Technical Overview of the Hardware
The TP-Link TL-WR1043ND v1.8, released in the early 2010s, is a discontinued wireless N gigabit router designed for high-speed home and small office networks. At its core is a MIPS architecture powered by an Atheros AR9132 system-on-chip (SoC), clocked at 400 MHz. This processor, paired with 32 MiB of DDR RAM and 8 MiB of SPI flash storage, provides sufficient computational power for advanced networking tasks and custom firmware experimentation. The router supports the 802.11b/g/n wireless standards at 2.4 GHz, achieving theoretical speeds of up to 300 Mbps under ideal conditions, although real-world performance depends on environmental factors and antenna configuration.
Basic links
- TP-Link support: https://www.tp-link.com/en/support/download/tl-wr1043nd/v1/
- OpenWrt tech data: https://openwrt.org/toh/hwdata/tp-link/tp-link_tl-wr1043nd_v1
 yaluke
yaluke
 Cloud4RPi
Cloud4RPi
 tehaxor69
tehaxor69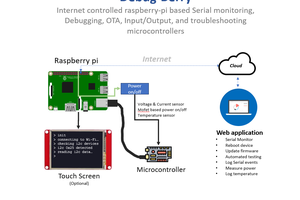
 Kaushlesh C. ( KD9VFU )
Kaushlesh C. ( KD9VFU )
 Robert Hart
Robert Hart