-
Pokemon go plus has arrived
09/05/2019 at 23:12 • 3 commentsToday
the pokemon go plus that I requested has arrived
I have proven that it is working correctly and now I have opened it
![]()
Tomorrow I will solder the necessary cables
![]()
![]()
see you tomorrow
-
Campaign in Donorbox completed!
09/04/2019 at 19:03 • 0 commentsHello everyone
I am pleased to announce that we have completed the donation campaign, I have already requested a Pokemon Go Plus, as soon as I receive it I will update these logs and upload all the information
thanks to the sponsors of the campaign, they will be the first to have access to the repository with the code, after that it will be public
Thanks!
-
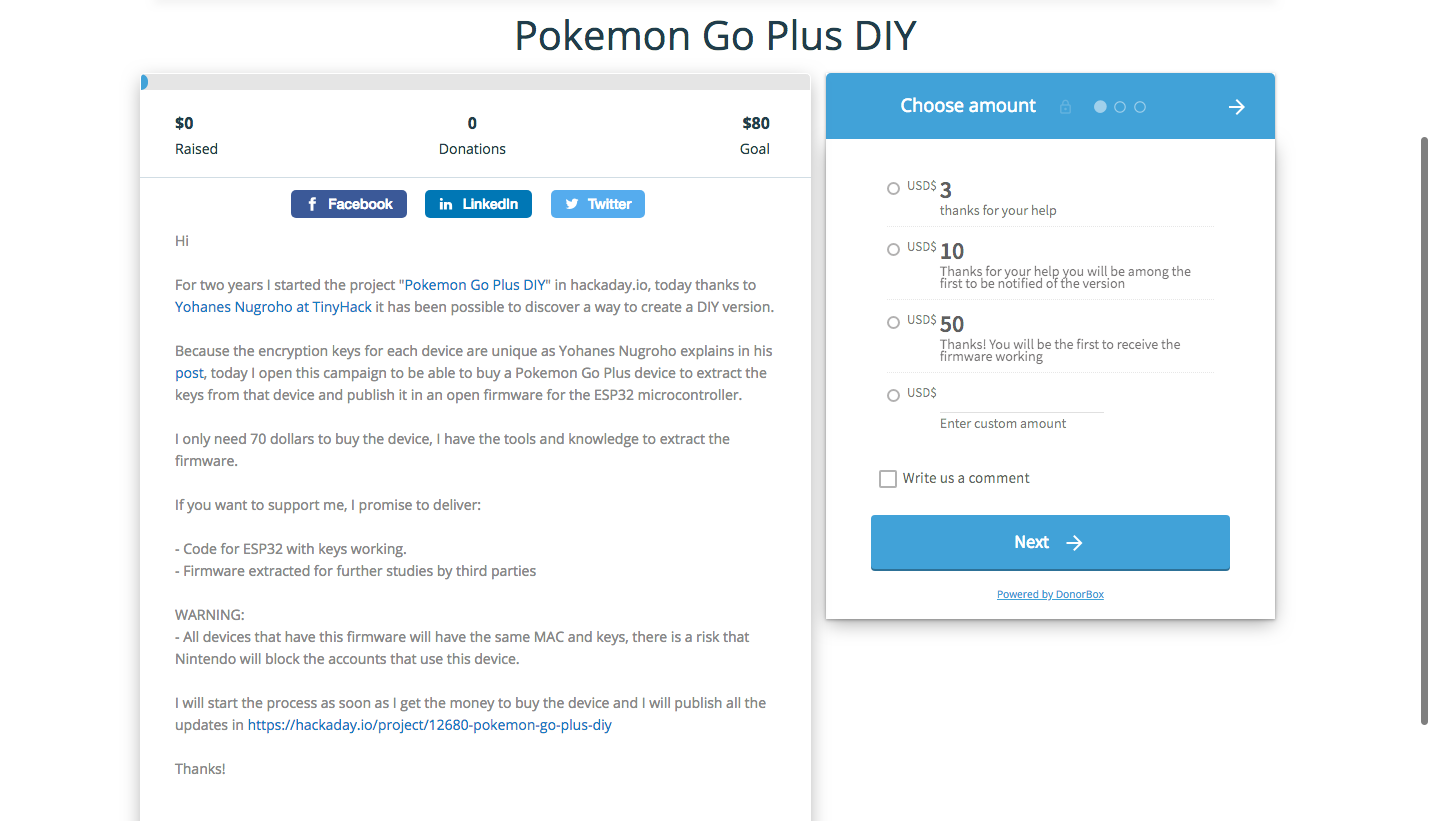
Donate for build our Pokemon Go Plus DIY
12/02/2018 at 20:14 • 0 comments![]()
Hi
For two years I started the project "Pokemon Go Plus DIY" in hackaday.io, today thanks to Yohanes Nugroho at TinyHack it has been possible to discover a way to create a DIY version.
Because the encryption keys for each device are unique as Yohanes Nugroho explains in his post, Today I open a campaign to raise money and buy a Pokemon Go Plus device to extract the keys from that device and publish it in an open firmware for the ESP32 microcontroller.
I only need $80 dollars to buy the device, I have the tools and knowledge to extract the firmware.
If you want to support me, I promise to deliver:
- Code for ESP32 with keys working.
- Firmware extracted for further studies by third parties
WARNING:
- All devices that have this firmware will have the same MAC and keys, there is a risk that Nintendo will block the accounts that use this device.
I will start the process as soon as I get the money to buy the device and I will publish all the updates in https://hackaday.io/project/12680-pokemon-go-plus-diy
If you want to donate from 3 dollars you can do it in the following link
-
Reverse Engineering Pokémon GO Plus
11/28/2018 at 05:00 • 0 commentsYohanes Nugroho at TinyHack writes about reverse engineering Pokemon GO Plus:
Pokemon GO Plus, (which I will refer from now on as PGP) is a wearable Bluetooth Low Energy (BLE) device to be used with the Pokemon GO game for Android or iOS. There have been many attempts to clone this device, but only Datel seems to figure out the algorithm, while the other clones are cloning the exact hardware and firmware.
I will explain the complete certification algorithm that I obtain from reverse engineering a PGP clone, and then I will explain how I did the reverse engineering and how you can extract your own blob and key if you want to clone your own device. I am providing a reference implementation for ESP32 so you can test this yourself.The article talks about the history of cloning and goes into great detail on the process. It does not discuss generating keys or the Bluetooth blob (as that would be proprietary to the company and could have Niantic ban someone’s account).
https://tinyhack.com/2018/11/21/reverse-engineering-pokemon-go-plus/
-
Pokemon Go Plus reverse engineering write up
01/19/2017 at 15:53 • 0 commentsThe user in reddit BobThePigeon_ to writing an excellent research on the work of the PGO +
https://www.reddit.com/r/pokemongodev/comments/5ovj04/pokemon_go_plus_reverse_engineering_write_up
Within your work we can find the certification process
Certification process
Current attempts to produce a DIY Pokemon Go Plus have been blocked by a certification process. The device and app will send random data (the "challenge") to each other, and the other side must respond with the correct response in order to certify the app and device as being genuine. Here is what is transacted during the certification (compare with this):
- Device sends 36 bytes: 03000000 + 32 random bytes to SFIDA_TO_CENTRAL, this is a certification challenge; the device is checking that the app is genuine.
- Device sends 4 bytes: 03000000 to SFIDA_COMMANDS, this will notify app
- App sends a response which is 20 bytes: 04000000 + 16 response bytes to CENTRAL_TO_SFIDA.
- Device sends 4 bytes: 04000100 to SFIDA_COMMANDS to notify app that it has received the response.
- App sends 36 bytes: 05000000 + 32 random bytes to CENTRAL_TO_SFIDA, this is a certification challenge; the app is checking that the device is genuine.
- Device sends a response which is 20 bytes: 05000000 + 16 response bytes to SFIDA_TO_CENTRAL.
- Device sends 4 bytes: 05000000 to SFIDA_COMMANDS to notify app that it has responded to the certification challenge.
- App sends 5 bytes: 0300000001 to CENTRAL_TO_SFIDA
- Device sends 4 bytes: 04000200 to SFIDA_COMMANDS
By using a combination of static analysis and debugging, I have determined the algorithm used to generate a certification response from a challenge:
- Split the 32 challenge bytes into two 16 byte halves.
- Encrypt the first 16 byte half using AES-128, using the key bda885742bc53918793ade3fa7b6cf3b.
- Take the encrypted result and XOR it with the second 16 byte half. This gives the response.
Here are some test vectors, obtained from a real device: challenge = 7526c9257080ec4b6366635b0ee5416324673e610d38d7f2440662b272db041f leads to response = 2445be74030f584a7a01fa26490a902e, challenge = 5035fb9119b5bb9de2f4f76803fef5152543b95e02c8791c69fb393215418aa5 leads to response = 78393cb801cd71e17ea977bb1c31acd3.
Thanks BobThePigeon_ -
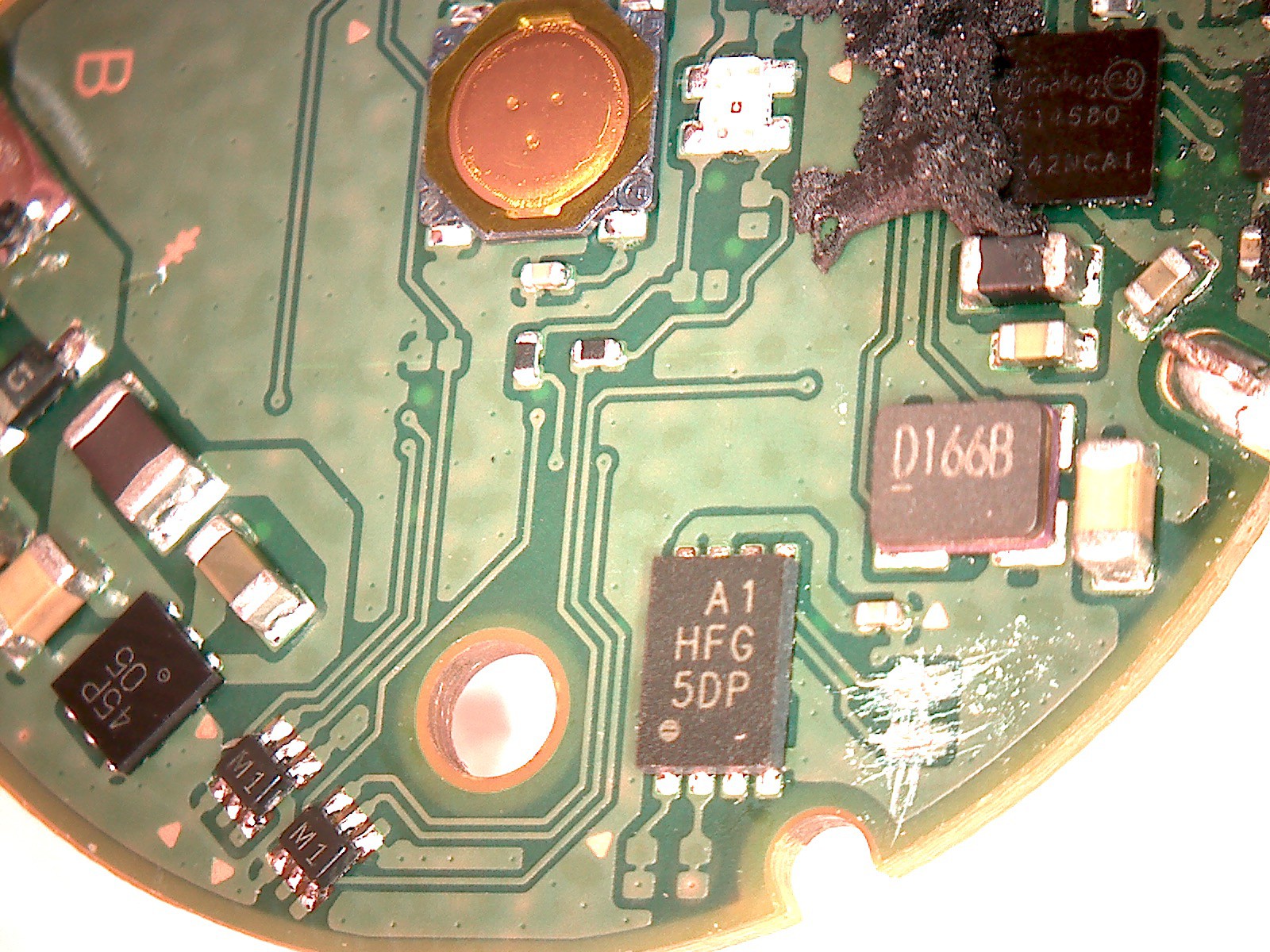
Hardware Teardown
09/16/2016 at 18:37 • 8 commentsThere are 3 non standard screws in the case. If you don't have tools like me. You can scratch of coating, add some flux and add a drop of very hot solder quickly so you don't melt plastic underneath. Then you can solder a pin header to unscrew it easily. You can clean solder and cut a slot for further assemble and disassemble.
![]()
There isn't a lot parts in side. I haven't investigated much but I think there is a PMIC, a SPI flash and DA14580.
![]()
The good thing is all SPI flash pins are exposed. You can even cut the trace to isolate it. This makes it easy to dump the firmware from this flash chip.
![]()
I suppose the encryption can be hacked by static analysis or move the firmware to a dev board for debugging.
-
Start conversation between App and BLE device
09/14/2016 at 08:13 • 7 commentsAfter installing 0.37 update we can use Pokemon Go plus. However there is a certification protocol before we can connect homemade hardware to Pokemon Go App. Here is my experiment on trying to mimic a real Pokemon Go plus.
1. Make sure the BLE device can bond with Android device. The device must support paring.
2. Make sure the UUID_SFIDA_COMMANDS characteristic has NOTIFY property. The Pokemon Go App will not read anything from BLE device until there is a notification
3. Don't try to reply with by hand with a BLE tool such as "LightBlue", you only have about 10 seconds.
The following info is the communication between App and device
1. Device starts advertisting
2. App connects to device
3. App pairs with device
4. App setups notification on SFIDA_COMMANDS
5. Device writes 3,0,0,0 (SFIDA_RESPONSE_CERTIFICATION_NOTIFY) to SFIDA_TO_CENTRAL and SFIDA_COMMANDS, this will create a notification to App
6. App reads SFIDA_COMMANDS then SFIDA_TO_CENTRAL
7. App writes 4,0,0,0 to CENTRAL_TO_SFIDA
8. Device writes 4,0,1,0 (SFIDA_RESPONSE_CERTIFICATION_CHALLENGE_1) to SFIDA_TO_CENTRAL and SFIDA_COMMANDS, this will create a notification to App
9. App reads SFIDA_COMMANDS then SFIDA_TO_CENTRAL
10. App writes 5,0,0,0 + 32byte (36 bytes total) random data to CENTRAL_TO_SFIDA
11. Device writes 5,0,0,0 (SFIDA_RESPONSE_CERTIFICATION_CHALLENGE_2) to SFIDA_TO_CENTRAL and SFIDA_COMMANDS, this will create a notification to App
12. App reads SFIDA_COMMANDS then SFIDA_TO_CENTRAL
13. App writes 3,0,0,0,3 to CENTRAL_TO_SFIDA
14. Device writes 4,0,2,0 (SFIDA_RESPONSE_CERTIFICATION_NOTIFY)) to SFIDA_TO_CENTRAL and SFIDA_COMMANDS, this will create a notification to App
15. App reads SFIDA_COMMANDS
16 App disconnects immediately
-
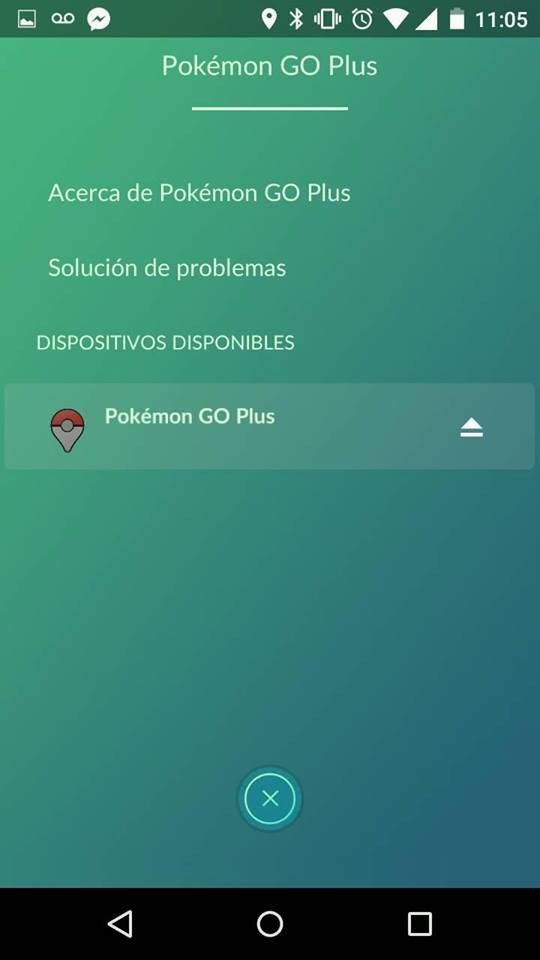
App version 0.37 added support PGO+!!
09/11/2016 at 16:16 • 0 commentsYesterday published the latest version 0.37, which already include support PGO+, and good news the DIY version is detected by the application :D
![]()
-
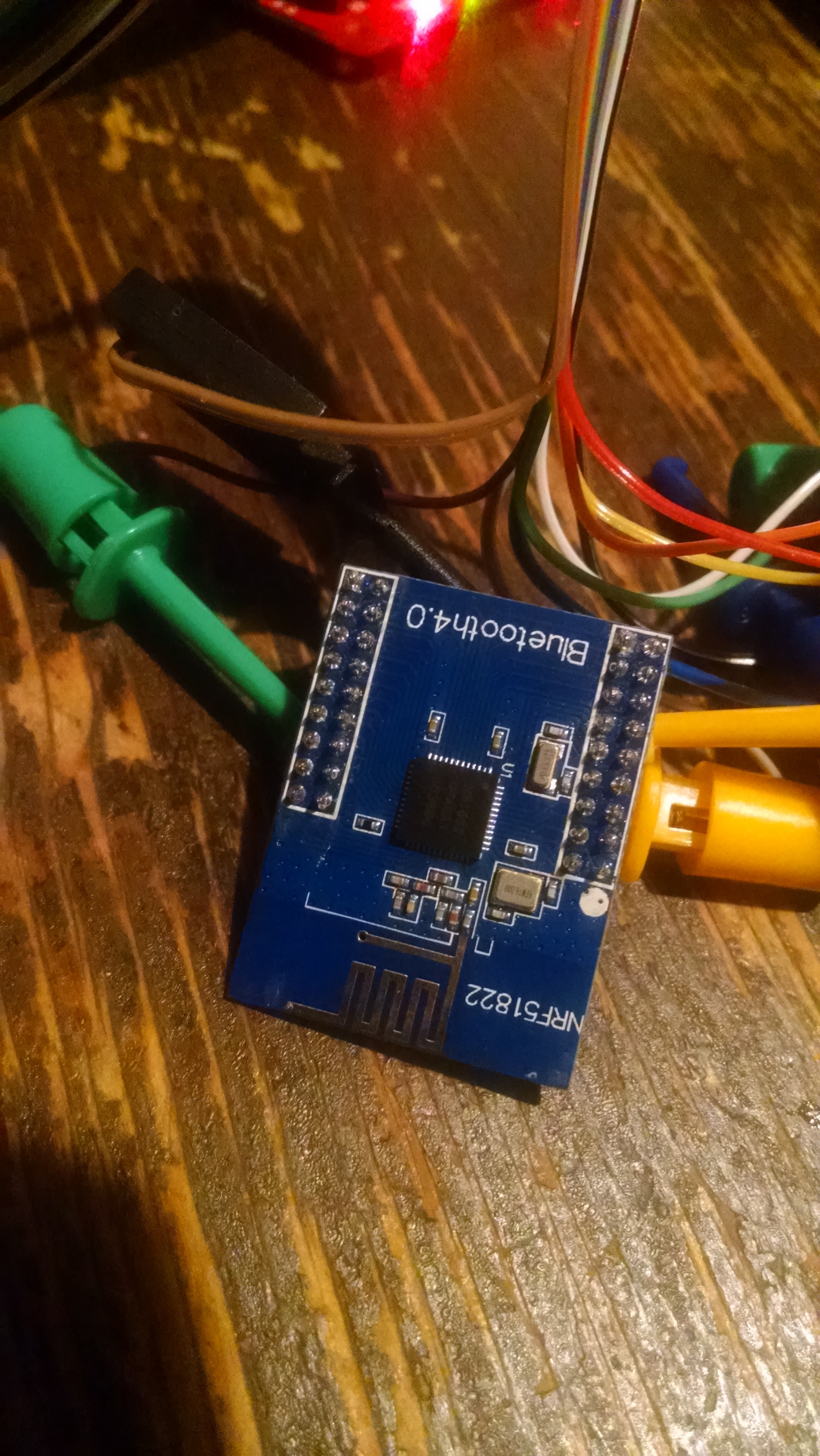
Working in nRF51822
08/22/2016 at 13:10 • 0 commentsI managed run in module BLE nRF51822, thanks to the project nRF5 Arduino Core
https://github.com/sandeepmistry/arduino-nRF5
and the branch nRF5 of the library arduino BLEPeripheral
https://github.com/sandeepmistry/arduino-BLEPeripheral/tree/nRF5
You can get a module nRF51822 in Alixpress for less than $7 dollars
![]()
![]()
We continue to expect the activation of Bluetooth in the application for testingThanks!
-
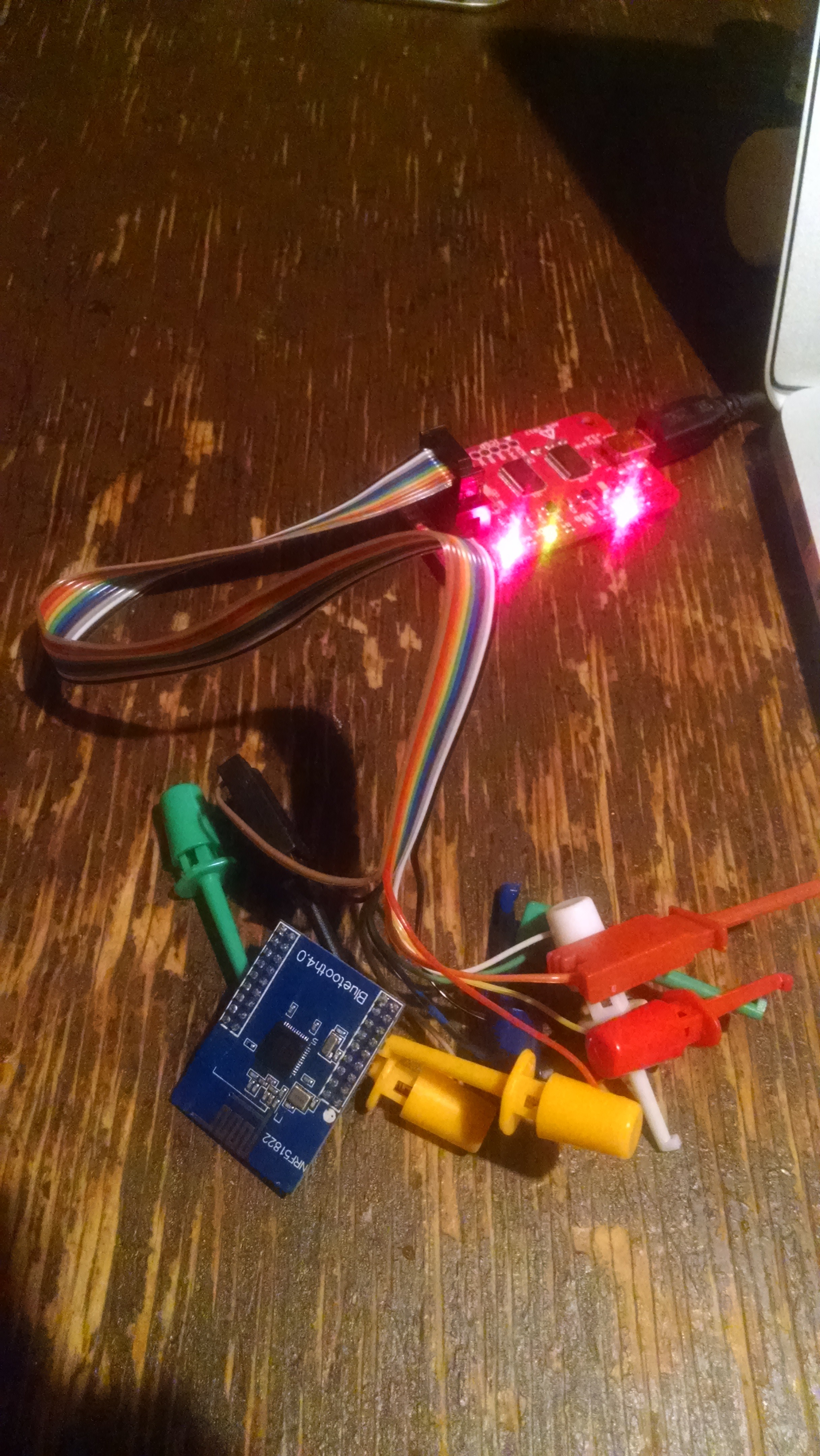
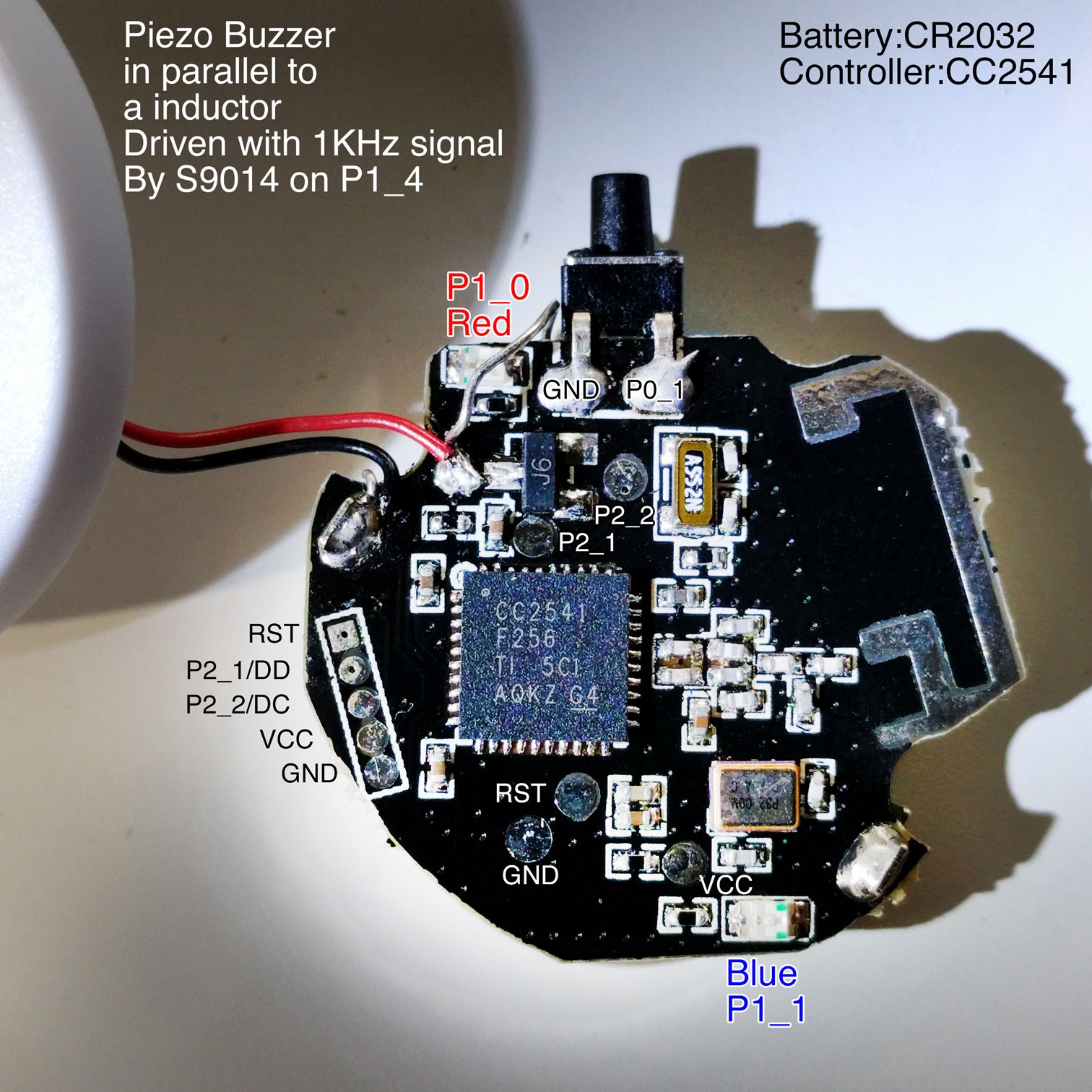
Working in version CC2541, Hack HAVIR HV-101 & HV-102
08/04/2016 at 12:47 • 4 comments@deqing tells us that he is working on a version for CC2541 and founded a interesting device to hack: HAVIR HV-101 & HV-102. It may be the only low cost BLE product with a reprogrammable controller.
It has a button, 2 LEDs, a buzzer and debug pads. That basically everything we need. I've put it's photo on https://github.com/DeqingSun/CC2541WristBandHack
![]()
Thanks @deqing
 Sabas
Sabas