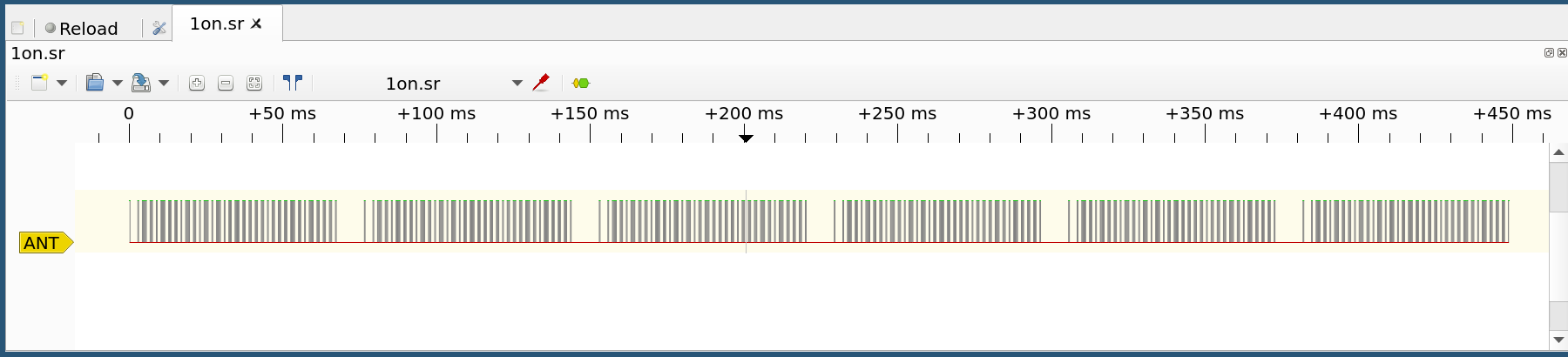
Step 1: Take a look at the data on Pulseview. There are 6 blocks of similar looking values.
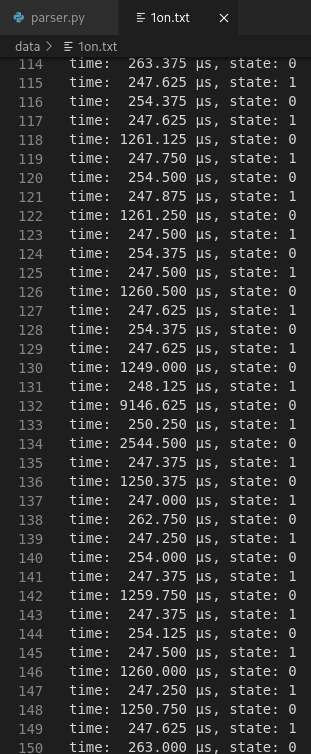
Step 2: I wrote a quick Python script to tell time spent on each state. Notice that the values are roughly 250 µs, 1250 µs, 2550 µs and 9150 µs
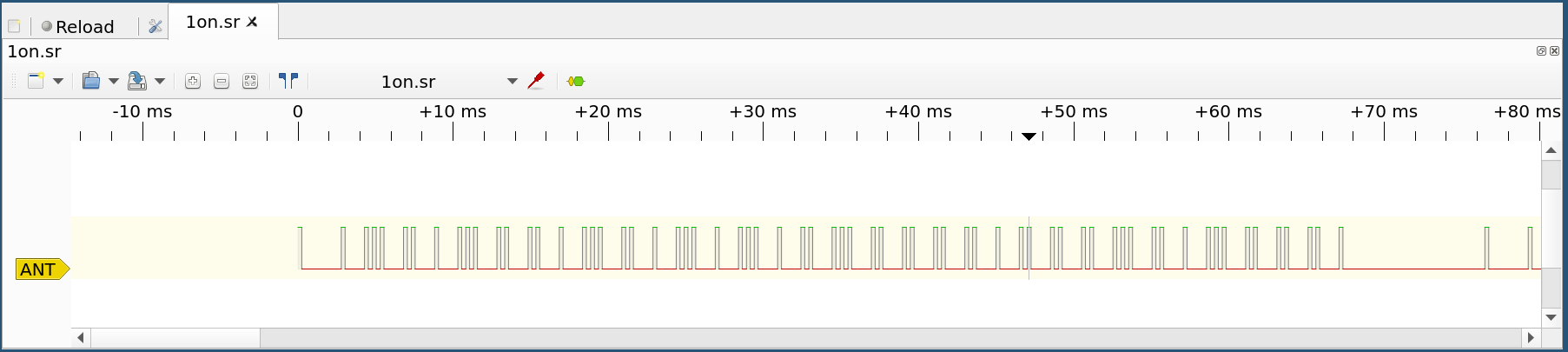
Step 3: This is a single data block which length is about 68 ms. Seems that the payload structure is 250 µs ON, 2550 µs OFF for initialiser bit. After that comes series of bits which are 250 µs ON, 250 µs OFF (or HIGH to LOW and 250 µs pause) for 0 and 250 µs ON, 1250 µs OFF (or HIGH to LOW and 1250 µs pause) for 1. Lets call the longer states -1 for now.
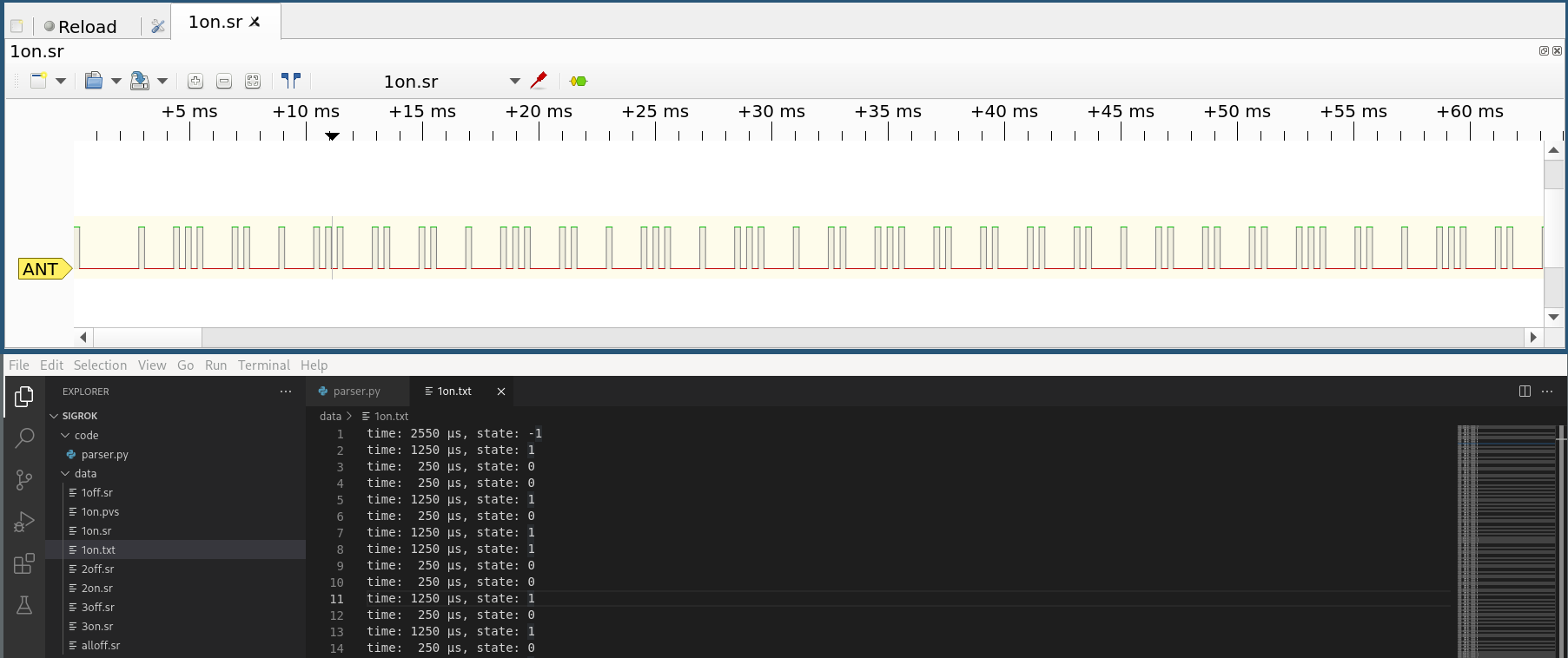
Step 4: Quick rewrite of the parser shows we are getting some decoded data.
Step 5: It is also easier to see that the payload is 65 bits transmitted 6 times in a row with a ~10ms pause in between
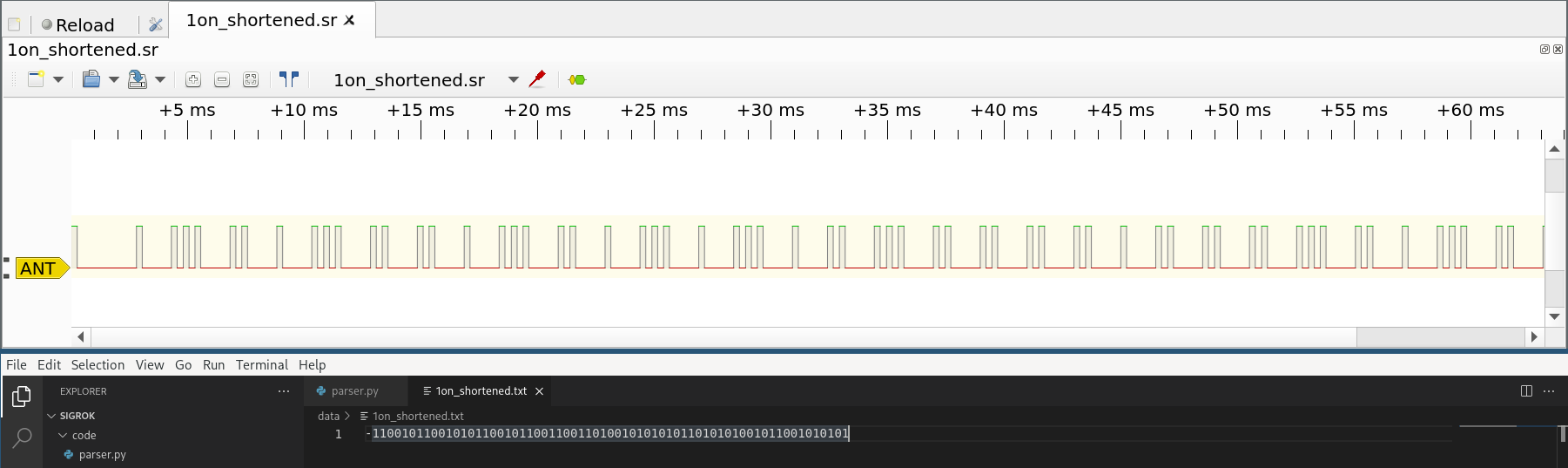
Step 6: Changed two lines from the parser and now we have a bit presentation of the payload. -1 is the longer initial bit, 1 and 0 are described above
 suikale
suikale
Discussions
Become a Hackaday.io Member
Create an account to leave a comment. Already have an account? Log In.