USE OF ISABELLE HOL FOR DOOM VERIFICATION AND VALIDATION
IN OTHER WORDS...... IF YOU WRITE SOFTWARE FOR A GAME LIKE DOOM... WRITE AND
ANALYZE THE SOURCE CODE AS IF YOUR VERY LIFE DEPENDED ON IT .......
HENCE THE USE OF SAFETY CRITICAL SOFTWARE DEVELOPMENT METHODS LEARNED FROM CREATING SOFTWARE FOR JET ENGINE FADEC CONTROLLERS AND THEN APPLY IT FOR VIDEO GAMES.....
WHY THE HELL NOT ????
LETS SEE IF WE CAN FIND EXTREMELY SUBTLE SOFTWARE FLAWS WITHIN THE DOOM SOURCE CODE THAT HAVE ELUDED DETECTION OVER THE LAST 27 YEARS... SINCE 1993.....
IN A FINAL SENSE OF GLORY TO HAVE MORE CARNAL KNOWLEDGE FOR THE SOURCE CODE THAN WHAT WAS THOUGHT POSSIBLE.....
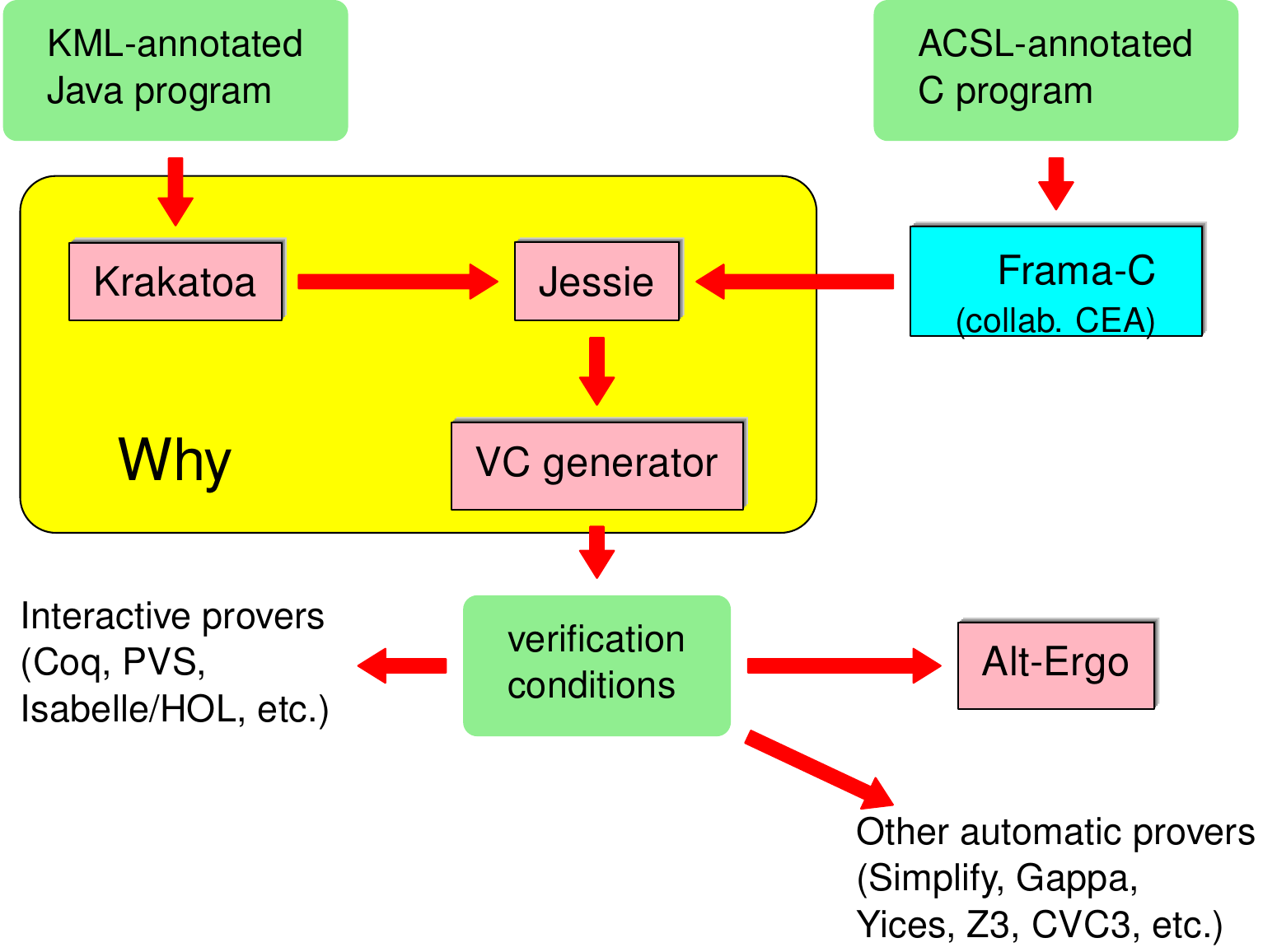
Compile with all warnings enabled, and use one or more source code analyzers.

 Martin Hub
Martin Hub
 Hacker House
Hacker House
 Norbert Heinz
Norbert Heinz
 technolomaniac
technolomaniac
Please provide feedback ??