-
About the event in general
12/09/2016 at 18:08 • 0 comments![]()
- Participation: 38 participants
- Attendance: unknown. Some people visited the place just to see what's happening, and some people solved challenges just for fun, without registering.
![]()
- Hackerspace members collectively developed challenges for participants to solve.
- Pick a challenge and start solving it, that's all to it (of course, without disturbing other participants).
- Unconventional ways of solving challenges are encouraged up to some extents, which would be breaking the challenge so that others won't be able to use it and sharing answers, as well as anything unforeseen that'd be deemed as unsportsmanlike by the judges.
![]()
- Two days of hacking, start at 13:37 and end next day at 19:00
- Kaspersky Labs agreed to supply us with pizza to fuel our hacking efforts
- We've had various gadgets as awards from our sponsors for first 3 places, as well as participation awards for places 4 and 5
Some photos:
Starting the competition: briefing
First day of work, solving challenges and fixing WiFi issues
Putting the shredded paper together
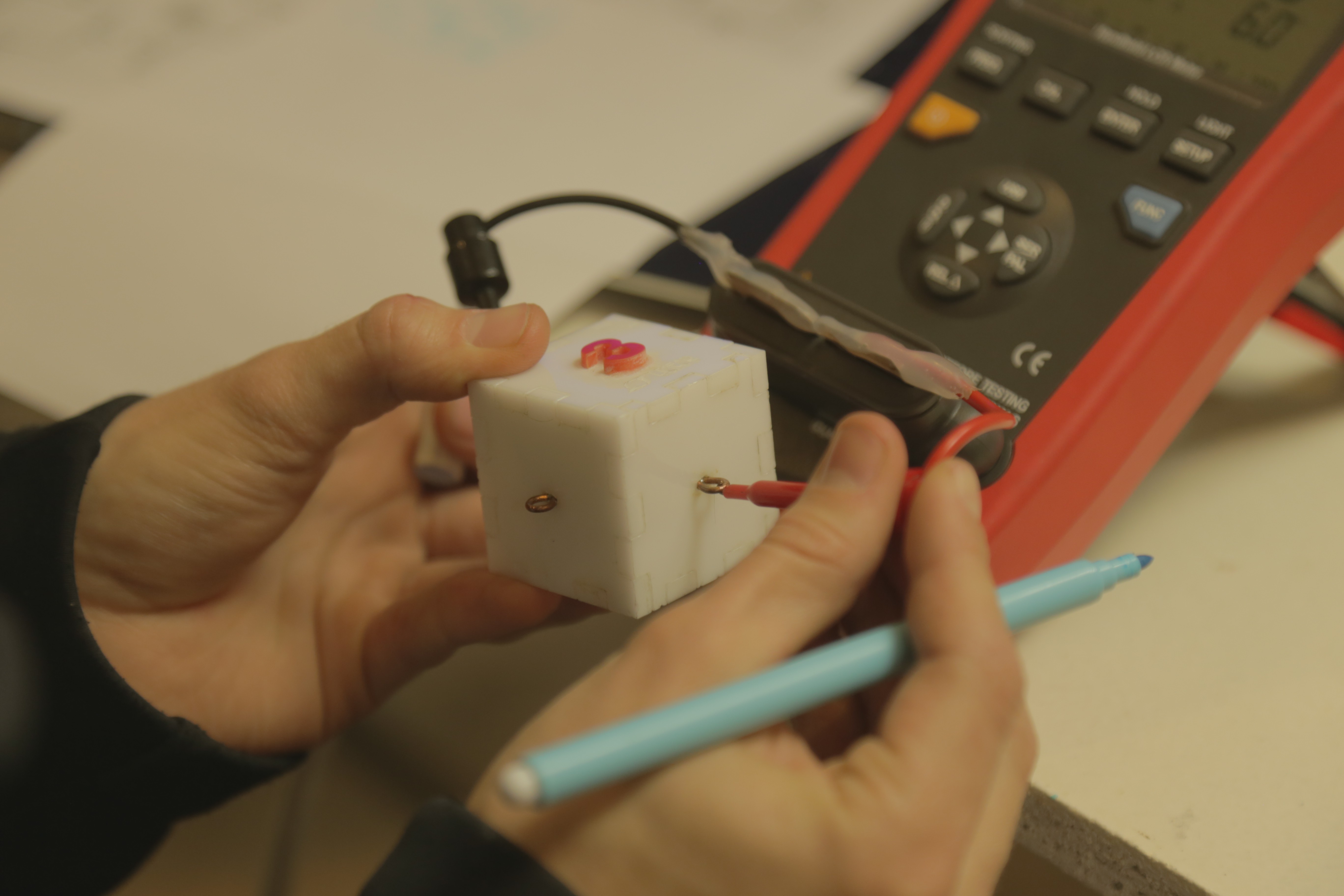
Probing the cubes
#frustration
#success
Second day, close to the finish line
Some young visitors
-
Speed typing
11/09/2016 at 03:59 • 0 commentsChallenge 23: SPEED TYPING 1
A mechanical keyboard, a Raspberry Pi and a widescreen monitor seem to make a nice speed typing contest rig when put together.![]()
Challenge 24: SPEED TYPING 2 RETRO EDITION
![]() Same idea - but with a typewriter which was converted from printing on paper to sending keystrokes over USB just a day before the challenge. Not as easy as with a mechanical keyboard, that's for sure.
Same idea - but with a typewriter which was converted from printing on paper to sending keystrokes over USB just a day before the challenge. Not as easy as with a mechanical keyboard, that's for sure.Here are both speed typing rigs - notice how even the chairs are matching?
-
Reverse-engineering
11/09/2016 at 03:52 • 0 commentsChallenge 17: CIRCUMVENTING ACCESS CONTROL
![]()
Put a marked card on the reader and a tune plays from inside the box the wires from the reader go to. Make it play this tune without using the marked card.
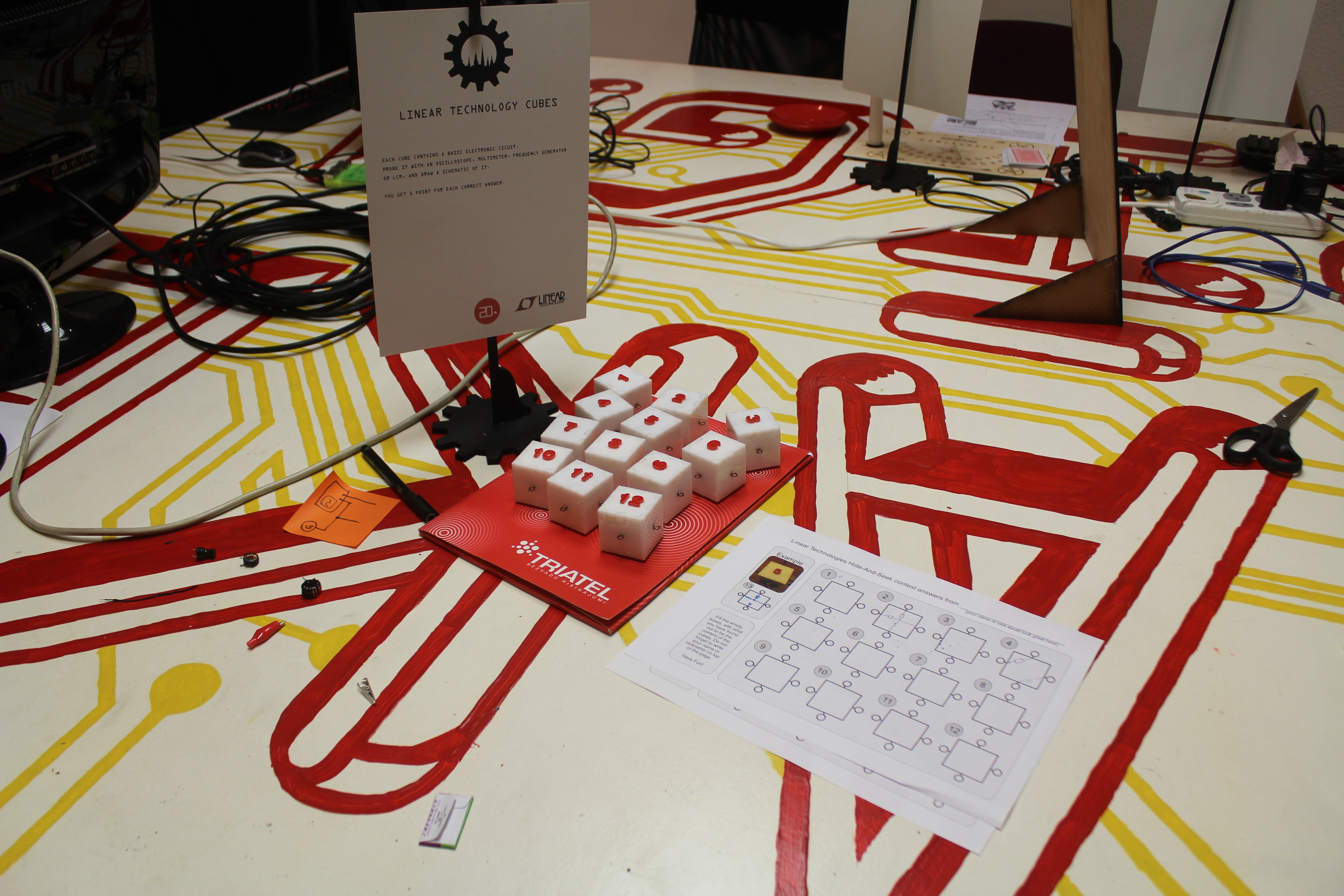
Challenge 20: LINEAR TECHNOLOGY CUBES
![]()
Acrylic cubes are glued shut and each has 4 hooks on the sides. Legends say there are various electronic components inside connected to the hooks - it's up to you to figure out the exact contents of each cube.
Challenge 28: SECRET FLASH
![]()
You've got a piece of PCB with an SPI flash soldered on. Can you read anything from the flash at all, for a start?
Challenge 30: CAPTCHA AND HTTP SECURITY
![]()
A webpage asks you to solve a mathematical problem, fill in your name and solve a captcha. One small problem - you've given one second to do it all. Can you type quickly enough? ;-)
Challenge 33: F17NESS P3OPL3
![]()
While we all were having fun, a guy was trying to reverse-engineer a MCU - to be exact, dump firmware from it, and since the next room was full of hackers, why not write a cry for help in l33tspeak since that's what they understand the best? The guy didn't get much assistance in the end, but the challenge paper did reportedly waste a lot of time for people trying to at least understand what the fuck this all meant.
-
WiFi, DNS, IoT, NTP...
11/09/2016 at 03:38 • 0 commentsChallenge 7: HIPSTER IOT CLOCK
An ESP clock with an OLED, which seems to deserve the "HIPSTER" tag. Of course it uses NTP, why wouldn't it? And why wouldn't you make it skip the time a little bit forward if the task says so?![]()
![]()
Challenge 16: BLEEDING HEART BANK
![]()
Gotta peek in some server's memory contents once in a while, ya know? Especially if it's a bank, that makes all that basement dwelling worth a life wasted.
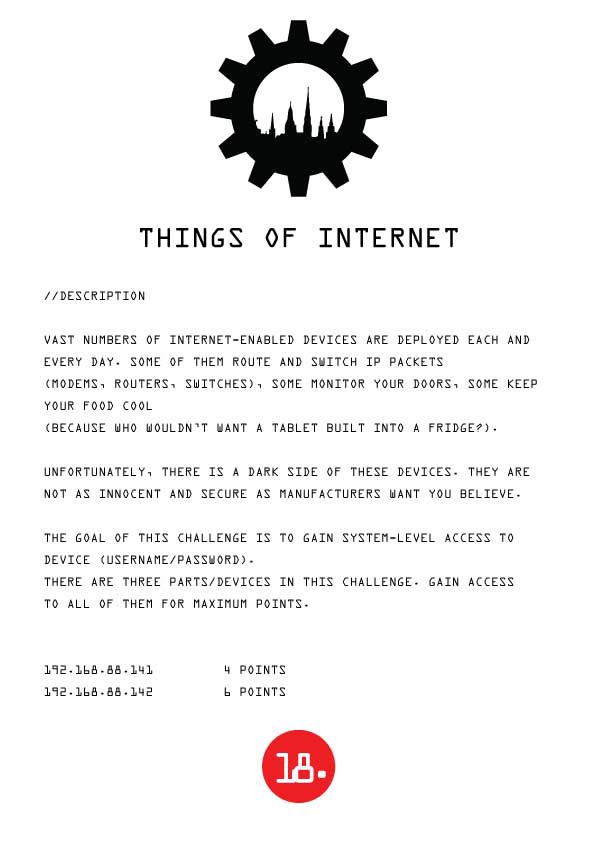
Challenge 18: THINGS OF INTERNET
IoT is this year's fad. Sadly, good passwords never were. Can you crack whatever we've set up?![]()
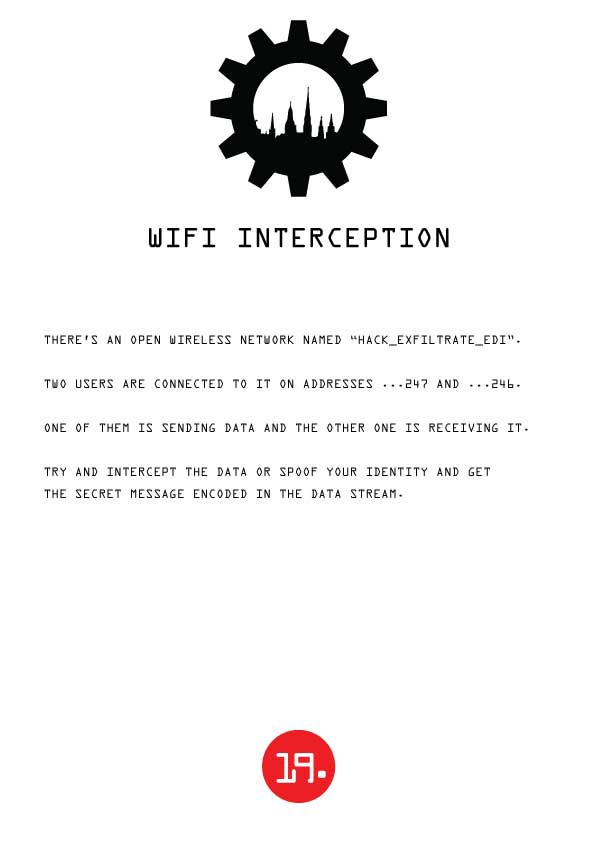
Challenge 19: WIFI INTERCEPTION
![]()
Two devices are communicating on an unsecured wireless network. What could go wrong? Hint: it's you impersonating one of them to see what secrets they're passing to each other.
Anybody can guess which Pi is that from this photo?
-
Binary cracking
11/09/2016 at 03:30 • 0 commentsChallenge 6: JAVA BREAKING
![]()
As much as I'd want to say Java is already broken, that's the challenge and you've got to get it done. .jar file provided - can't be sure it won't run malicious code on your computer, of course, but the idea of this event is to have fun and we gotta have sure you will.
Challenge 11: .EXE CRACKING 1
![]()
What will take you longer - downloading this executable or cracking it? Could go either way.
Challenge 12: .EXE CRACKING 2
![]()
Unless you have a really slow Internet connection, the answer to the previous question is no longer "downloading".
Challenge 13: .EXE CRACKING 3
![]()
One more. Unless you've been there before, good luck to you. Oh whatever, you'll need that anyway.
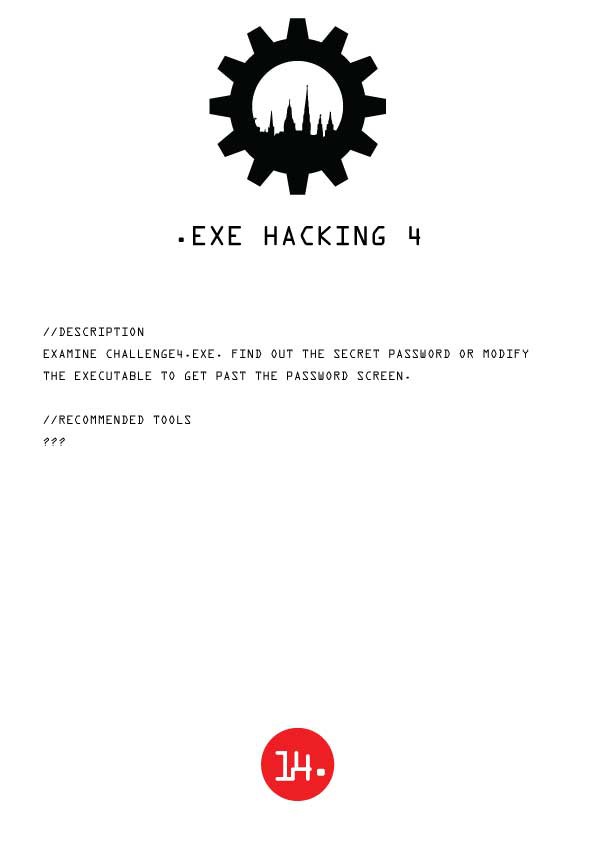
Challenge 14: .EXE CRACKING 4
![]()
Wizardry expected.
-
Social engineering and tamper protection circumvention
11/09/2016 at 03:22 • 0 commentsChallenge 2: PROBLEMS WITH YOUR PC?
![]()
It's hard enough to configure a computer, it's even harder to get someone to assist you. Fortunately, there seems to be a steady supply of people promising to solve all of your computer woes with just the right amount of money deposited into their bank account, after which you're going to get access to their exclusive piece of crap PC speed up tools, 0.5/2 assistance (as opposed to 24/7), as well as a feeling of money not so well spent. If you can call one of those guys and tick all of the boxes in our "Scammer bingo" sheet, you deserve all of the hacker cred for entertaining the public, as well as up to 10 points in our challenge.
Challenge 22: DUMPSTER DIVE
![]()
Ever thought of those guys FBI employs to sit and recover shredded documents all day long? Now you can feel like one by doing this tedious job for us (and we save a lot of money). Can you recover the document and get the information you need or are you going to quit after your breathing sends pieces of paper flying across the room for the tenth time?
Pictured: a template of the page we had, one of bags with paper that was supplied to people and two successful attempts at solving this.
Challenge 26: THERE'S A BUG IN YOUR WARRANTY 1
![]()
Those stickers that leave glue and "VOID" all over your tech when you disassemble it? We've got a roll of those, and we want you to finally unglue one of them without ruining the sticker. Do you have the patience or are you going to fuck it up over and over?
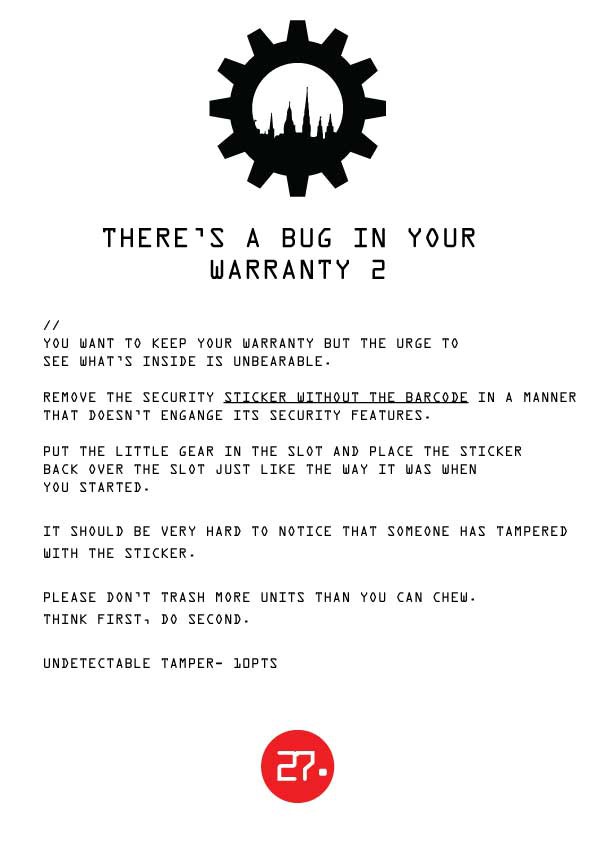
Challenge 27: THERE'S A BUG IN YOUR WARRANTY 2
![]()
We've got a roll of higher-grade antitamper stickers as well. Can you handle it?
Challenge materials - pieces of plastic with a gear-shaped cutout, an anti-tamper sticker covering the cutout from both sides and gears you need to insert inder the cutout. Those two pieces of plastics show the unsuccessful attempts at ungluing the sticker, as the white marks can be seen.
-
Lockpicking, wire&metal puzzles and chess
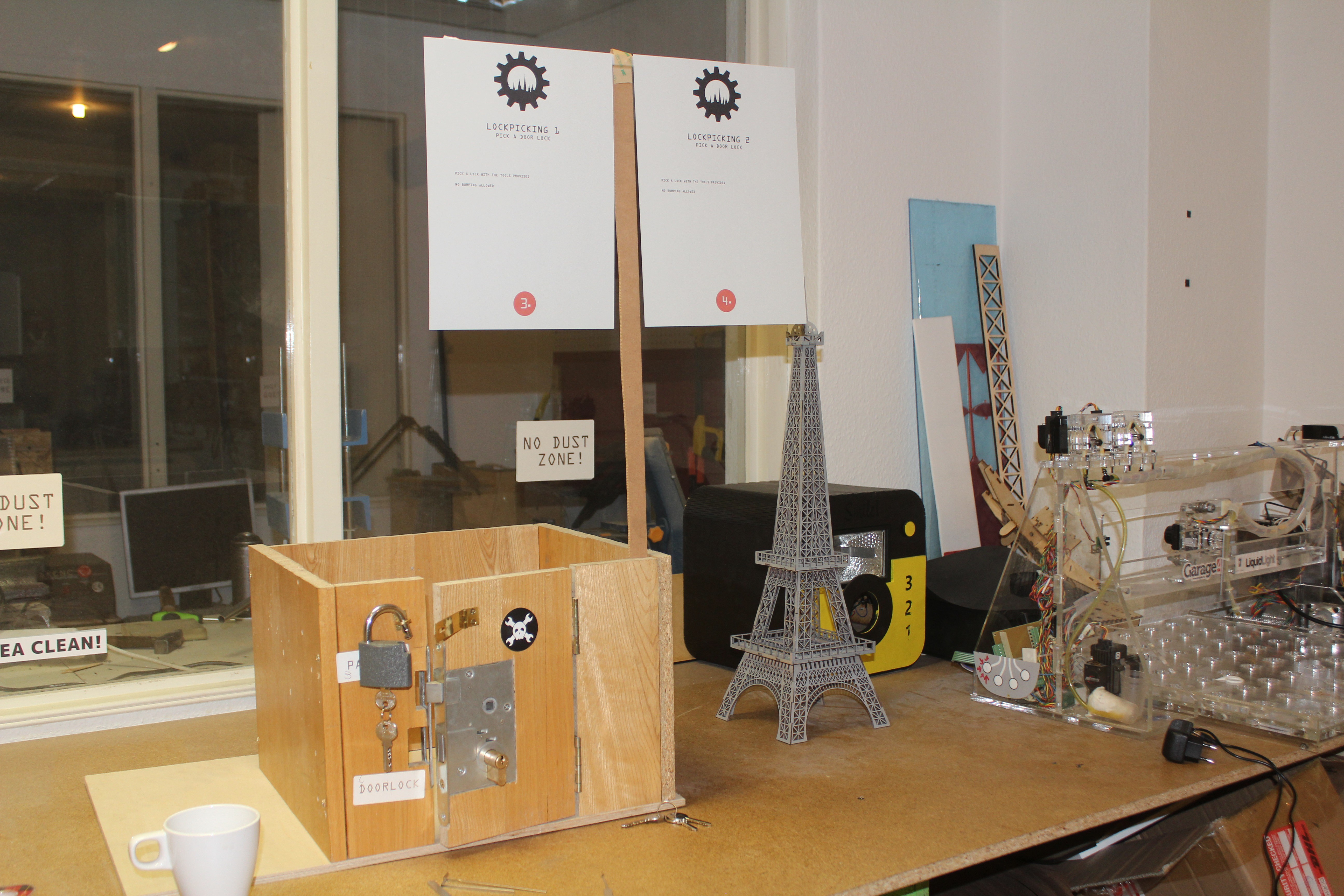
11/09/2016 at 03:08 • 0 commentsChallenge 3: LOCKPICKING 1
![]()
A set of lockpicks appeared right next to this padlock. Must've been magic, seeing as it's borderline legal to use them in our circumstances. At least we are sure we haven't seen who put them where they are.
Challenge 4: LOCKPICKING 2
![]()
The lock is the same old tumbler lock, just embedded in a door of a small drawer. Given that the drawer doesn't have a top wall, picking a lock seems to be an exercise in futility but what the hell, you wanna earn points or what?
Two locks in question in their natural habitat
Challenge 25: PUZZLES
![]()
Lots of them with different solutions. You can always consult the Internet when nobody's looking - ain't nobody stopping you from hacking the hacking challenge.
Challenge 2: PLYWOODCHESSBOX
![]()
Can you beat a piece of plywood at chess? Connect it to your computer, open your favourite serial terminal and find out!
![]()
-
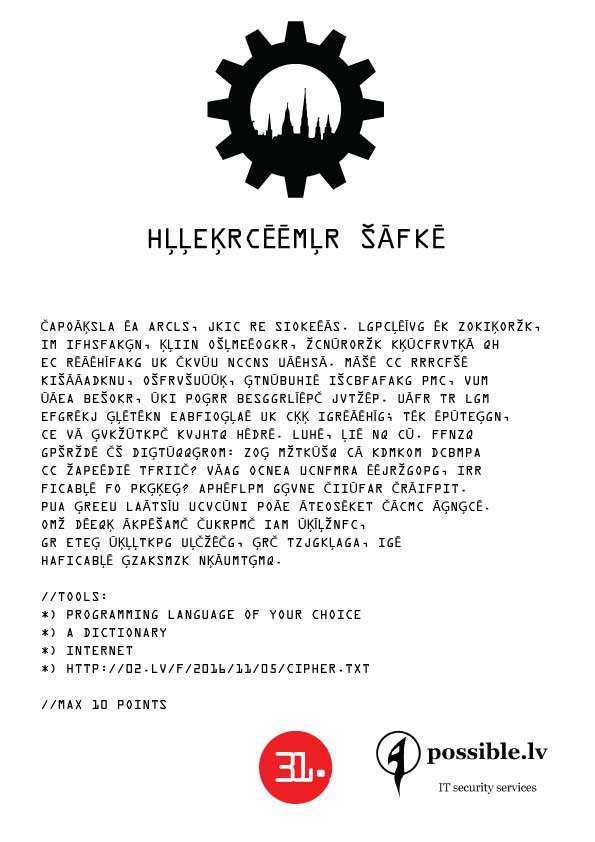
Cypher and steganography challenges
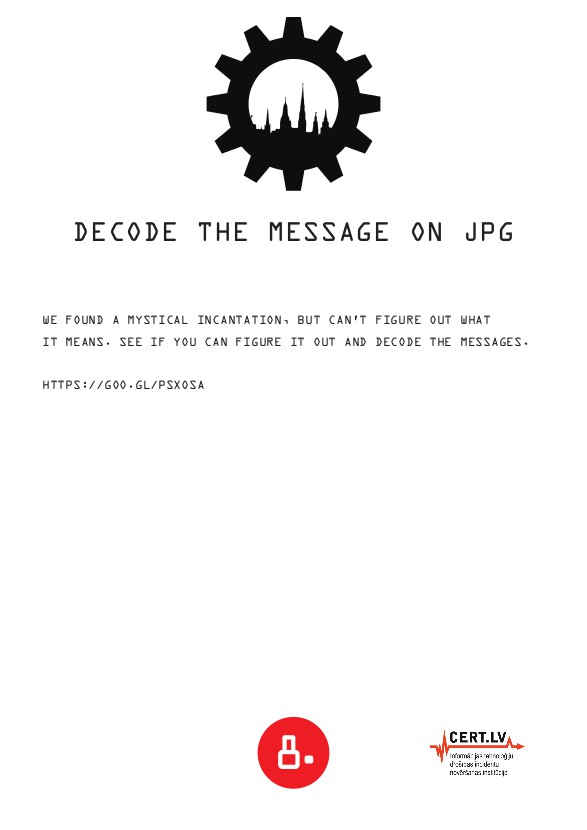
11/09/2016 at 03:02 • 0 commentsChallenge 8: DECODE THE MESSAGE IN JPEG
![]()
A link to a JPEG in question is written on the challenge paper (corrected to bit.ly/2f4aBsU ).
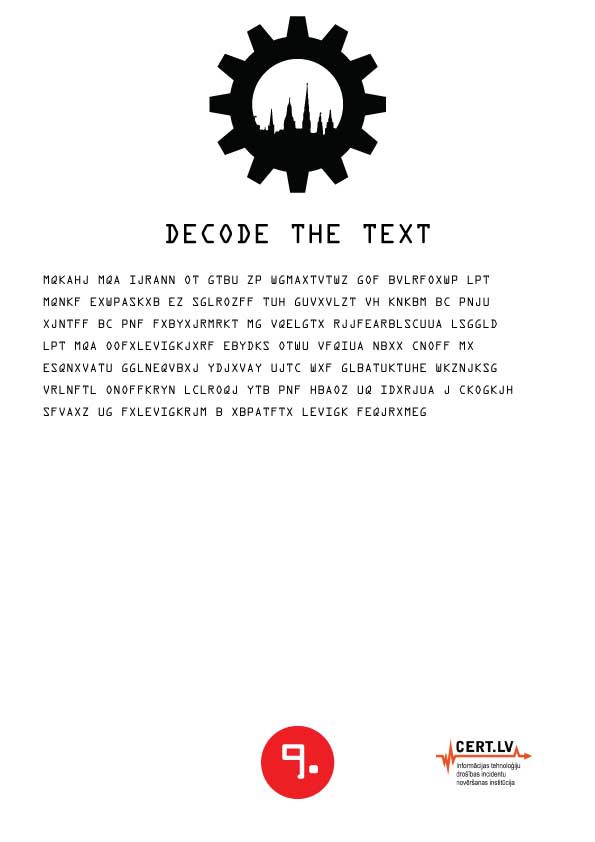
Challenge 9: DECODE THE TEXT
![]()
A piece of paper with gibberish printed on it. No instructions provided.
Challenge 10: TRAFFIC ANALYSIS
![]()
A link to a .pcap file seems to be all you need.
Challenge 21: THE LAST WISH OF GREAT K
![]() You have an Ouija board with a dish on it, a candle attached to the board and a stack of playing cards. There's nothing else that could tell you what the heck you're supposed to do with this.
You have an Ouija board with a dish on it, a candle attached to the board and a stack of playing cards. There's nothing else that could tell you what the heck you're supposed to do with this.
Challenge 31:
okay what the hell I don't have those characters on my keyboard
![]()
At least this one includes a link to the text so you don't actually have to type it on the keyboard as seemed to be the way with Challenge 9.
Challenge 32: HACK THE ENIGMA MACHINE
![]()
A PS/2 keyboard with erased letters, a 16x2 display and a healthy dose of hot glue. Can you type out the text so it looks exactly the same? Not as simple as it seems - the letters that you're supposedly typing never seem to match what appears on the screen.
-
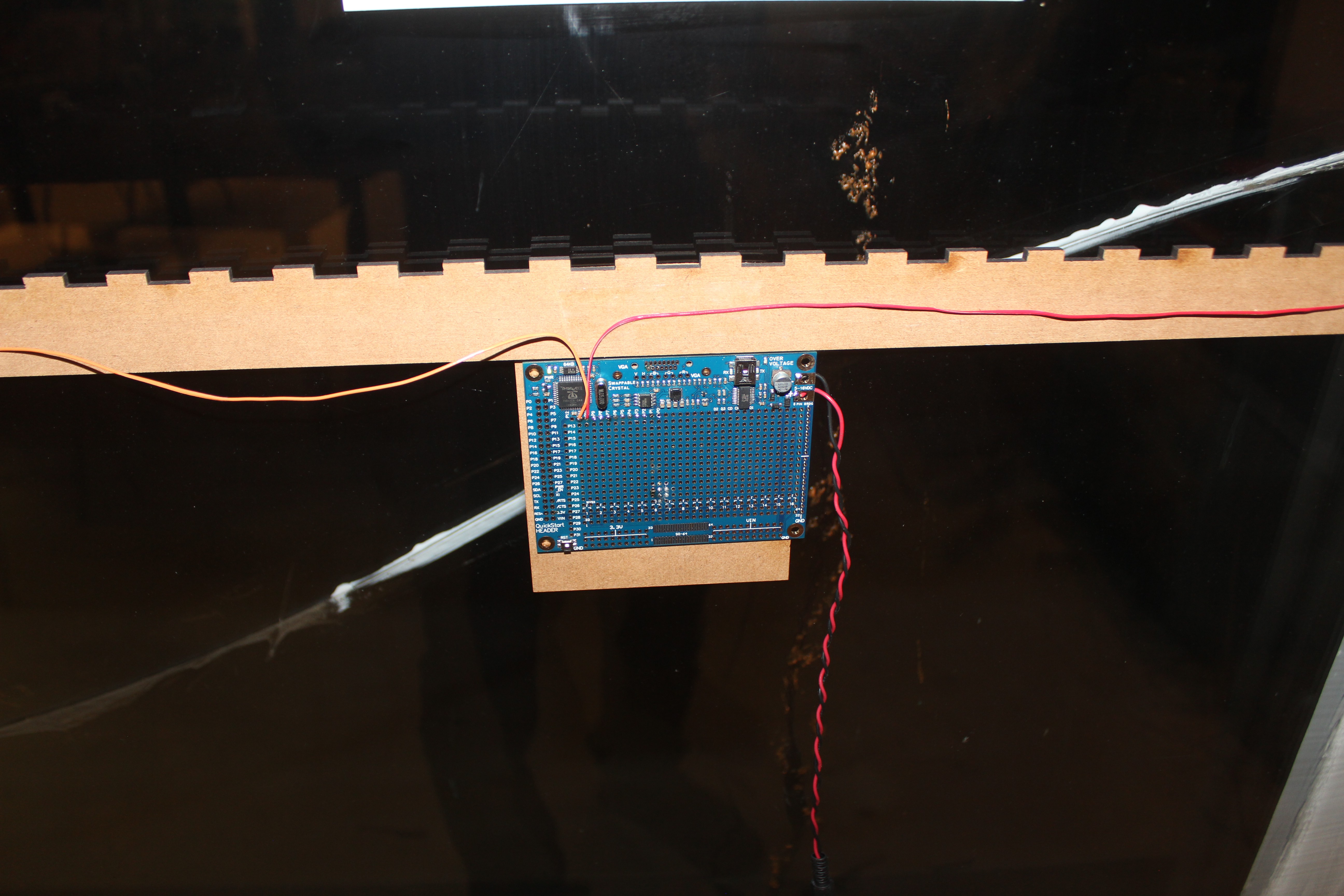
RF challenges
11/09/2016 at 02:43 • 0 commentsChallenge 1: RADIO PIRATES
![]()
Hardware - a Parallax Propeller board sending RF transmissions by wiggling pins (code not published).
Challenge 5: ZLRS TRANSMISSION SYSTEM
![]()
Hardware - a black box (made from white acrylic) with a button which seems to light up an LED inside. Nothing else is known except that the box has an antenna with "GSM" written on it.
Challenge 15: SDR BLACK BOX
![]()
Hardware - a black box (again, white acrylic) that allegedly contains some RF tech. No antenna visible, but there's a button and when you press it a red LED flashes inside.
Second challenge from top: SDR BLACK BOX
Third challenge from top: ZLRS
 Arya
Arya







 #frustration
#frustration  #success
#success 
 Some young visitors
Some young visitors
 Same idea - but with a typewriter which was converted from printing on paper to sending keystrokes over USB just a day before the challenge. Not as easy as with a mechanical keyboard, that's for sure.
Same idea - but with a typewriter which was converted from printing on paper to sending keystrokes over USB just a day before the challenge. Not as easy as with a mechanical keyboard, that's for sure.














 Pictured: a template of the page we had, one of bags with paper that was supplied to people and two successful attempts at solving this.
Pictured: a template of the page we had, one of bags with paper that was supplied to people and two successful attempts at solving this.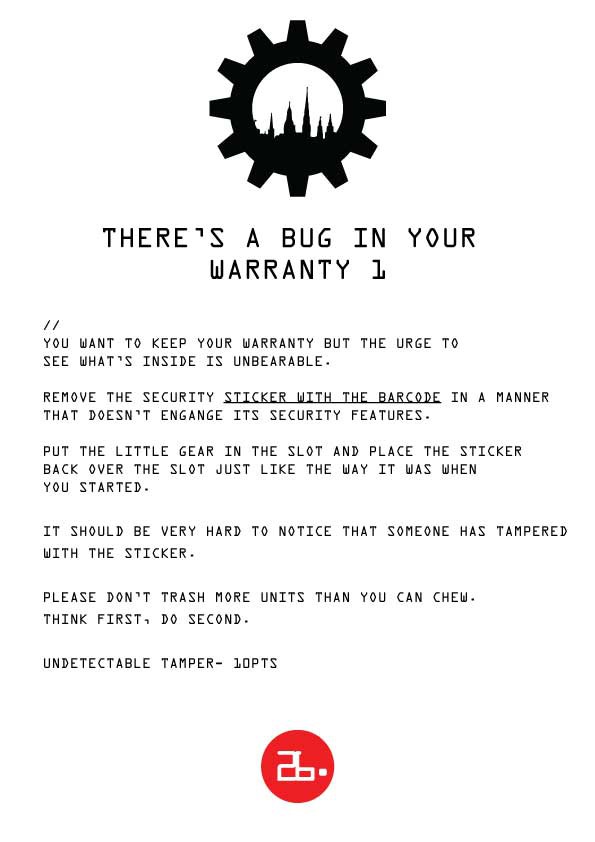
 Challenge materials - pieces of plastic with a gear-shaped cutout, an anti-tamper sticker covering the cutout from both sides and gears you need to insert inder the cutout. Those two pieces of plastics show the unsuccessful attempts at ungluing the sticker, as the white marks can be seen.
Challenge materials - pieces of plastic with a gear-shaped cutout, an anti-tamper sticker covering the cutout from both sides and gears you need to insert inder the cutout. Those two pieces of plastics show the unsuccessful attempts at ungluing the sticker, as the white marks can be seen.






 You have an Ouija board with a dish on it, a candle attached to the board and a stack of playing cards. There's nothing else that could tell you what the heck you're supposed to do with this.
You have an Ouija board with a dish on it, a candle attached to the board and a stack of playing cards. There's nothing else that could tell you what the heck you're supposed to do with this.