Update: Now selling on tindie!
Update 2: Many thanks to Troed Sångberg who successfully built a PicoGlitcher. For his built, he made a parts list on Mouser which you can find in the project files.
Introduction
Voltage glitching attacks are a class of hardware attacks that exploit the vulnerability of electronic systems to sudden and brief changes in their power supply voltage. By intentionally introducing these abrupt voltage changes, or "glitches," attackers aim to disrupt the normal operation of the target device, causing it to malfunction in a controlled manner. This can result in the bypassing of security measures, corruption of data, or unintended execution of code. Voltage glitching is particularly relevant in the context of embedded systems, such as microcontrollers and smart cards, which are commonly used in secure applications including payment systems, access controls, and IoT devices.
The core concept behind voltage glitching is to induce faults at precise moments during the execution of critical operations within the device. These faults can lead to outcomes such as skipping security checks, extracting secret keys, or gaining unauthorized access to protected functions. The success of a voltage glitching attack relies on careful timing and an understanding of the target device's behavior under different power conditions. Attackers often use specialized equipment to generate and control these glitches with high precision, making this technique both sophisticated and powerful.
Previously featured projects
Glitching has been previously described on Hackaday for example here (everything you didn't know you need to know about glitching attacks) or here (Apple Airtags hacked and cloned with voltage glitching). The latter even describes attacking an Apple Airtag with a Raspberry Pi Pico and a mosfet.
Existing hardware
Usually these attacks are carried out by expensive hardware such as the ChipWhisperer Pro, the ChipWhisperer Husky, or the devices from Riscure. As these devices are typically very expensive (several hundred Euros), they are not accessible for the hobby hacker. The ChipWhisperer Husky is even more inaccessible for hobby hackers since it has long shipping times up to several weeks.
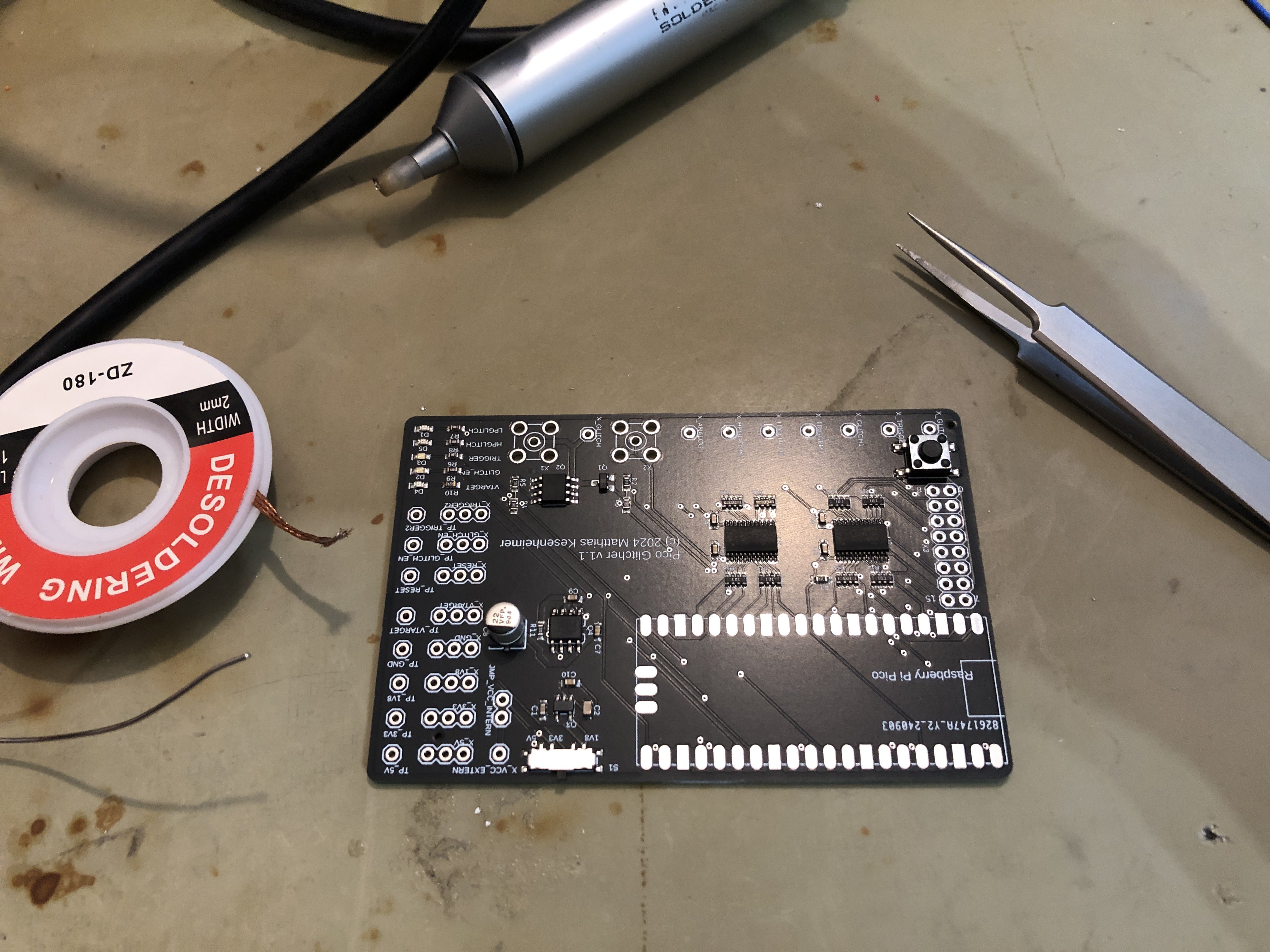
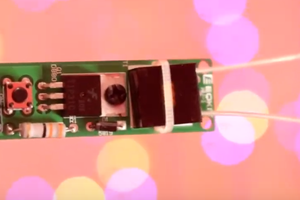
The PicoGlitcher
It turns out, however, that voltage glitching attacks can easily be performed with cheap and available hardware like the Rapberry Pi Pico and some other components. The sampling rate of the Raspberry Pi Pico is fast enough to enable attacks against most common microcontrollers like the ESP32 or STM32 processors. To gain more insight into voltage glitching attacks and using only cheap components, the PicoGlitcher was born.
The hardware required for the PicoGlitcher involves, of course, a Raspberry Pi Pico and additional components for precise voltage control and monitoring. Specifically, it includes a power supply capable of switching the target on and off, and crowbar transistors that can switch up to 66 amps. The design of the voltage glitching stage of the PicoGlitcher is exactly the same as found in the ChipWhisperer Pro. Furthermore, the board provides several different voltages to supply all kinds of different target boards. A built-in level shifter translates between the fixed voltages of the Raspberry Pi Pico and the voltage levels of the target board.
Glitches must be placed very precisely. The PicoGlitcher is able to trigger on various external events. For example, a rising or falling edge could be used to start the timers. Additionally, the PicoGlitcher can sniff on a UART communication and trigger if a specific word is sent.
To summarize:
- The PicoGlitcher is cheap (less than 30€) in comparison to professional equipment
- Various trigger capabilities: Rising or falling edge trigger, UART trigger, etc.
- Level shifters to trigger on signals with different voltage level.
- Low and high power crowbar mosfets to switch up to 66 amps.
- SMA connectors...
 Matthias Kesenheimer
Matthias Kesenheimer













 teardownit
teardownit
 fr.shirvan
fr.shirvan
Hi. I've been starting to learn about glitching a few months ago, glitching a cc2510 with a rppico clone ( https://gitlab.com/FTregan/cc2510glitcher ). The glitch works fine, 10-30 seconds only are needed ( I started from the knowledge shared in https://zeus.ugent.be/blog/22-23/reverse_engineering_epaper/ which uses a mosfet instead of analog switch and needed a few days).
Would you like support for cc2510 added or do you prefer to concentrate on the board and keep the mcu specific code out of the project repo ?