Lots of fun updates! First, I'm honoured to have made it to the final five for the Hackaday Prize. There has been a ton of work showing up on all these projects, so it must have been a razor-thin margin between the projects that made it and the ones that didn't, and a lot of time spent by the judges! Thanks to all involved for this.
Next, I've pushed the 0.08RC1 release, available on the software release page. The 0.08RC1 release supports all the features you need for the AES-256 bootloader attack, so go ahead and download the sample traces and break the bootloader yourself. This includes the Python-based analysis script feature which I think will become one of the core functions for the CW-Analyzer due to it's flexibility. I'm still hoping to add some additional support for remote networked capture boxes in the coming week or two.
Finally, two academic papers that might be of interest to you (I swear). The first explores the use of clock recovery with the ChipWhisperer. You can read a version of it on IACR EPrint, and I'm happy to announce it was accepted into the Journal of Cryptographic Engineering, so will appear there at some point in the future. This paper goes to show that having open hardware and software will make it easier than ever for researchers to duplicate my work... it's simply not possible to have this level of transparency in how I obtained my research results without invoking the open-source model.
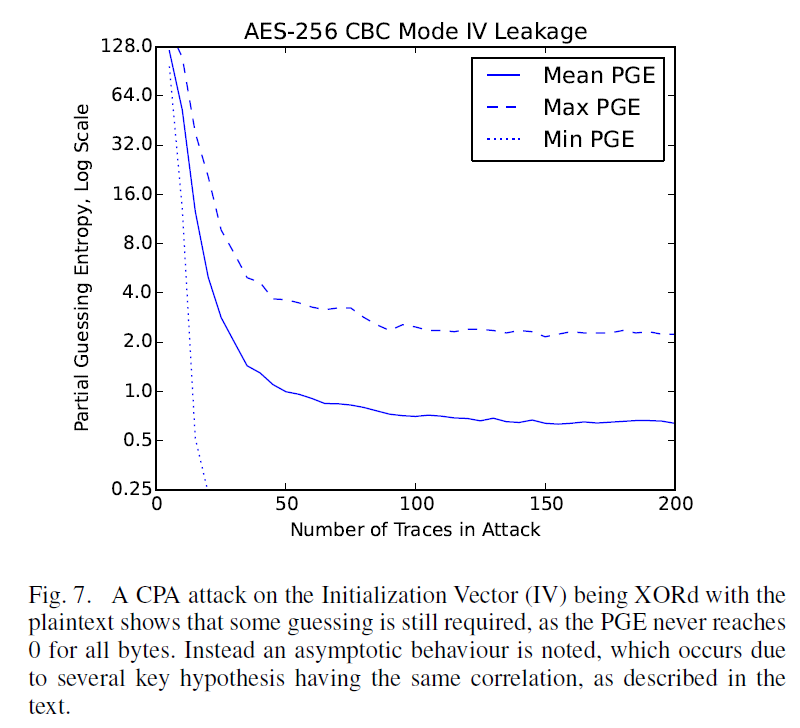
The second is a paper based on my work attacking the AES-256 bootloader, which is still in progress. The pre-print is available from IACR E-Print service (not sure where the final version will end up yet, if anywhere). But it goes to show the results of attacking the XOR operation in the I.V. of the AES CBC mode.
Speaking of papers, I recently discovered that my OpenADC project has been used by a few other researchers doing work into low-power wireless networks and ended up in some published papers. It's definitely cool to see these tools propagating 'in the wild'. I've added links to my main project description with those papers.
 Colin O'Flynn
Colin O'Flynn
Discussions
Become a Hackaday.io Member
Create an account to leave a comment. Already have an account? Log In.