rsa
Generating public/private rsa key pair.
Enter passphrase (empty for no passphrase):
Enter same passphrase again:
Your identification has been saved in /home/christoph/.ssh/sshhs1.rsa.
Your public key has been saved in /home/christoph/.ssh/sshhs1.rsa.pub.
The key fingerprint is:
SHA256:dBZqUfK7f4L+U36rc7ZPws+uKCJtUihO7fKrS9V4yKg myKey
The key's randomart image is:
+---[RSA 4096]----+
| o.o |
| = . |
| + + |
| o * o . |
| ..=.S . |
| .o.o.. . .. |
| Eo.o o .. oo .|
| .o + + o.oooB.|
| o=o= o.o+=**O|
+----[SHA256]-----+
Copying SSH-key to the remote server
You should already have a working SSH-connection for that user on that server to do this.
christoph@christoph-ThinkPad-L580:~$ ssh-copy-id -o VerifyHostKeyDNS=no -o User=ubuntu -o CheckHostIP=no -o ProxyCommand="nc -X 5 -x localhost:9050 %h %p" -i ~/.ssh/sshhs1.rsa af66kcmtrfqp6de7wfmfhou5pfrtxqbxtbwpryxl4tuixa5qfe55kkid.onion
/usr/bin/ssh-copy-id: INFO: Source of key(s) to be installed: "/home/christoph/.ssh/sshhs1.rsa.pub"
/usr/bin/ssh-copy-id: INFO: attempting to log in with the new key(s), to filter out any that are already installed
/usr/bin/ssh-copy-id: INFO: 1 key(s) remain to be installed -- if you are prompted now it is to install the new keys
Number of key(s) added: 1
Now try logging into the machine, with: "ssh -o 'VerifyHostKeyDNS=no' -o 'User=ubuntu' -o 'CheckHostIP=no' -o 'ProxyCommand=nc -X 5 -x localhost:9050 %h %p' 'af66kcmtrfqp6de7wfmfhou5pfrtxqbxtbwpryxl4tuixa5qfe55kkid.onion'"
and check to make sure that only the key(s) you wanted were added.
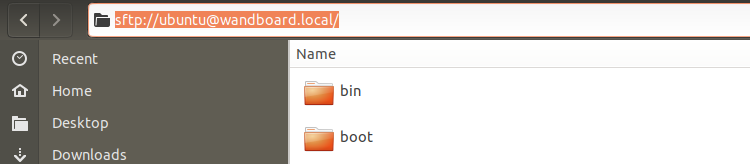
Easy file transfer
There's no need to use scp over the command line.
 Christoph Tack
Christoph Tack
Discussions
Become a Hackaday.io Member
Create an account to leave a comment. Already have an account? Log In.