Opened up case, saw the following
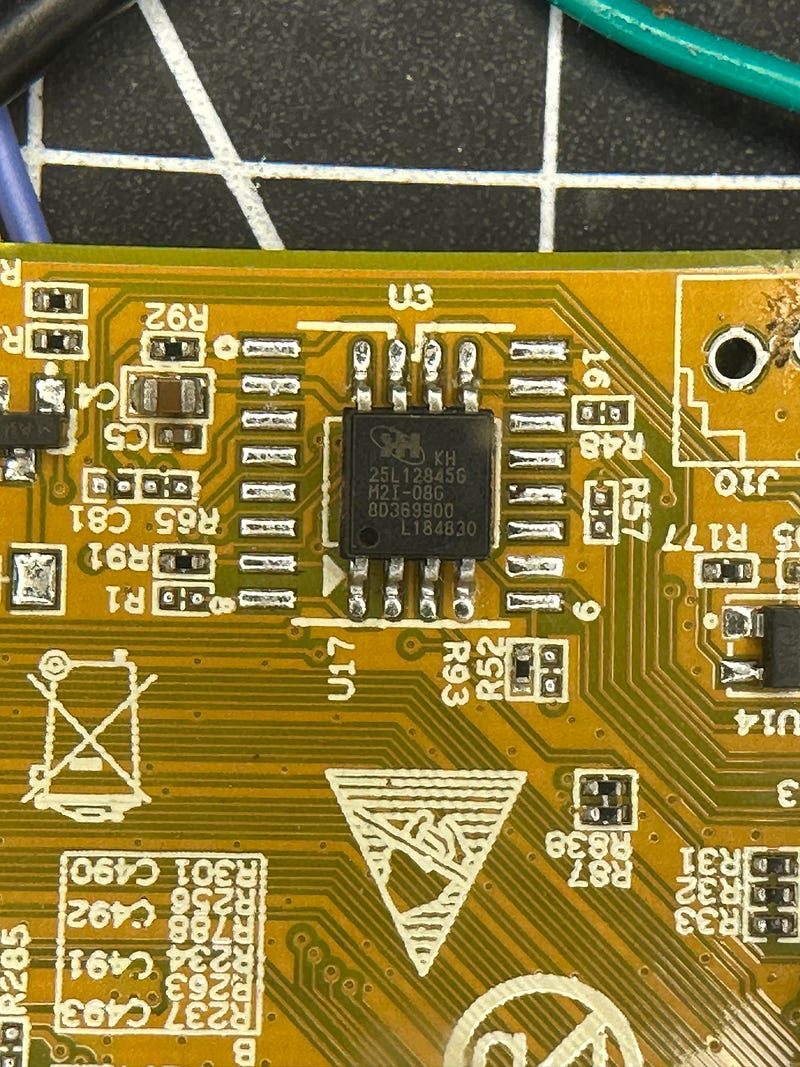
- Flash chip KH25L12845G
- 2 20-pin headers
- USB input
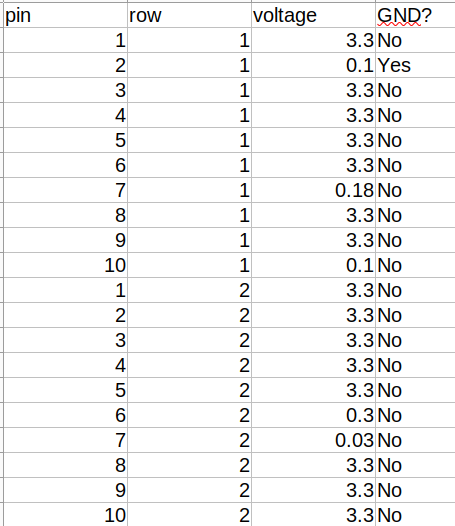
I tested the 20-pin header that had leads going to (presumably) the CPU. Here are the voltages:
Pivoted to looking at the flash chip. Here is the datasheet:
https://www.macronix.com.hk/Lists/Datasheet/Attachments/312/KH25L12845Gver11-1.1.pdf .
This is a run-of-the-mill SOIC-8 SPI Flash chip:
I setup my Arduino Uno to dump the flash:
- run `git clone https://github.com/urjaman/frser-duino`
- run `make flash-u2`
I carefully de-soldered the flash chip from the board.
- Used a rework station to blow hot air on the chip to release it.
I prepped the chip for reading
- seated the chip in a SOIC-8 socket and placed on breadboard
- Pin hookup:
- Pins 3,7,8 (WP, HOLD, and VCC) to Arduino 3.3v
- Pin 4 (GND) to Arduino GND
- Pin 1 (CS) to Arduino pin 10
- Pin 5 (MOSI/SI/COPI) to Arduino pin 11
- Pin 6 (MISO/SO/CIPO) to Arduino pin 13
I used `flashrom` with arduino to dump flash:
`flashrom -p serprog:dev=/dev/ttyACM0:115200 -r flash_dump.bin`
I then used binwalk to extract the filesystem:
`binwalk -e flash_dump.bin`
There was a full embedded Linux filesystem (using busybox).

I found an old DES encrypted password in "/etc/passwd-", which looks to be a backup file for `/etc/passwd`
- I bruteforced it with hashcat,
- `hashcat -m 1500 hash.txt /usr/share/seclists/Passwords/rockyou.txt
- found it in a matter of seconds (not gonna post that here)
I found a MD5Crypt encrypted password in "/etc/passwd". I have not been able to crack it yet. This is unfortunate, as this is the actual root password for the system.
Next on the agenda is to look at implanting fake updates over USB. At first glance, there doesn't appear to be any/many protections other than file name checking. Could be fun.
 Andrew (@datagoboom)
Andrew (@datagoboom)
Discussions
Become a Hackaday.io Member
Create an account to leave a comment. Already have an account? Log In.