After using the flashing tool to create a flash dump for backup reasons, I read a 8kiB (0x2000) section of the start of flash and then wrote it back using the User Data feature of the tool.
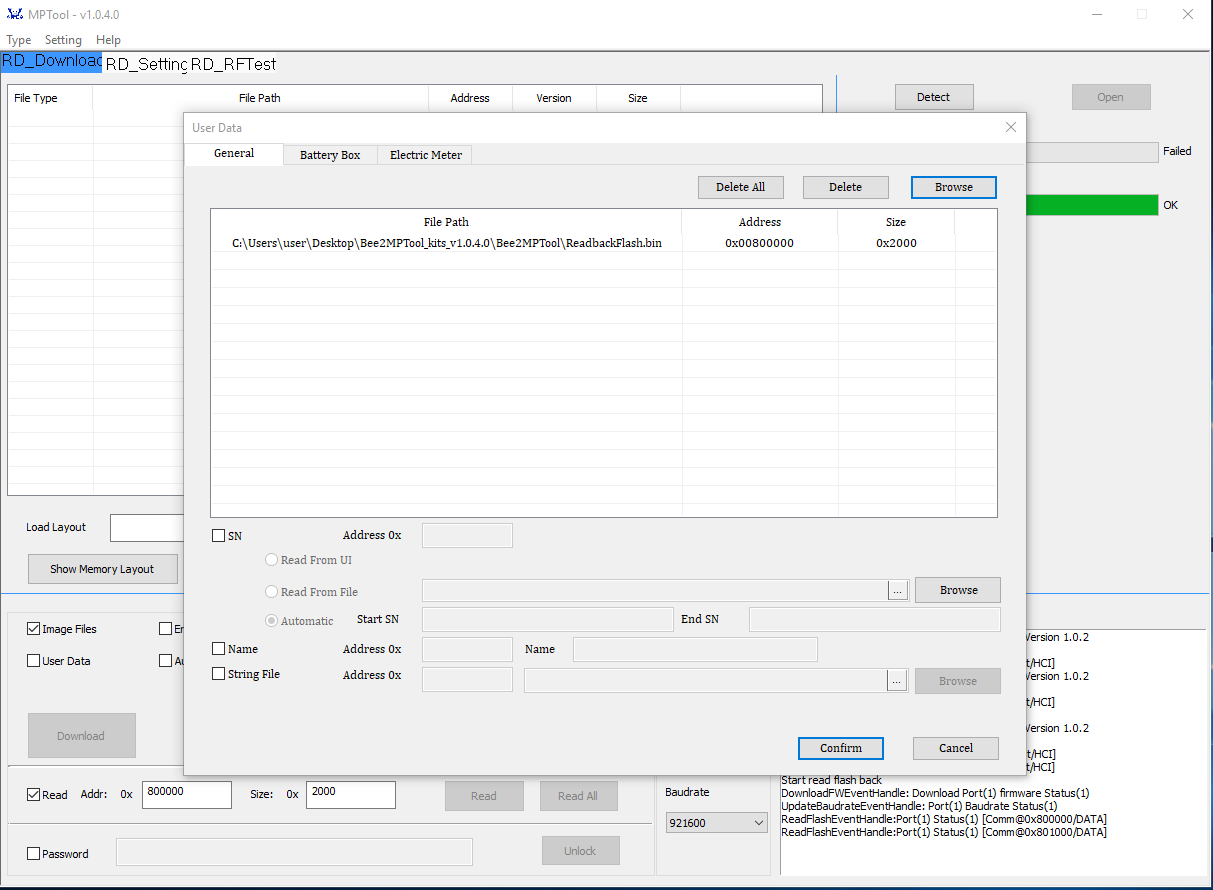
The MessageBox logs two EraseFlash and then two consecutive WriteFlash and VerifyFlash events.
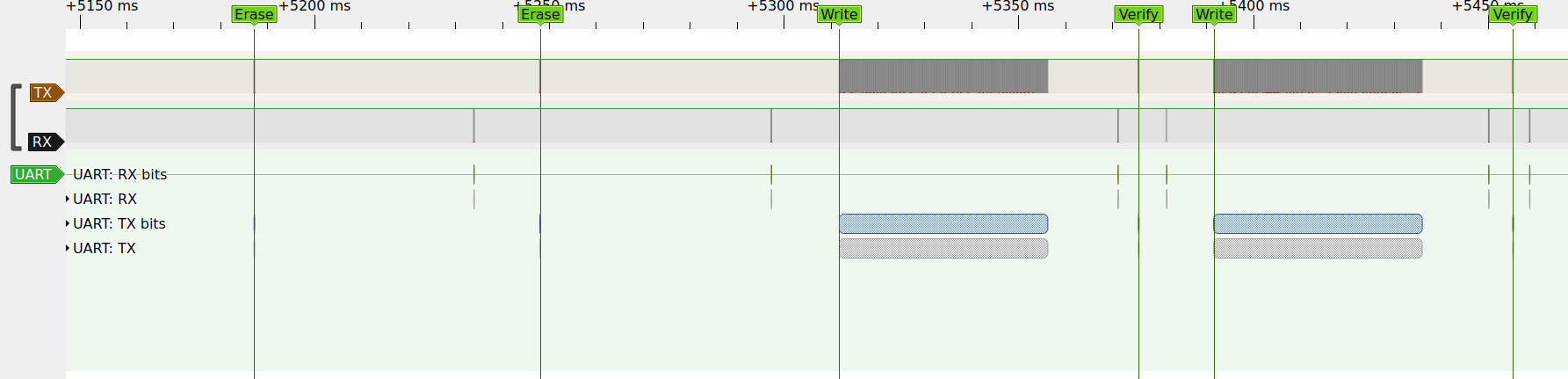
This is also visible in the captured signals. I also tested the Chip Erase function of the tool and captured its operation and response code. By checking the numbers of bytes transmitted, recording more examples and using reveng I found more uses of the CRC.
| Protocol Phase | Op/RespCode | Parameters: length |
| TX: erase sector | b"\x87\x30\x10" | - address: 4B - length b"\x00\x10\x00\x00": 4B- CRC-16/ARC: 2B |
| RX: acknowledge erase sector | b"\x87\x30\x10" | - stuffing (b"\x00"): 5B- CRC-16/ARC: 2B |
| TX: erase 16 sectors | b"\x87\x35\x10" | - address: 4B
- length b"\x00\x00\x01\x00": 4B- CRC-16/ARC: 2B |
| RX: acknowledge erase 16 sectors | b"\x87\x35\x10" | - stuffing (b"\x00"): 5B- CRC-16/ARC: 2B |
| TX: erase all | b"\x87\x31\x10" | - CRC-16/ARC: 2B |
| RX: acknowledge erase all | b"\x87\x31\x10" | - stuffing (b"\x00"): 5B- CRC-16/ARC: 2B |
| TX: write | b"\x87\x32\x10" | - address: 4B - length: 4B - payload: nB - CRC-16/ARC: 2B |
| RX: acknowledge write | b"\x87\x32\x10" | - stuffing (b"\x00"): 5B- CRC-16/ARC: 2B |
| TX: verify | b"\x87\x50\x10" | - address: 4B - length: 4B - CRC-16/ARC of flash content: 2B - CRC-16/ARC: 2B |
| RX: acknowledge verify | b"\x87\x50\x10" | - stuffing (b"\x00"): 5B- CRC-16/ARC: 2B |
 marble
marble
Discussions
Become a Hackaday.io Member
Create an account to leave a comment. Already have an account? Log In.