Continued...
Challenge 4 - Hardware Encoding Morse
A lRg comms tower itz n not powered, a PIGEON_HOLE gap exists whch needs somTIN4 cndctvity. l%kin awA U notic som CLOUDS. c%d DIS b d coz of it aL. d rona?
Description: So when one completes the tool/target combo, the badge lights up and blinks. Fast. REALLY FAST. Some people just recorded it with their phones and slowed it down to watch the pattern. Others...actually read what it said "woah, d bIrb ComplEtd d cIrcuit! a vanilla iCe trak starts playin &lyts r flashin waaa t% fst. nEd 2 lit'rally netflIx & Chill 2 slothngz dwn b4 i git a hedakE" Let's think about this. Blinking fast, need to "chill" and slow things down. Well if one used the MYBASIC editor they would have noticed there was a TEMP.BAS which describes the location of the thermistor temperature sensor on the badge. Guess what happens when you chill the sensor down? It slows the blinkies down. Do that, and you should notice the dot and dash pattern, which is morse encoding. There's also other hints when you look at the clouds "R thOs clouds? problE not, thOs R chem trails.Dey put a hex on U morse so thN U tink." Anyway, decode the morse and this translates to 5GT0W3RZDuH.
...-- ..... ....- --... ..... ....- ...-- ----- ..... --... ...-- ...-- ..... ..--- ..... .- ....- ....- --... ..... ....- ---..
Tool unlock: hack PIGEON_HOLE wit BIRB
Flag: hack flag wit 5GT0W3RZDuH
What Did You Learn Today: That sometimes embedded systems used peripheral sensors for entropy. And if you have access to hardware you can control that entropy. Which lets you control the logic, such as blink speed or encryption keys...
Challenge 5 - HARDWARE Encoding RS232
u c Mt BER cn, sobr thotz :( mAbE U cn cure d rona by putn smTIN inside yo slf.U scratch BUTT whIl tinkiN bout it.
Description: This one is very similar to morse encoding, only we encoded it with good ol' RS232 Serial. Because one should know those serial UART adapter blinkies mean something. More importantly this should teach you about how to interpret reading serial on a logic analyzer. The initial description doesn't help much, but once the tool/target hack is completed (which should be obvious because COVID can be killed by inserting a UV Light in you somehow somewhere) you will be told "Yor gutz lite ^ & blink. Itz supa serial 2 stRt tink bout lEst & mstsigNfict tNgs thN stop, cuz DIS mA b d wrng cure."
 Super Serial? Think about the least and most significant things? C'mon what better hints could we have given you? Now if you've never worked with serial a quick google on how the protocol works will teach you that charachters are turned into binary, it pads a 0 as the start bit, it INVERTS the LSB/MSB order (so its received correctly), then the end is appended with a 1 as the stop bit. The blink pattern shown would translate to...
Super Serial? Think about the least and most significant things? C'mon what better hints could we have given you? Now if you've never worked with serial a quick google on how the protocol works will teach you that charachters are turned into binary, it pads a 0 as the start bit, it INVERTS the LSB/MSB order (so its received correctly), then the end is appended with a 1 as the stop bit. The blink pattern shown would translate to...
0100011001 0011100101 0000100101 0000000101 0001100101 0110011001 0001100101 0100110101 0101011001 0000011001 0111011001
So you remove the start and stop bits, invert the binary, and the result is: 1NH@L3LY507
Tool unlock: hack BUTT wit UVLIGHT
Flag: hack flag wit 1NH@L3LY507
What Did You Learn Today: How serial encoding on hardware actually works.
Challenge 6 - PHREAKING Elevator
U entR a building & wiLCaruana runs awA az U apRch an OpN elvt0r. Yln he hz a:X & dropz a CELL. Thr iz l0kd CALLBOX bElO d flOr btNz.
Description: Good ol' Will Caruana. This gentleman is a curator of shenanigans and a dear friend. So we thought we would team up and simulate some elevator phreaking in the form of a badge CTF challenge. The callbox is locked, so unlocking it..calls for a lock pick. Once you get it open you see "Bt hW u caL? Etchd w wot wz problE a hevE gauge wire U c ZXh0LjQxNzc=" also the other item is the cell which Will drops "Therz only 1 fone # n d recnt caL lst 312d3333372d4d41542d492d4f4245592e2e2e4d6179422064726f7020442059"
Translate those encodings... You get our phone number and extension:
1-337-MAT-I-OBEY...MayB drop D Y
Extension: 4177
Give good old Taco Corp Pharmaceutical, Elevator Right to Repair, bath tub medea vodka, and artisinal organic salsa factory super friendly and sometimes helpful but not always customer service hotline. Enter extension 4177 and you will over hear Will & Hyr0n simulating an elevator phreaking event with the flag at the end. Its like you're actually phreaking an elevator that we are hanging out in (but not..because DEF CON was canceled) He gave a great talk on this and they did a write up in Wired as well.

Tool unlock: hack CALLBOX wit LOCKPICK
Flag: hack flag wit OTIS
What Did You Learn Today: Kinda weird and scary, that elevators can be dialed into and discussions had, by a phone number and extension. That, the phone number is related to the callbox and the extension typically the number on the top of the elevator.
Challenge 7 - WIRELESS POCSAG
A PAYPHONE by a run dwn gas statN. P$ shows -$1337 / gal.WUT?! wiLCaruana again, n he iz runN awA :-d & shooting a laser @ U.
Description: What's better than NPC Will once? Twice. When you hack the target with tool, you learn of a COINBOX on the PAYPHONE. This has an encoding "it hz Bin pryed OpN & NE coins put n faL rght bak out.N bak u C msg: Rm9yIGEgZ29vZCB0aW1lIGNhbGwgZXh0LiAyMzIz" which translates to extension 2323. Same phone number as elevator phreaking (encoded again) in hex. Give it a call with the other extension. You get a message that spells out a bitly link. Go get that link. Its a soundtrack to the pool party, the pool on the roof...wonder who is playing? When you listen, well it's quite the sound. Here's my best advice when dipping your toes into the world of signals. You can visit the Signal Identification Wiki and based on its frequency, down select what it could possibly be, then proceed to demodulate & decode it. You can also grab a phone app called SignalID which assists in identifying signals. So lets say you get past that hurdle and learn its good ol Post Office Code Standardisation Advisory Group (POCSAG). Great! If you are a Windows Person, you could follow this link... But we aren't Windows people that often, we like Penguins. So how could you do this entirely in Linux?
Option 1 EZ CLI Method (Credit 5p0rk):
lappy@386:~$ multimon-ng -s SCOPE -t wav dc28_andnxor_ost.wav > out; grep POCSAG out
Option 2 GQRX Existence is Pain Method (but it gets you understanding how the tool works):
In short, to make the file able to transfer around and not make us go broke with bandwidth charges, we compressed it using a GQRX export. Which means you will have to upsample it. You do this with sox. More importantly, when you do this, its a RAW signal meaning there is no metadata in the file header and GQRX has to read that info based on the structure of the file name. So do the following to upsample the WAV.
$sox dc28_andnxor_ost.wav -e float -t raw -r 1024000 -b 32 -c 2 gqrx_20200806_123456_123456789_1024000_fc.raw
Notice the format is essentially "gqrx_YYYYMMDD_XXXXXX_XXXXXXXXX_BITRATE_fc.raw"
The x's can be anything really its just the structure which matters.
Also note this isnt going to be a tutorial on GQRX in Linux, there are plenty of those. What is important is realizing we are going to load a RAW/IQ file play it back over UDP , pipe that into SOX to downsample it, then pipe it into multimon to decode. Yes, btw, that is very stupid that it has to be upsampled just to get played by GQRX because GQRX CANT EVEN NATIVELY PLAY THE DAMN FILES IT RECORDS WITHOUT EXTERNAL MODIFICATION (pull request incoming)... Anyway, once you have the file loaded and the correct SDR receiver settings for POCSAG in GQRX (-26db squelch, RAW/IQ Mode, Width about 15k), his play and in another command window run the following...
lappy@386:~$ nc -l -u -p 7355 | sox -t raw -esigned-integer -b 16 -r 48000 - -esigned-integer -b 16 -r 22050 -t raw - | multimon-ng -t raw -a POCSAG512 -a POCSAG1200 -a POCSAG2400 -a FLEX -f alpha - | cut -c 52-
And here is what you will hear (i.e. robot sex) and see...
hyr0n@ubuntu:~/dev/sdr$ nc -l -u -p 7355 | sox -t raw -esigned-integer -b 16 -r 48000 - -esigned-integer -b 16 -r 22050 -t raw - | multimon-ng -t raw -a POCSAG512 -a POCSAG1200 -a POCSAG2400 -a FLEX -f alpha - | cut -c 52-
multimon-ng 1.1.8
(C) 1996/1997 by Tom Sailer HB9JNX/AE4WA
(C) 2012-2019 by Elias Oenal
Available demodulators: POCSAG512 POCSAG1200 POCSAG2400 FLEX EAS UFSK1200 CLIPFSK FMSFSK AFSK1200 AFSK2400 AFSK2400_2 AFSK2400_3 HAPN4800 FSK9600 DTMF ZVEI1 ZVEI2 ZVEI3 DZVEI PZVEI EEA EIA CCIR MORSE_CW DUMPCSV X10 SCOPE
00 FLEX
This one's dedicated to all the hackers. Even out settle score quick. My disaster recovery requires even more disks<LF><NUL>
Put your bytes up, prove it or you forfeit. Got my C64 and we blew it into orbit. 1:M. Bison with eight straight perfects<LF>
Overload emotions make hate, break circuits. In case you heard, it's a name fake service. Optimize our runtime to escape verdicts.<LF>
Got an integer scope flow. That they can't sign. Passing code, didn't sanitize. Command lines; land mine<LF>
So before, they'll see me after. I'm Advice dog. Courage Wolf. Plus Philosoraptor. Don't prove we're human unless we really hafta<LF><NUL>
My team built schemes that destroyed recaptcha. Hate what they see, finish this chapter.<LF><NUL><NUL>
By the way we're not any geeks, we hack into NASA.<LF>
Drink all the booze. Hack all the things. Drink all the booze. Hack all the things<LF><NUL><NUL>
Drink all the booze. Hack all the things. Drink all the booze. Hack all the things<LF><NUL><NUL>
Got this Vodka and this Redbull. They still give me wings.<LF><NUL>
Drink all the booze. Hack all the things. Drink all the booze. Hack all the things<LF><NUL><NUL>
Drink all the booze. Hack all the things. Drink all the booze. Hack all the things<LF><NUL><NUL>
Zero through Three. We're in every single ring. I'm just waiting until my blackberry dies<LF><NUL>
Cause I'll replace it with a raspberry pi. Don't compare to this track. It makes everything they said dull<LF><NUL>
Neutralize any threat. Turn Red skull to dev null. They killed virus writers that we mentioned<LF><NUL><NUL>
But instead they ascended to the VXHeavens. To reincarnate as live wires. Still inside we hide ciphers in signed device drivers<LF>
Which school will we hit next? They didn't learn the format. So we've gotta printf. Next step is a chin check<LF><NUL>
Freestyles that I spit best. They didn't decrypt yet. I crush internet MC's in rhyme battles. Get your WiFi tackled<LF><NUL>
Hak5 Pineapple. I don't think you'll like my snapple. Cause I popped it with vodka. And a cyanide capsule<LF><NUL><NUL>
Drink all the booze. Hack all the things. Drink all the booze. Hack all the things<LF><NUL><NUL>
Drink all the booze. Hack all the things. Drink all the booze. Hack all the things<LF><NUL><NUL>
Got this Vodka and this Redbull<LF><NUL><NUL>
They still give me wings<LF>
So we drink all the booze. Hack all the things. Drink all the booze. Hack all the things<LF><NUL><NUL>
Drink all the booze. Hack all the things. Drink all the booze. Hack all the things<LF><NUL><NUL>
First we drink all the booze. Then we hack all the things. Then backdoor the firmware.<LF><NUL>
On anything you bring. Regardless of the hardware, service, or encoding. Connected it to the internet<LF>
And someone's gonna own it. This is for the pirates who clap. And love the sound attacking from the cloud<LF><NUL><NUL>
Then we're back in underground. There's no masking from us now. We pop Tor nodes around the globe<LF><NUL><NUL>
Track and hunt you down. Hacked on schedule, add it to your calendar. Devices online; here comes another challenger<LF><NUL>
State infiltrated, so undercover. This is for my comrades who stare at their debuggers. And trace every buffer<LF>
Examining the code flow. Haven't been to sleep? Better pop another No-Doz. I think I'll need a planet sized urn<LF><NUL><NUL>
Cause some men just wanna see the world burn. Your turn!<LF>
Drink all the booze. Hack all the things. Drink all the booze. Hack all the things<LF><NUL><NUL>
Drink all the booze. Hack all the things. Drink all the booze. Hack all the things<LF><NUL><NUL>
Got this zodka and this Redbull. They still give me wings<LF><NUL><NUL>
So we drink all the booze. Hack all the things. Drink all the booze. Hack all the things<LF><NUL><NUL>
Drink all the booze. Hack all the things. Zero through three. We're in every single ring<LF><NUL><NUL>
FLAG: DUALCORE<LF><NUL><NUL>
TBH We were really sad about not being able to bring this to DEF CON. Hyr0n studied to get his HAM tech, coordinate, and setup a POCSAG beacon for DC28 just so we could broadcast Hack All The Things for a wireless challenge. At least you got a recording to hack on.
Tool unlock: hack PAYPHONE wit QUARTER
Flag: hack flag wit DUALCORE
What Did You Learn Today: POCSAG (pager protocol) while old, is still heavily in use and can be monitored in the clear with a $15 software define radio. What still uses POCSAG you ask? Those vibrating pick up your food pucks at restaurants. Oh and hospitals. Yep, many hospitals use POCSAG as a backup for their internal messaging system and unfortunately transmit patients private health information IN THE CLEAR. Which is a HIPAA violation (you cant even send that info via text message). If you ever come across this in the spectrum, responsibly report the hospital to HIPAA for their negligent handling of patient information.
Challenge 8 - PASSWORD CRACKING NTLM
Pon d flOr ther sits a glitter covered tink pad frm TyMkrs.Itz old, runN win 2000, & evN hz an IOMEGA_DRIVE.
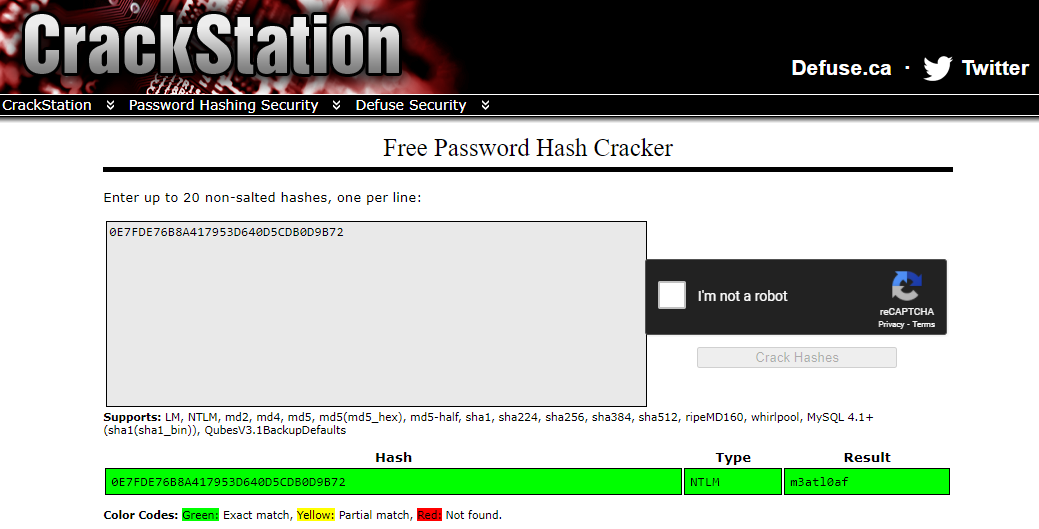
Description: This challenge refernces a damn drop box we got from the TyMkrs, an old computer, and the fact that you need to hack its password. The lesson here is that older OS's, like Win 2k, used NTLM as its password base. How do you get that hint? When performing the tool/target hack, it is revealed "W a solid clik d disk snaps in2 plAc.Un4tuN8ly d files R credential locked by d win SAM." Doing some research on Windows 2000 and SAM -> NTLM based encryption. "Navigating 2 d win SYS thirty two config SAM U find: 0E7FDE76B8A417953D640D5CDB0D9B72" Go use your favorite NTLM password cracker, and you will get the flag.
Tool unlock: hack IOMEGA_DRIVE wit ZIP_DISK
Answer: hack flag wit m3atl0af
What Did You Learn Today: A lot of computers out there are not running the latest and greatest operating systems. In fact many of our Win 2000/XP era PCs are still in the wild. If you find one the Security Account Manager (SAM) is located at %SystemRoot%/system32/config/SAM and it will have NTLM encryption. Which can be cracked faster than Matt Damon giving you a wink.
Challenge 9 - CRYPTO/ENCODING Slackbot
Theres a robotic HED on d ground, bt it iz lacking d milliamps.FAC & reminds of U of pure annoyance.
Description: Lets face it we all hate slackbot. But we don't believe anyone has ever roped in that bastard to a CTF puzzle with its creeper responses. So there's a first right? There are plenty of hints once you perform the tool/target hack, such as ""U cn ask me simpl questions bout how Slack works,o jst typ a few keywords lIk "m355@g3" bt TLK 2yorself so others lIk guvment dun knO"" and "Blu grEn red yeLo w two eyes som brows & wot d fuk iz dat a nose o mouth?!" So go hop in our public slack, and not to ruin it for other, but start a DM with yourself (where slackbot will reply). This leads to a chain of events based on its responses. Here's a screenshot of the Slackbot canned responses:
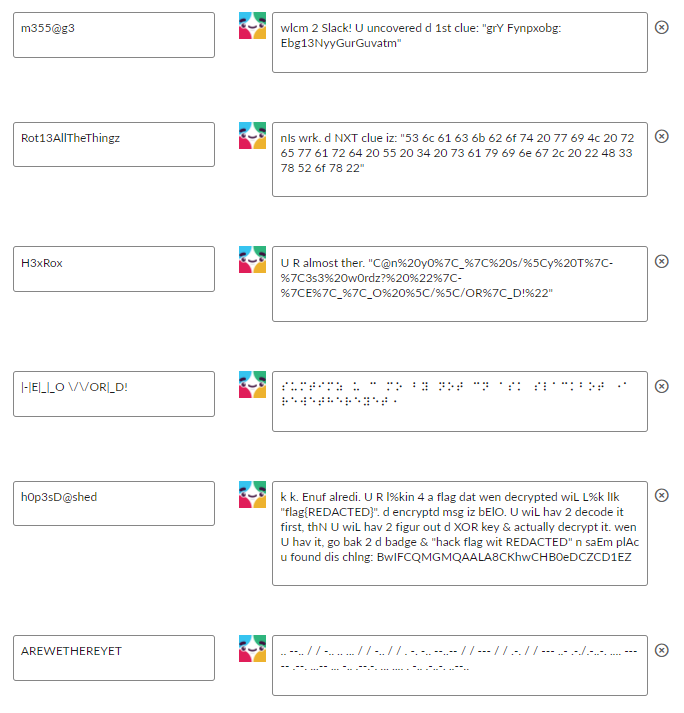
- m355@g3 -> grY Fynpxobg: Ebg13NyyGurGuvatm -> ROT13 -> teL Slackbot: Rot13AllTheThingz
- Rot13AllTheThingz -> 53 6c 61 63 6b 62 6f 74 20 77 69 4c 20 72 65 77 61 72 64 20 55 20 34 20 73 61 79 69 6e 67 2c 20 22 48 33 78 52 6f 78 22 -> HEX 2 ASCII -> Slackbot wiL reward U 4 saying, "H3xRox"
- H3xRox -> C@n%20y0%7C_%7C%20s/%5Cy%20T%7C-%7C3s3%20w0rdz?%20%22%7C-%7CE%7C_%7C_O%20%5C/%5C/OR%7C_D!%22 -> URL Decode -> C@n y0|_| s/\y T|-|3s3 w0rdz? "|-|E|_|_O \/\/OR|_D!"
- |-|E|_|_O \/\/OR|_D! -> ⠎⠥⠍⠞⠊⠍⠵⠀⠥⠀⠉⠀⠍⠕⠀⠃⠽⠀⠝⠕⠞⠀⠉⠝⠀⠁⠎⠅⠀⠎⠇⠁⠉⠅⠃⠕⠞⠀⠐⠁⠗⠑⠺⠑⠞⠓⠑⠗⠑⠽⠑⠞⠐ -> Brail Decode -> sumtimz u c mo by not cn ask slackbot ⠐arewethereyet⠐
- AREWETHEREYET -> .. --.. / / -.. .. ... / / -.. / / . -. -.. --..-- / / --- / / .-. / / --- ..- .-./.-..-. .... ----- .--. ...-- ... -.. .--.-. ... .... . -.. .-..-. ..--.. -> Morse Decode -> IZ DIS D END, O R OUR "H0P3SD@SHED"?
- h0p3sD@shed -> k k. Enuf alredi. U R l%kin 4 a flag dat wen decrypted wiL L%k lIk "flag{REDACTED}". d encryptd msg iz bElO. U wiL hav 2 decode it first, thN U wiL hav 2 figur out d XOR key & actually decrypt it. wen U hav it, go bak 2 d badge & "hack flag wit REDACTED" n saEm plAc u found dis chlng: BwIFCQMGMQAALA8CKhwCHB0eDCZCD1EZ -> TIME TO ACTUALLY DO SOME WORK. So at this point you have to start brute forcing. That is a Base64 encoded message, so decode it from B64 before attempting to decrypt it. Since you know it looks like "flag{.." you already know the first 5 characters. Keep going. Eventually you can figure out it is "iCanHazEncryptI0n?"
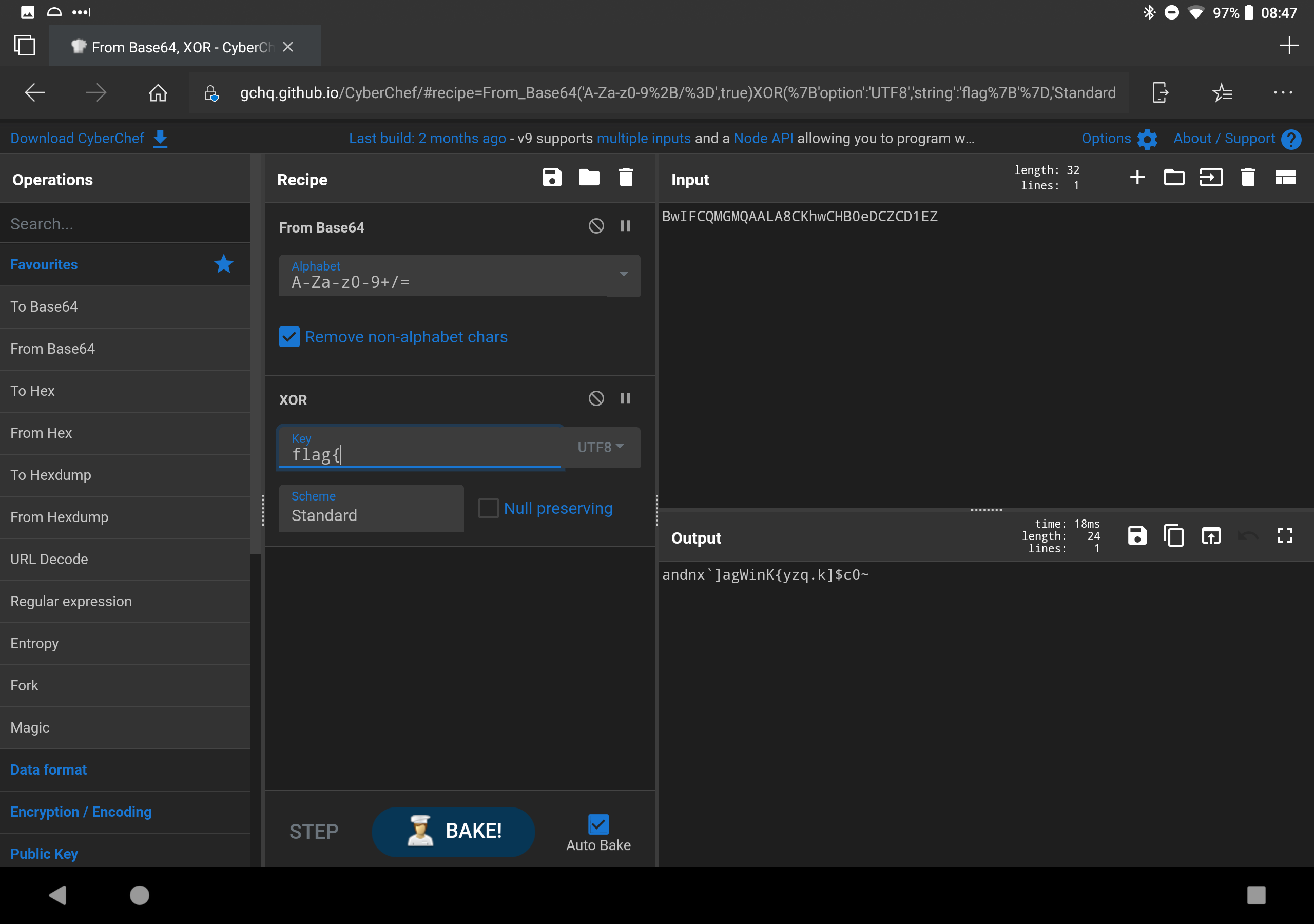
But that is the LONG way. Notice it's XOR? That means there is an inverse relationship between the flag and the key. After you see the begining, you can probably guess "andn..." completes as "andnxor" so swap the key for andnxor and you will see..
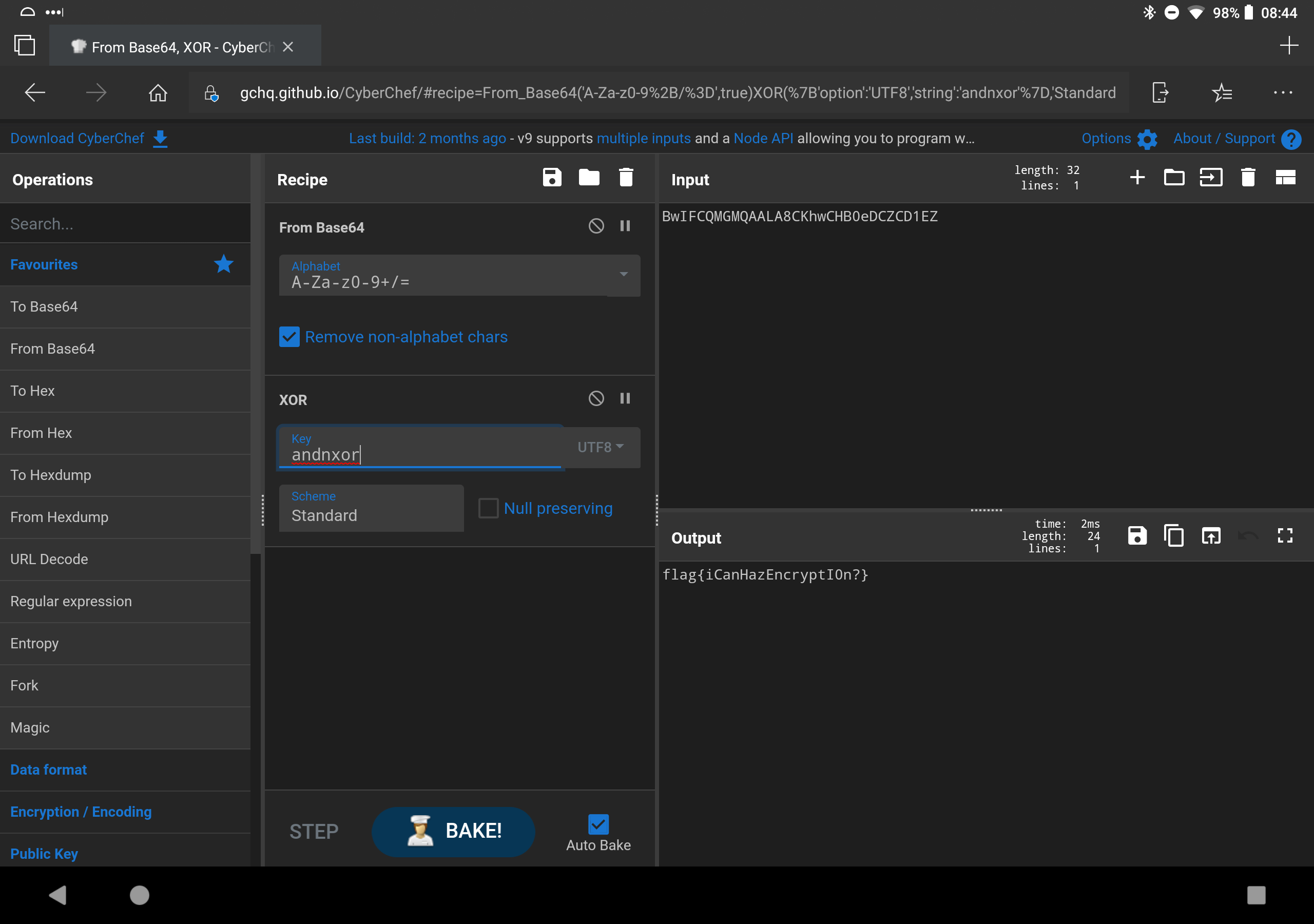
Shout out to Kur3us, he designed this puzzle and its awesome IMHO. Also a great tool for things like this is CyberChef.
Tool unlock: hack HED wit BATTERY
Answer: hack flag wit iCanHazEncryptI0n?
What Did You Learn Today: The XOR property -> if a XOR b = c, then a XOR c = b.
Challenge 10 - CRYPTO/ENCODING Storyline Recap Challenge
WTF hapnd 2 DIS world since DC27? WeL AND!XOR rOt it n a note, tore it up, &...itz randomly spred throughout d wrld. Hav :) putting it bak 2geder 4 recap
Description: Its pretty self explanatory. The final note has been broken into pieces and spread randomly throughout the map which you will find. Collect, save them, decode them, and piece it together to tell the story. To make it easier, here's a dump from the header file...
#define RECAP_00 "44 20 64 63 32 37 20 61 6e 64 21 58 6f 72 20 6e 75 63 6c 65 61 72 20 77 6e 74 72 20 62 61 64 67 65 20 26 20 68 61 63 6b 66 6f 72 73 61 74 61 6e 20 70 61 6e 64 65" #define RECAP_01 "6d 69 63 20 62 61 64 67 65 20 67 6f 74 20 64 72 75 6e 6b 2c 20 68 6f 6f 6b 64 20 75 70 2c 20 26 20 63 61 75 73 65 64 20 44 20 72 6f 6e 61 20 66 72 6d 20 73 6f 6d" #define RECAP_02 "20 6d 65 73 73 65 64 20 5e 20 73 74 64 2e 20 74 68 6e 20 64 65 66 20 43 6f 6e 20 77 7a 20 63 61 6e 63 65 6c 6c 65 64 2e 20 34 20 72 65 61 6c 73 69 65 73 2e 20 73" #define RECAP_03 "69 6e 63 65 20 74 68 6e 20 77 65 76 65 20 73 70 72 65 64 20 72 75 6d 6f 72 73 20 63 75 7a 20 77 65 20 72 20 3a 22 29 20 62 6f 75 74 20 64 20 68 25 6b 20 5e 2e 20" #define RECAP_04 "72 75 6d 6f 72 73 20 73 75 63 68 20 6c 69 6b 20 69 74 20 77 7a 20 62 61 74 73 2c 20 35 20 67 20 63 65 6c 20 74 6f 77 65 72 73 2c 20 62 69 72 64 73 2c 20 62 69 6c" #define RECAP_05 "6c 20 67 61 74 65 73 20 74 72 79 69 6e 67 20 32 20 6d 41 6b 20 6d 6f 6e 65 20 6f 66 66 20 6f 66 20 76 61 63 63 69 6e 65 73 2c 20 63 6f 6e 76 69 6e 63 69 6e 67 20" #define RECAP_06 "70 6f 74 75 73 20 32 20 63 6f 6e 76 69 6e 63 65 20 75 20 32 20 64 72 69 6e 6b 20 42 6c 65 61 63 68 2e 2e 2e 20 66 20 55 20 62 6c 65 76 20 6e 65 20 6f 66 20 64 61" #define RECAP_07 "74 20 55 20 72 20 64 75 6d 62 2e 20 31 30 30 30 25 20 66 6b 6e 20 6c 75 67 2e 20 63 6f 72 6f 6e 61 76 69 72 75 73 20 73 75 78 20 26 20 64 65 2d 72 61 69 6c 65 64" #define RECAP_08 "20 6f 75 72 20 61 6e 6e 75 61 6c 20 63 6f 6e 20 78 70 65 72 65 6e 73 2e 20 69 67 6e 6f 72 20 61 6c 20 64 61 74 20 64 75 6d 62 20 73 63 68 65 74 20 26 20 68 61 76" #define RECAP_09 "20 3a 29 20 68 61 63 6b 69 6e 67 20 64 69 73 20 62 61 64 67 65 2e 20 77 65 20 68 6f 70 20 69 74 20 62 72 69 6e 67 73 20 55 20 3a 29 20 26 20 68 61 70 65 6e 73 2e" #define RECAP_10 "20 55 20 73 68 75 64 20 68 61 63 6b 20 66 6c 61 67 20 77 69 74 2e 2e 2e 75 70 70 52 20 63 61 73 65 2e 2e 2e"
Lets translate this with a hex to ascii...
D dc27 and!Xor nuclear wntr badge & hackforsatan pandemic badge got drunk,
hookd up, & caused D rona frm som messed ^ std. thn def Con wz cancelled. 4
realsies. since thn weve spred rumors cuz we r :") bout d h%k ^. rumors such lik it
wz bats, 5 g cel towers, birds, bill gates trying 2 mAk mone off of vaccines,
convincing potus 2 convince u 2 drink Bleach... f U blev ne of dat U r dumb. 1000%
fkn lug. coronavirus sux & de-railed our annual con xperens. ignor al dat dumb
schet & hav :) hacking dis badge. we hop it brings U :) & hapens. U shud hack flag
wit...uppR case...
The challenge at this point, notice all of the upper case letters. Put them togther.
Tool unlock: none
Answer: hack flag wit DXDCABUUUUR
What Did You Learn Today: More HEX? The Grind? Maybe that messages can be hidden inside of other messages? That Hyr0n has a thing for HackForSatan? Maybe... But really that we heart you all. Its been a crazy year with a lot of crazy things being said. Like the recap message says, we hope this years hacker project brought you some smiles and happiness, and that you learned something new.
 Hyr0n
Hyr0n
Discussions
Become a Hackaday.io Member
Create an account to leave a comment. Already have an account? Log In.