Warning: there is still a flaw with the connexion establishment protocol.
-o-O-0-O-o-
This protocol is symmetrical so it could be used for low to medium speed communication, for example user interfaces (keyboard/mouse/terminal), sensors, ... Or simply to link 2 CPU or MPU (most likely) even if they have no special HW/peripheral : 2×2 GPIO and you're rolling!
It uses 4 wires so it is comparable to SPI but the overall protocol can be richer (almost arbitrary) and bidirectional, since framing is controlled by each peer.
Compared to async serial ("RS232") :
- can be bit-banged with a basic microcontroller or even a computer (through the keyboard's LEDs ?)
- 4 wires (+GND) for everything, data as well as ACK
- no need for synchronisation, common clock, or speed negociation
- no need of deep FIFO
versus I²C :
- no funky FSM (that always gets a detail wrong)
- no damned analog trickery or limitation from open-collectors and pull-up resistors
- full duplex
Versus SPI :
- messages can be sent by any peer at any time, with arbitrary framing
-o-O-0-O-o-
Logs:
1. Basics
2. Higher level
3. Service messages
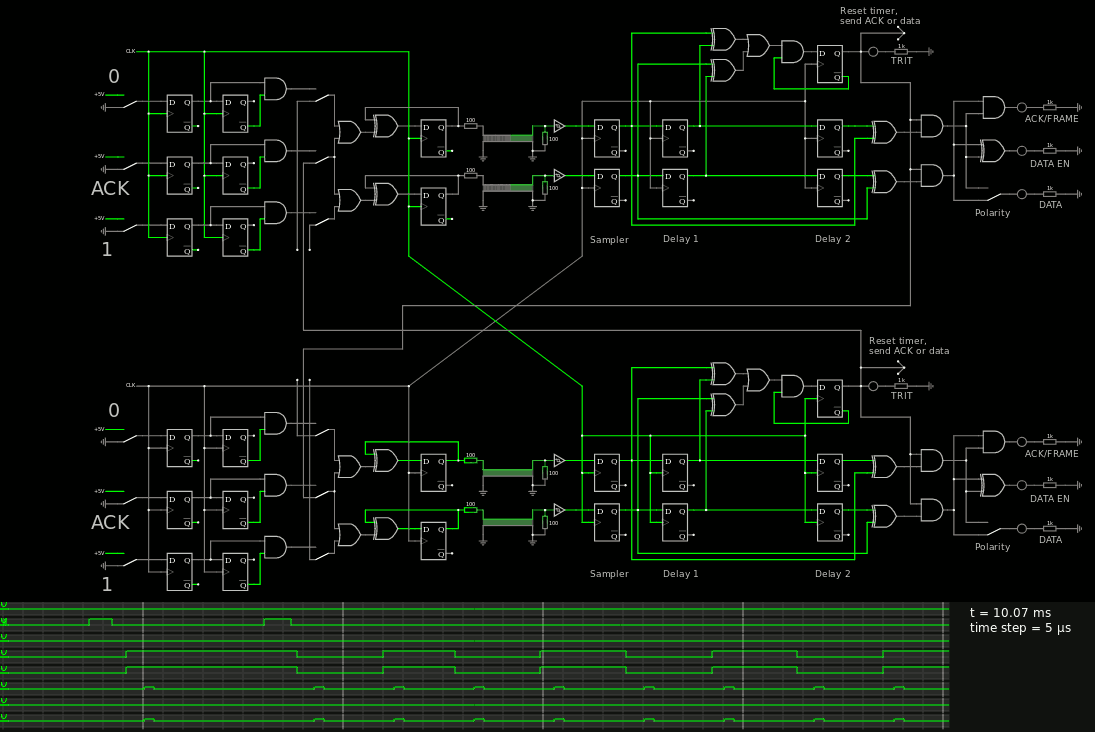
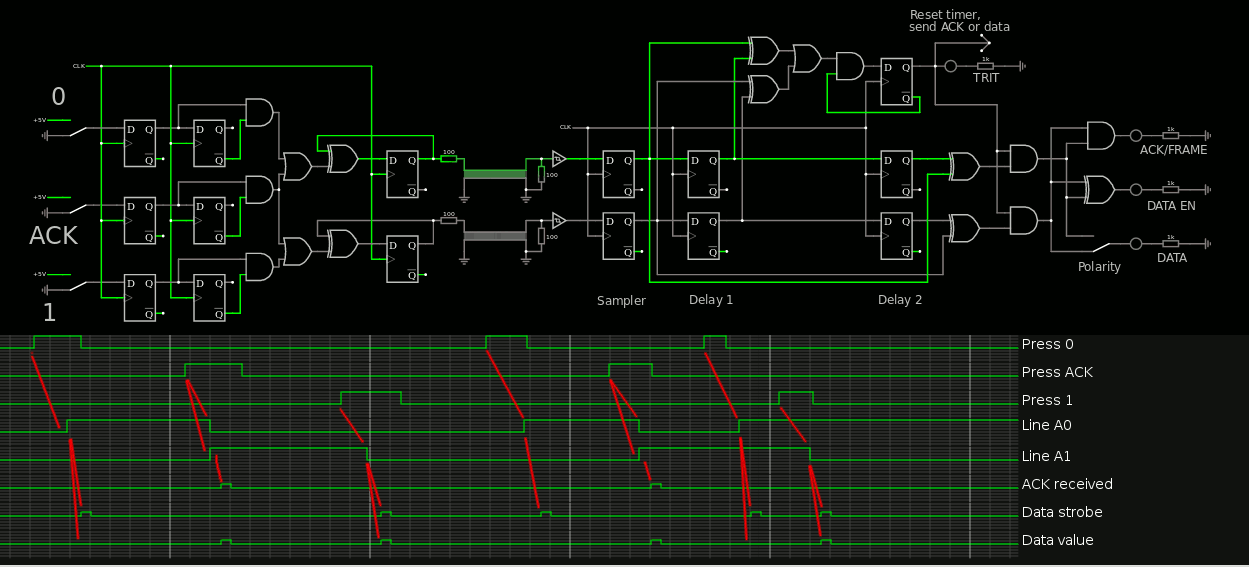
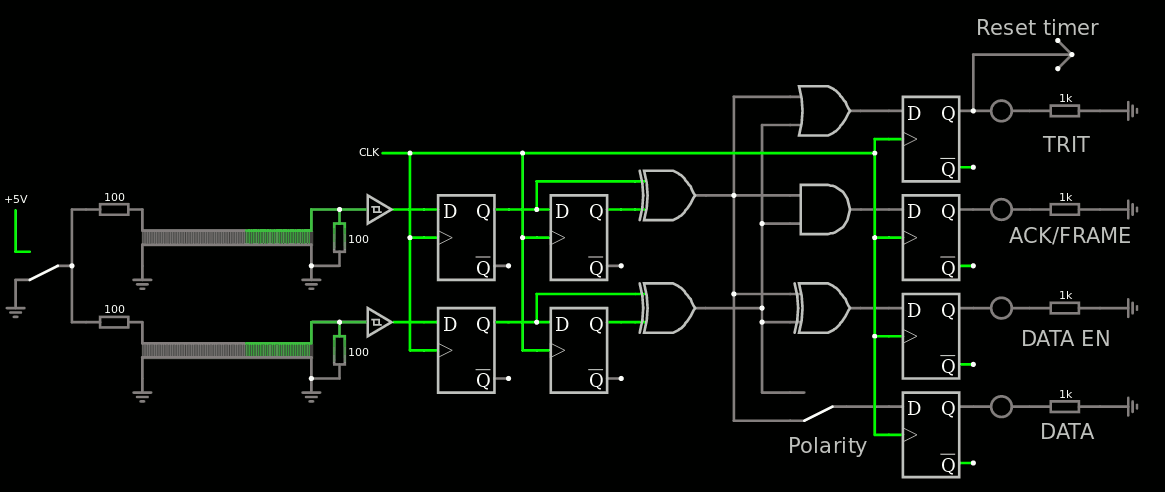
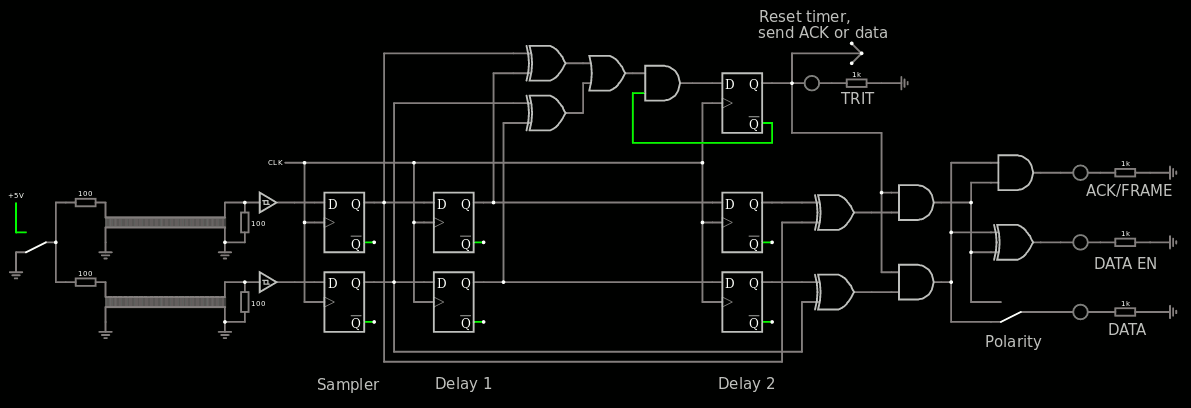
4. Basic receiver circuit and jitter tolerance
5. Basic sender and receiver
6. ACK ACK!
7. Software version
8. Finite State Machine
9. It's a ACK
10. Enhanced protocol
11.
.
 Yann Guidon / YGDES
Yann Guidon / YGDES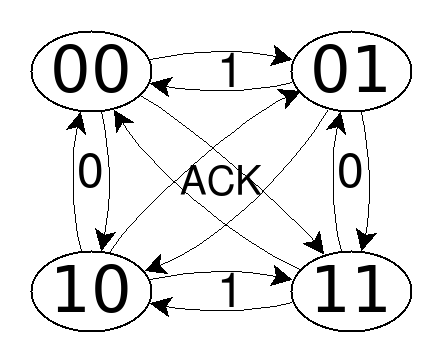



 spookymelonhead
spookymelonhead
 Jac Goudsmit
Jac Goudsmit
I looked again at the RPi's GPIO and... sigh.............
It only allows setting or clearing bits, not toggling, so the pins can't be changed simultaneously. This can create some problems...
I think there is also a parallel interface somehow/somewhere and that would be better.