Long time ago I ordered several ESP8266 modules (ESP-201) for my yet-to-be-made home automation system. Not long before that time I had Wi-Fi security related project on "big" PCs. Which inevitably brought me to well known Kali system. So, idea to use tiny ESP8266s for wireless penetration tests come to my mind immediately after I had them on my table. But quick look through early version of Espressif SDK doesn't reveal any "hacker friendly" functions. So, I focused on other applications.
Some time ago I, as a faithful Hackaday RSS feed subscriber, read article about packet injection on ESP8266. This article finally gave me last part of the puzzle and plan for the weekend.
HARDWARE
My hardware setup consists of ESP module, mini DC-DC converter (D-SUN), pin headers, jumper, 9V battery plug and four 4k7 resistors.
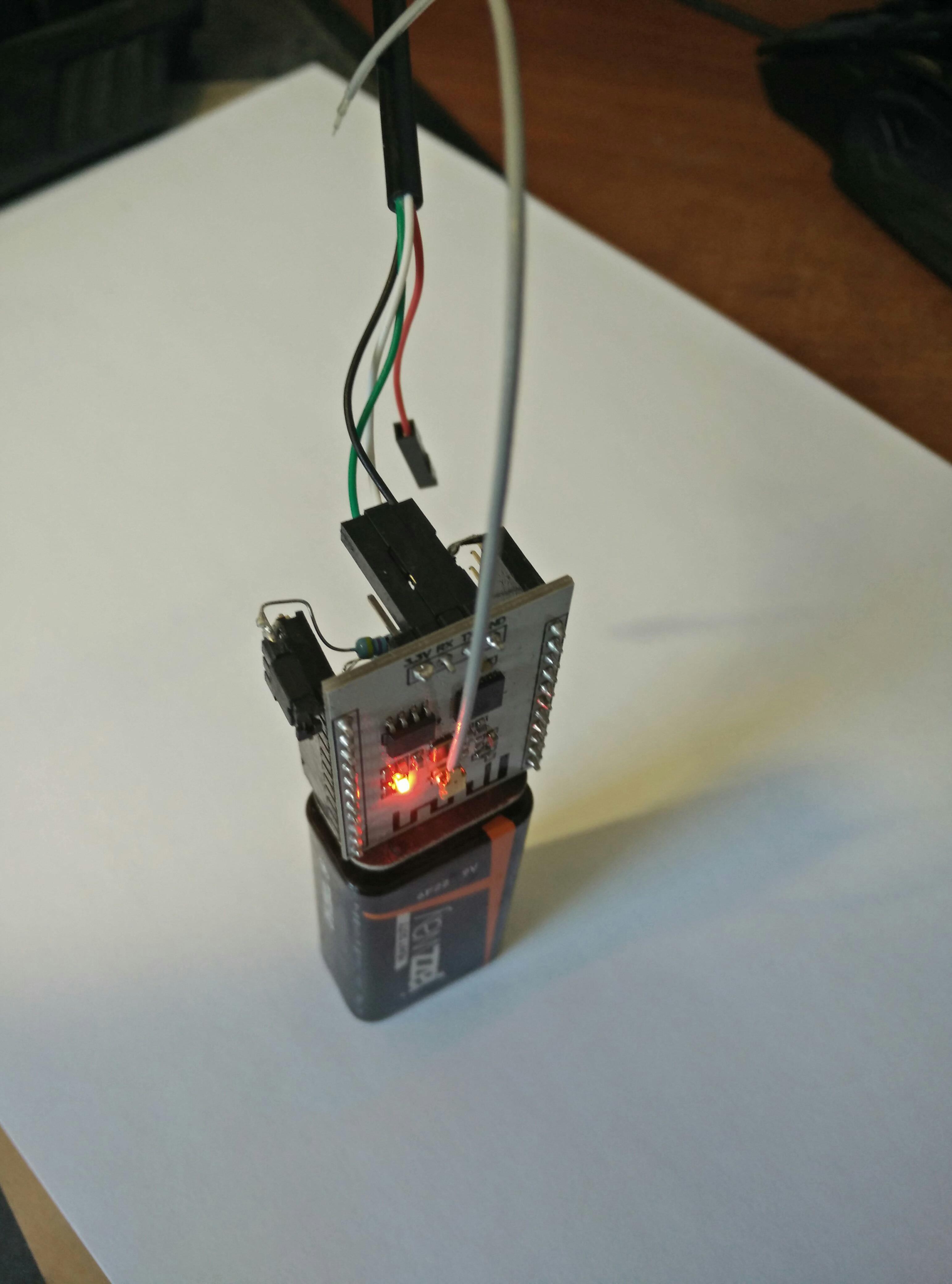

SOFTWARE
I use Arduino IDE (1.6.7), because it can work with all boards I have in my inventory. Also it is multi-platform, I can easily start project on Windows and finish on Linux. I am definitely missing code completion and editor tools from my "working horse" - MS VS, but for the small scale projects it doesn't matter much.
I started with code from original article, but first adopted it for Arduino project, and finally replaced nearly everything, looking with one eye onto the MDK3 source code. My code have couple of strange things, some fixes I made looking at test results, without deep understanding and reading standards. First - I do not have time for complete analysis, and second, let's face the truth, I can't see many usages for this code except to show it to my friends.
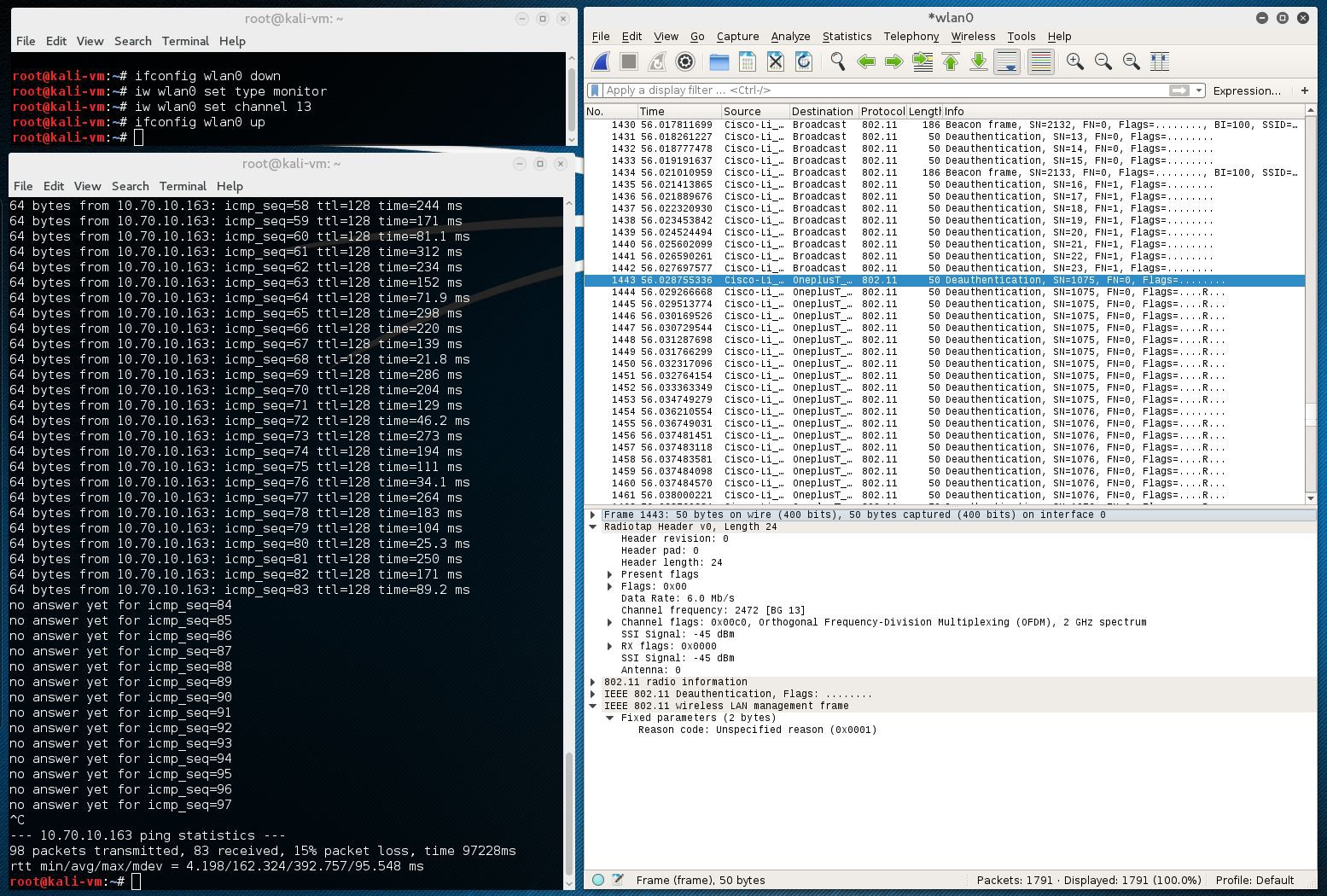
Below is the screenshot from wired Kali system which I use for monitoring. You can see how ping to my phone connected over Wi-Fi was terminated after ~10 seconds after I attached battery to assembly. Also you can see Deauthentication packets in Wireshark dump.
Different devices behave differently in response to this attack. One of my phones goes permanently offline, and another manages to reconnect quickly, while software checking other channels. There are several options I can suggest for people who would like to have more stable effect:
- At some moment stop scanning and only quickly hop over channels with DeAuth procedure.
- Play with time constants and packet numbers, to find better combination.
- Buy 14 ESP modules for every Wi-Fi channel :-)
There is a catch with Espressif SDK versions and "wifi_send_pkt_freedom" function. As it is mentioned here, "....wifi_send_pkt_freedom can't send management packets and encrypted packets, beacon is one kind of the management packets. We add this limitation because it may effect other devices......"
BUT, this fix is applied by Espressif only in latest versions of SDK. In the SDK version 1.3.0 "freedom" function was already present, but without limitations. You only may...
Read more » Rand Druid
Rand Druid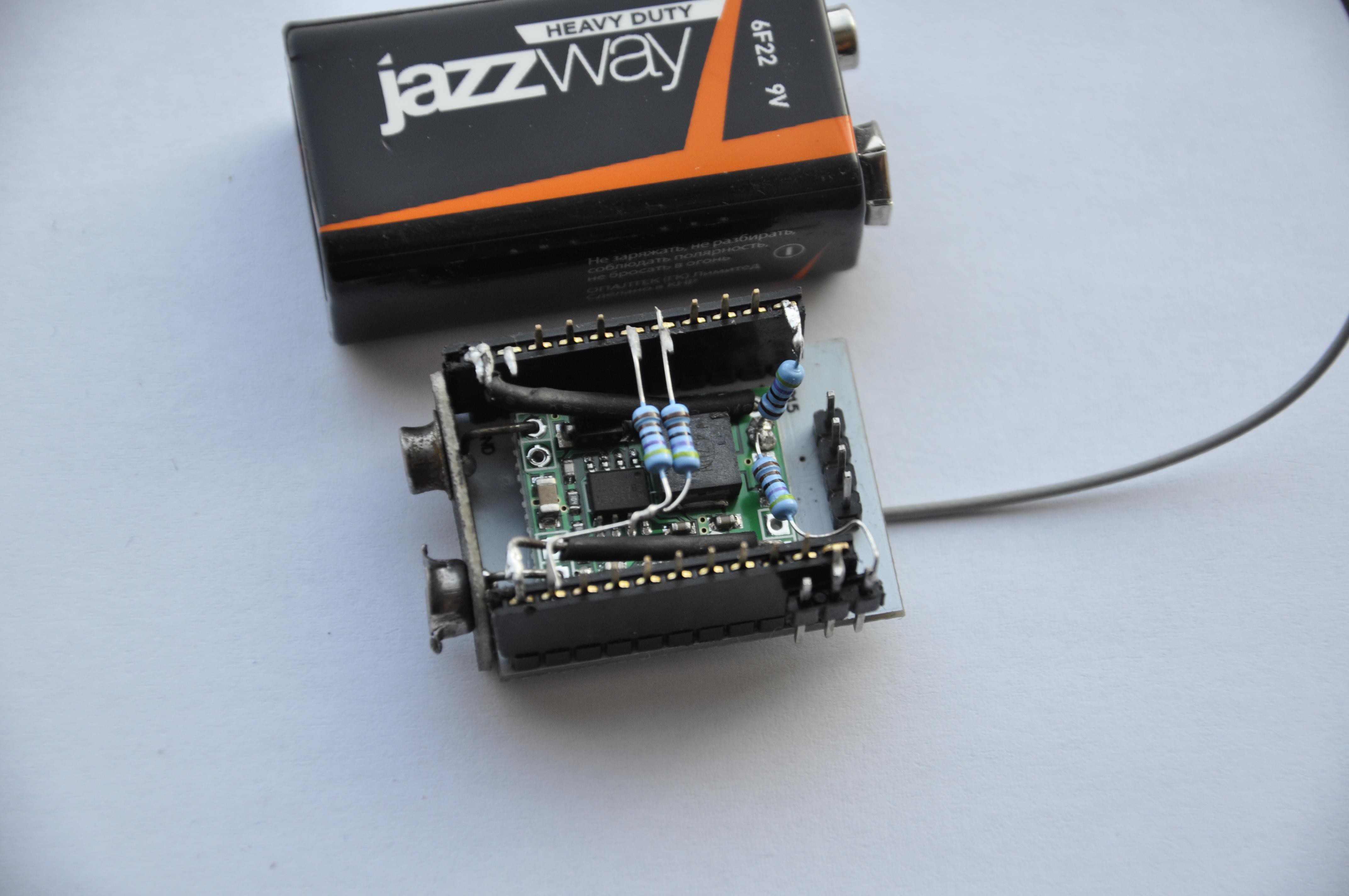


If you like the MS VS environment, the Atmel development environment uses it for their ARM stuff as well as their other processors.