So, yesterday I've played around with damico's Arduino-OATH-Token (https://github.com/damico/ARDUINO-OATH-TOKEN) so I can use his code with my own timer bar. There was also just a small edit necessary to make the algorithm work with the code I've got from google since it was two bytes longer than the authenticator expected.
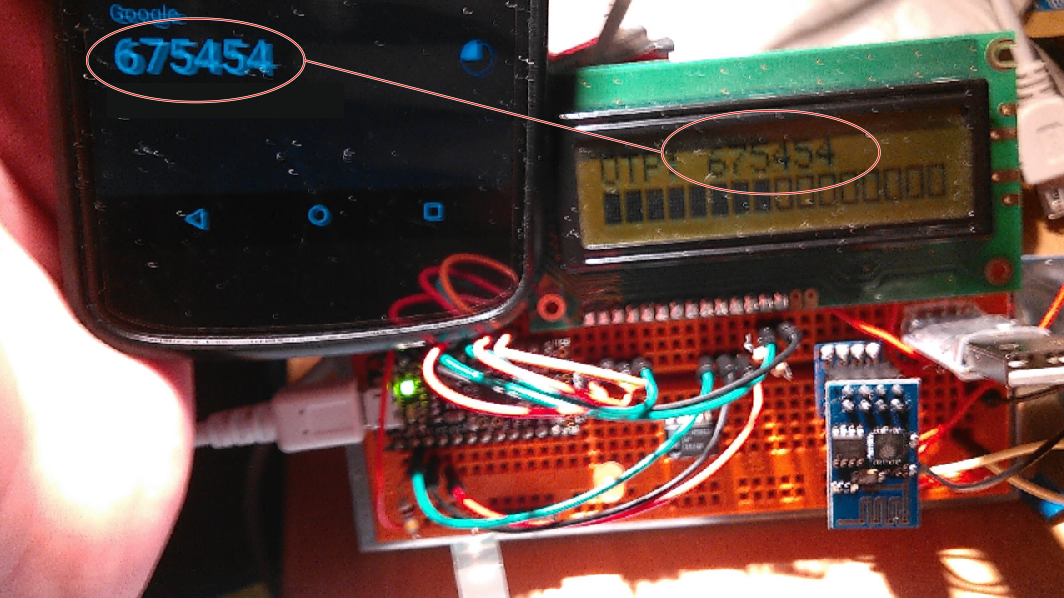
As you can see in the picture above, the codes of the Trinket and Google Authenticator match.
After this was done I wanted something nicer than some components plugged into a breadboard so I made a prototype for the hardware design. It is big enough to fit the components side by side and theoretically a battery pack and even though the final device is planned to be much smaller, the current version will still fit into my jeans pocket.
Because the authenticator is supposed to handle multiple accounts in the future I needed some kind of menu controls. Since the I2C OLED display I've ordered hasn't been delivered yet and the one I currently use needs almost all of the pins and I still need 2 for the I2C RTC module (which didn't arrive yet either), I didn't have enough pins left to connect all five button I wanted.
To work around this I connected all the buttons via a voltage divider with different resistors per button to one analog input and differentiate them by their specific voltage drop.
Below you'll see the circuit diagram for the buttons and the current hardware protoype.
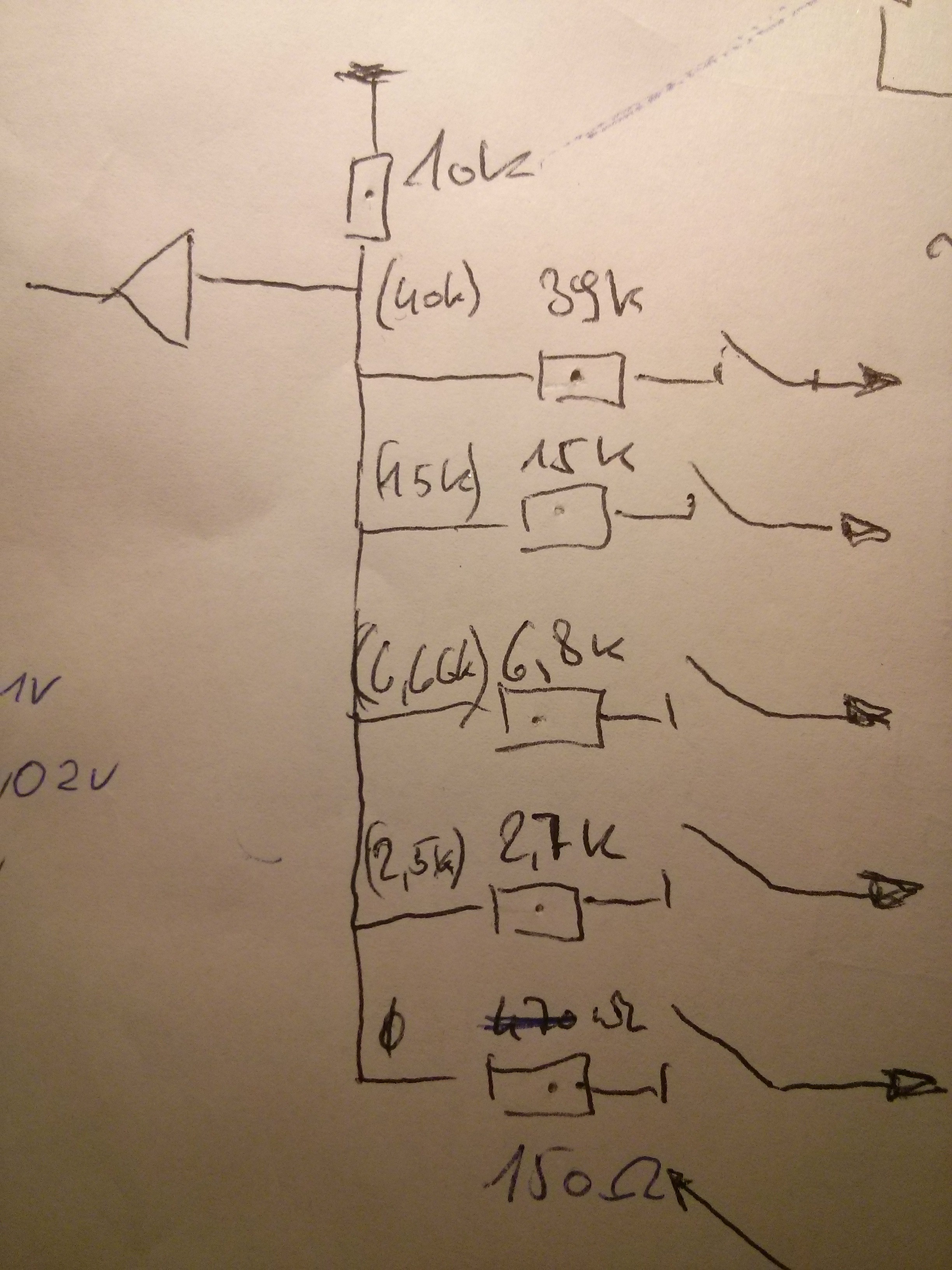
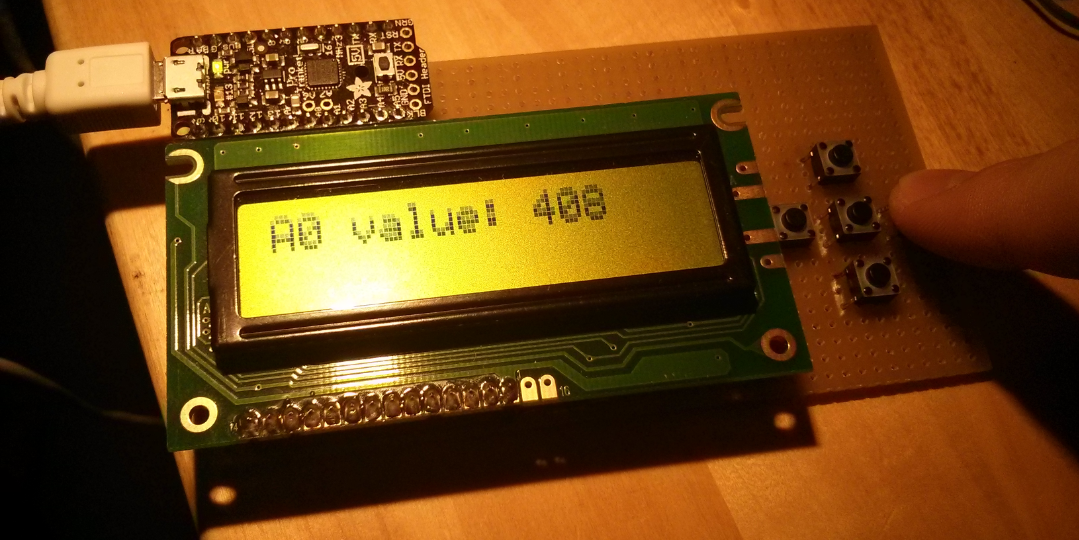
Now I have to continue working on the code to implement a menu and multi account support.
 naqua
naqua
Discussions
Become a Hackaday.io Member
Create an account to leave a comment. Already have an account? Log In.
Hey, sorry for the late reply unfortunately I didn't have much time for this project recently.
You can use this simple two liner in Python 2:
import base64
print ', '.join([hex(ord(i)) for i in base64.b32decode('base 32 secret here')])
In damicos code you need to change line 46 from "Sha1.initHmac(hmacKey1,16);" to "Sha1.initHmac(hmacKey1,20);" since Google changed the length of the secret to 20 bytes.
You can also use this much neater version "Sha1.initHmac(hmacKey1,sizeof(hmacKey1));" if you want more flexibility for other secret lengths.
I will also eventually publish my changes when I have the time to work more on the code and have cleaned it up a little.
Are you sure? yes | no
How did you convert the text string used by the Google App for the secret key to the bytes used by the Sha1.initHmac()?
Are you sure? yes | no