DISCORD GROUP => https://discord.gg/HfJhd2S
Before we get into the project's details, I would like to invite you to join our Discord group where we chat about hacking, electronics, IoT, and much more => https://discord.gg/HfJhd2S
SCHEMATIC => https://qortex.cc/products/open_mac
For those interested in the web app, you can check it here by signing up => https://qortex.cc
SOURCE CODE => https://github.com/kalanda/esp8266-sniffer
THE THINKING
The device I made is based on the ESP8266 popular chip from Espressif, it's where all those NodeMCU come from. If I where to be a lazy dude I would eventually grab a bunch of NodeMCU or D1 Mini pro's and get the tracking tool running. However I knew this was going to be a tool for hackers and had to be in my hacking arsenal, which made me rethink twice before uploading the code to my NodeMCU.
IT HAD TO BE INVISIBLE
The device I was going to build had to be very small in order to fit it in hidden places like books, shelfs or my own pocket. Before even programming the NodeMCU to check if it works or not, I started laying out the components I had previsouly put on my schematic on Eagle CAD software and everything was taking it's shape.
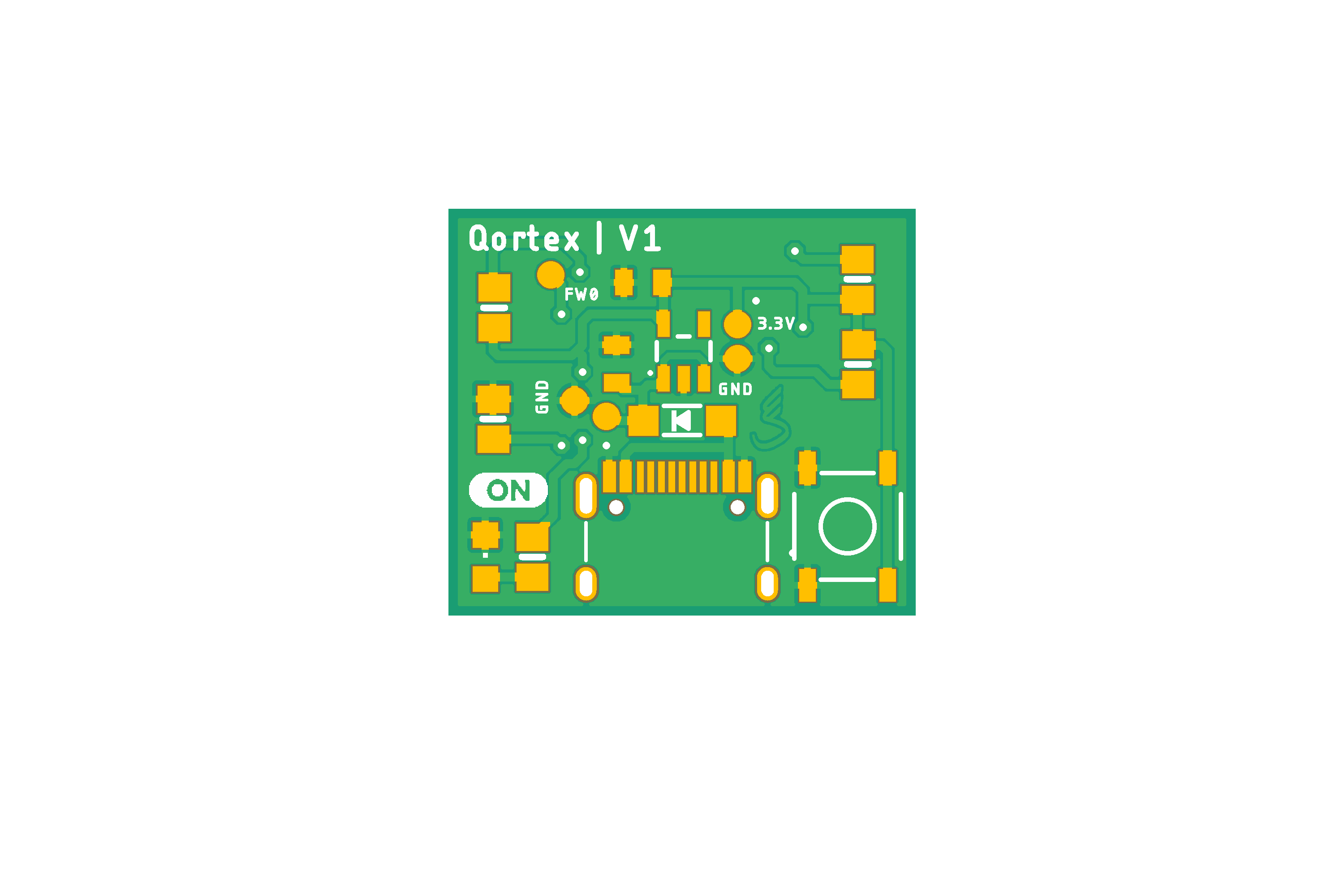
The board has roughly 12 components onboard, all of them surface mount and easy to solder with 0805 package. It has a green led to indicate when it's on and a reset button in case I want to update wifi creds (SSID and pass).
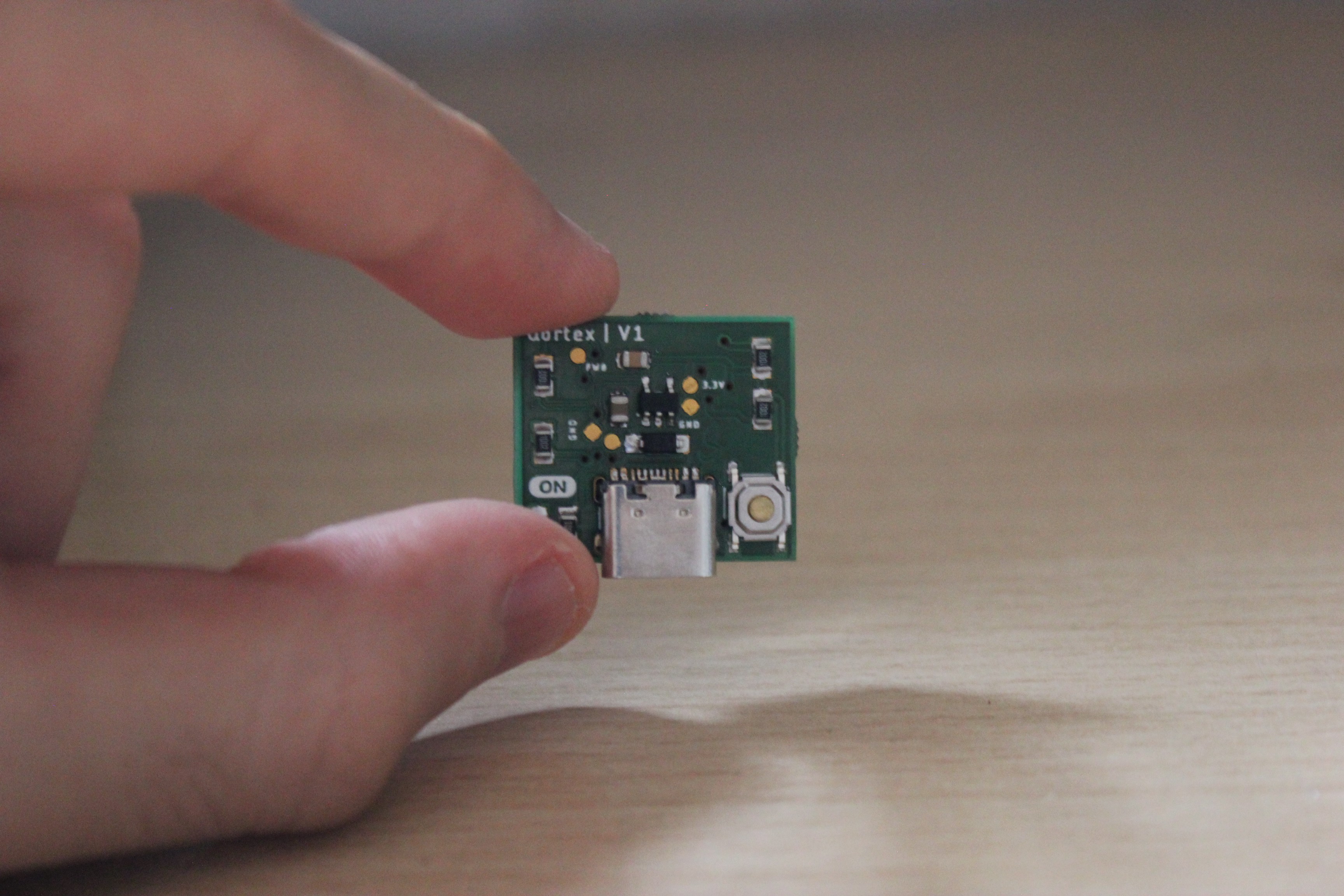
The usb c connector is used just for powering the board.
PROGRAMMING
Now it was time to upload the code to the device, but this time I would use a custom-made jig to do so. I did not put any labels to the test pads so that no one could "hack" the device for getting the code inside it nor uploading. It does however support OTA so I can update the code from my web app anywhere and anytime I want.
I still have to do some code tweaks, I promise it will be open-source on github.
MAC ADDRESS DATABASE
As you may know, I had already made an IoT platform for my projects. The best part is the database because not only I can sniff MAC addresses from nearby devices, but also save to a database no analyze and check for relations between other mac addresses targeted in other areas.
THE "ATTACK"
In order to perform the tracking I had to setup a network of 8 devices like this one plus a LiteFi 1 ESP8266 repeater I was selling on Kickstarter. It was a mesh-like formation placed at my city's library (of course I got the permision to do so) in 8 locations that had a lot of traffic.
The repeater used in this project:
With the hardware being ready, I just had to sit and watch how my database was getting filled with new unique (not randomized) MAC addresses. With this device I was able to target over 526 MAC addresses in 2 days. Each MAC address had an RSSI value which indicated the proximity of the devices.
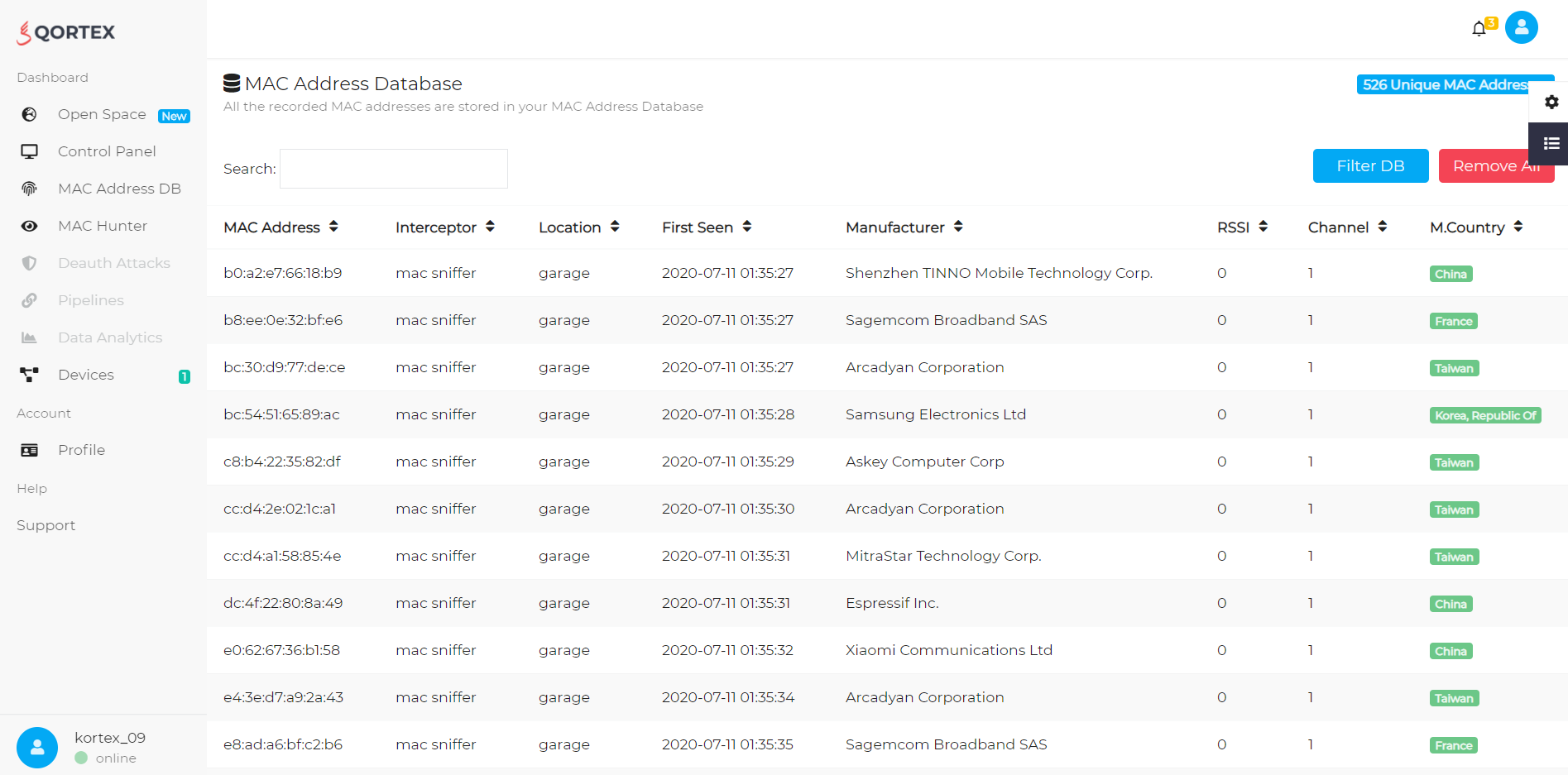
I set up my repeaters to be open so anyone could connect. On my web app I was able to see all MAC addresses connected to my repeater. Now I could now who was in the library, the time it entered and other stats like packets sent and received.
To summarize the repeaters were used to see who is connected to the main library wifi, while the tiny MAC sniffer devices I made were used to sniff all mac addresses from smartphones and laptops. If we combine all that we can know:
- Who entered the library, since we can assign a name to the MAC address in DB.
- Who is connected to the library's wifi (again we already have the MAC stored in DB)
- The number of people who are in a certain place in the library
- The flow of in/out people from a specific place
- We can search for a specific person and get notified once it has entered the library.
All this could be done without anyone noticing. We could place these devices secretely in a bus or public space where free wifi is available and start sniffing people's mac addresses. Again, do not do it illegally....
Read more » Amine Mehdi Mansouri
Amine Mehdi Mansouri




 tdicola
tdicola
 Grandeur
Grandeur
 AKA
AKA
Seems promising, but I can not find the source code in your Github repos.