
With "Maelstrom," one of the hardest parts has been striking the right tone. I want visitors to understand that their data can be gathered and reused in ways difficult to predict, but I also want their visit to be a rewarding experience--and not too scary.
The installation passively listens for these kinds of data:
- WiFi connection probe requests. Your phone sends these transmissions in an effort to see whether your favorite WiFi networks are nearby. With a special device, a Maelstrom machine listens for these requests. The phone's unique WiFI network identifier (MAC address) includes a code that indicates the device's manufacturer. Maelstrom's software looks for this.
- Nearby Bluetooth low-energy (BT LE) devices occasionally emit a peep letting nearby devices know that they are present. A Maelstrom node uses its Raspberry Pi's Bluetooth radio to listen for these BTLE devices and their names, like "Charge 2." It also looks at their MAC addresses and attempts to determine the device's manufacturer, like "Fitbit."
If you interact with the WiFi network, Maelstrom_PUBLIC, provided by the installation, it can further sense some attributes about your device:
- When signing in to the "captive portal" provided by Maelstrom's software, details about your browser are revealed:
- user agent
- browser version
- operating system
- screen size
- whether it is a touch screen
- These attributes, and others, can be used as a fingerprint to identify your device model, and perhaps to uniquely identify you.
- The Python library user_agents also attempts to discern whether your device is a phone, tablet, or desktop computer; your device's overall family, such as "iPhone"; and whether you are a human, or an automated "spider bot."
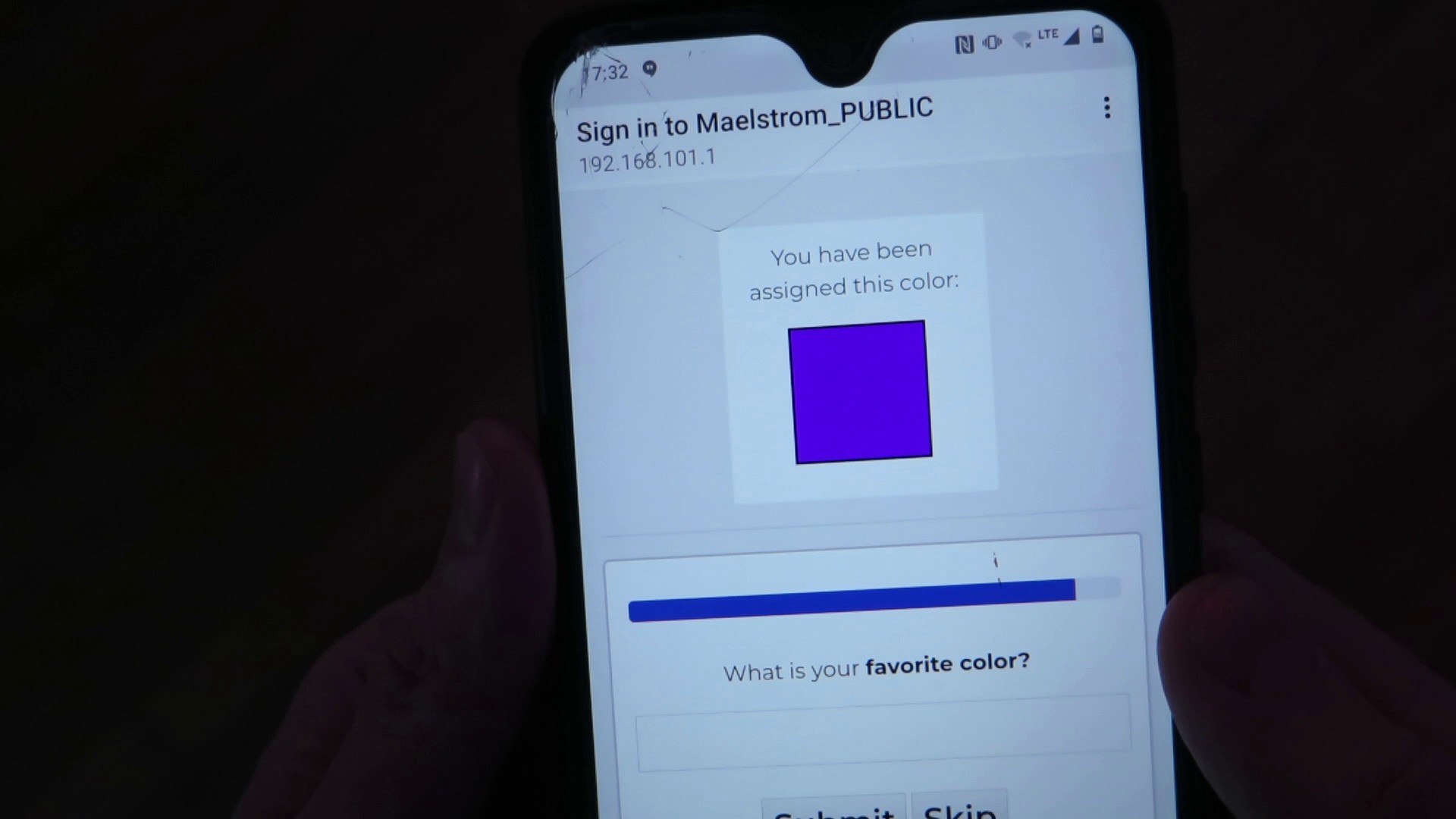
The captive Maelstrom_PUBLIC network also asks you to provide these details to "sign in to the network":
- first name
- then, in random order:
- last name
- middle name
- favorite color
- mother's maiden name
- street address
- childhood phone number
- phone number
- ZIP code
- age
- nickname
- first pet's name
- There's a Skip button, which doesn't really skip the question, they just end up again later. Easter egg/commentary on my part.
- There's no real network to join at the end. It just thanks you for providing all your data and shows you what you provided.
You can use a card-scanning station to detect attributes from a credit card or ID card (with a visual "2D barcode" on the back):
- shortened card number, last 4 digits
- expiration date
- name
- any other attributes exposed by your motor vehicle department or card issuer, such as your height and eye color
- it will also attempt to scrape any useful text (using an algorithm similar to the *nix "strings" command) from other types of cards, like gift cards or membership cards
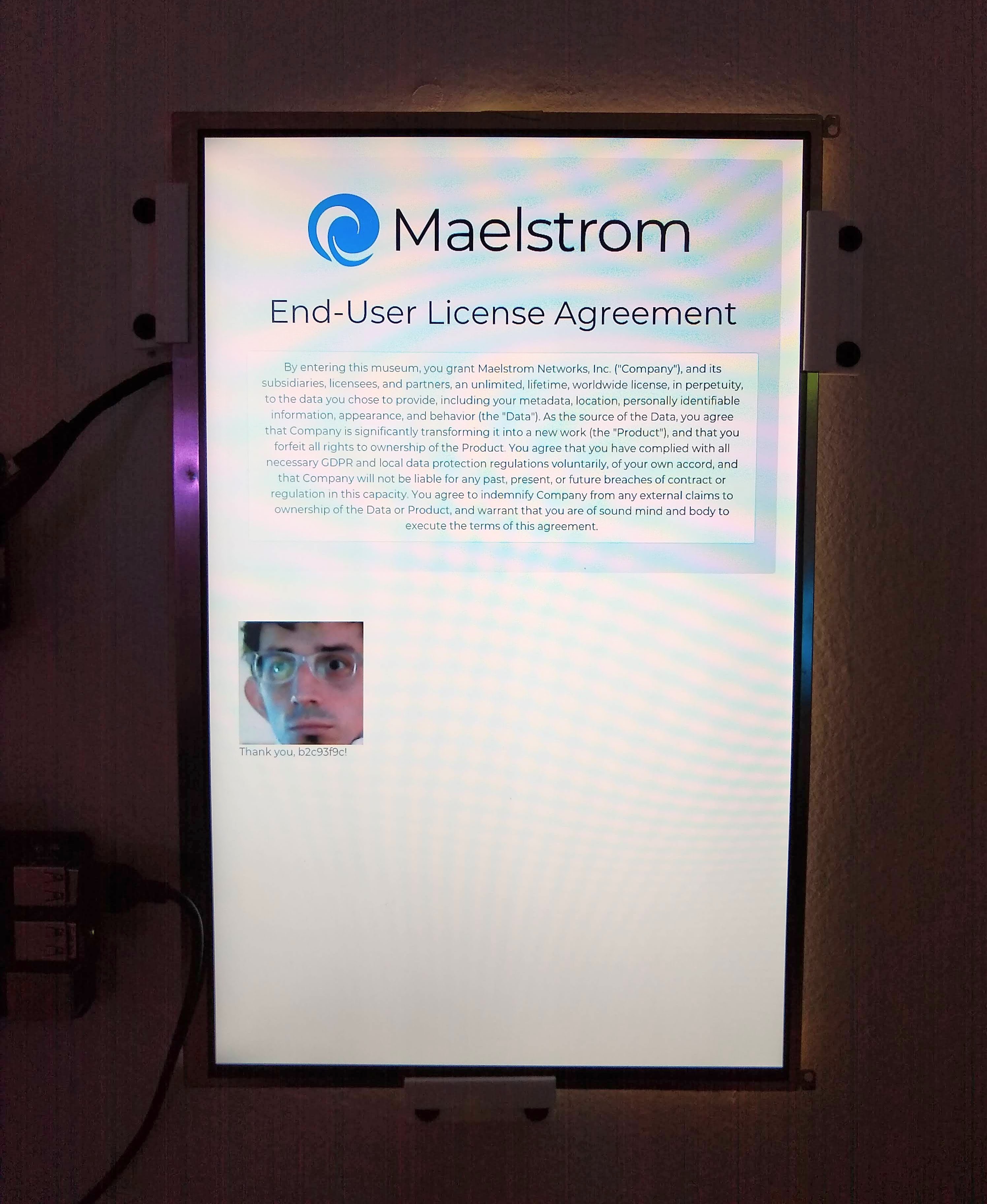
And several machines use attached cameras and the face_recognition Python library to monitor for faces. I didn't go too far with this yet, since it doesn't work well with masks. These are not currently associated with visitor dossiers, but are shown on dedicated screens (the End-User License Agreement shows them in a "Thank you for agreeing!" box; a Maelstrom FR-Class machine shows them as tiles).
All of these data are only retained for 15 minutes, and populated into text written by me, using either Chevron/Mustache (for HTML output methods) or a simplistic templating language similar to Mustache (for text/audio outputs).
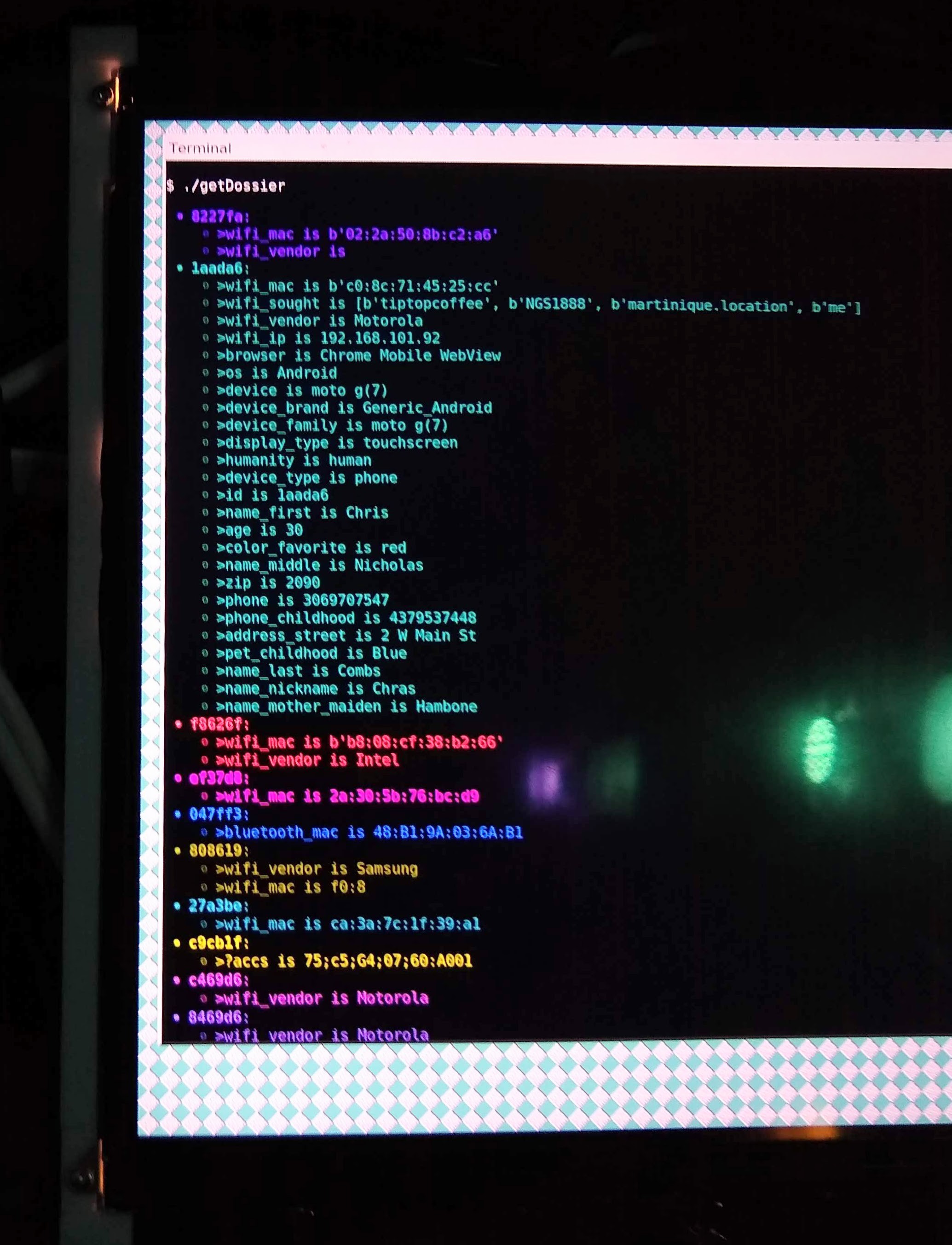
There are a few machines which show the full dossier data that the machine knows for each visitor, but most of the displays will only show or speak whitelisted attributes that I included in the text templates.
 Chris Combs
Chris Combs
Discussions
Become a Hackaday.io Member
Create an account to leave a comment. Already have an account? Log In.