-
CTF Results & Walkthrough (Part 4)
08/16/2020 at 05:56 • 0 commentsMORE FLAGS!!! WUT?!
The remaining flags were sprinkled throughout the internet, the badge, and other places throughout the year. Here's what you may have found or missed...I
Found code: PCB QR Code
Go ahead scan it...see what happens...
![]()
Found code: Twitter 1
https://twitter.com/ANDnXOR/status/1291615817440694272
Found code: Twitter 2
https://twitter.com/ANDnXOR/status/1291874479723827200
Found code: Twitter 3
https://twitter.com/ANDnXOR/status/1283615391504142336
Found code: Github
Do you watch our repository update status? Seems we pushed something to the DC24 badge a couple of months ago...Look at it in it's RAW form...
https://github.com/ANDnXOR/ANDnXOR_DC24_Badge/blob/master/README.md
Found code: About
Scroll to the bottom of the About section on the badge menu, it takes a while...
Found code: BASFUK.BAS
Did you think the Brainfuck interpreter was broken? Well yes it was, but if you fix the code compared to the original in MYBASIC samples...
Found code: POST
Take a close look in the Power On Self Test UART at start up. Normally you were on /dev/ttyACM0, this would be /dev/ttyACM1 (however its quick you may miss it). Better circumvent the RTOS providing middleware and just go directly to the UART breakout...on back... solder some RX, TX, and GND header pins
Found code: Scoreboard
Take a look at the source, there's a really weird comment...
Found code: Release Video
There's a secret in the TP. Can you find it?
Found code: Release Video
We sure do like floppy disks...
Found code: Release Video
Damn hipsters...
Found code: T-Shirt
Did you look closely at the Shirts or the Sticker Swag included? Check out the print on the black wire...
sOXMxT
In Closing...
This was probably the largest amount of challenges and easter eggs we've ever done in one of our CTFs. He'll getting some of the badges via drops (which is outside the scope of the CTF obviously) had tons of create juices behind the various drop proxies across the land of hax0r. All that being said to pull this off takes a village. The Matt Damon Village. With that, we will leave you with a view of the header code of BENDER so you can see behind the scenes how this worked. It will be posted to github, but in short the framework for BENDER was made generic and all challenge content is kept in a source file. Here's what it looks like. Enjoy this while we work on the overall project post mortem.
/***************************************************************************** * Made with beer and late nights in California. * * (C) Copyright 2017-2020 AND!XOR LLC (https://andnxor.com/). * * PROPRIETARY AND CONFIDENTIAL UNTIL AUGUST 11th, 2020 then, * * Licensed under the Apache License, Version 2.0 (the "License"); * you may not use this file except in compliance with the License. * You may obtain a copy of the License at * * http://www.apache.org/licenses/LICENSE-2.0 * * Unless required by applicable law or agreed to in writing, software * distributed under the License is distributed on an "AS IS" BASIS, * WITHOUT WARRANTIES OR CONDITIONS OF ANY KIND, either express or implied. * See the License for the specific language governing permissions and * limitations under the License. * * ADDITIONALLY: * If you find this source code useful in anyway, use it in another electronic * conference badge, or just think it's neat. Consider buying us a beer * (or two) and/or a badge (or two). We are just as obsessed with collecting * badges as we are in making them. * * Contributors: * @andnxor * @zappbrandnxor * @hyr0n1 * @bender_andnxor * @lacosteaef * @f4nci3 * @Cr4bf04m *****************************************************************************/ #ifndef WH_BENDER_H #define WH_BENDER_H #include <zephyr.h> #define URL_LEADERBOARD "bit.ly/3egadD5" #define URL_SLACK "bit.ly/3eRTR4B" #define URL_END "bit.ly/2Aw1s9C" #define MAP_CHAR_PLAYER "☻" #define MAP_CHAR_LOCKED "°" #define MAP_CHAR_UNLOCKED "°" #define MAP_CHAR_WALL '*' #define MAP_START_ROW 15 #define MAP_START_COL 11 #define MAP_MAX_ROWS 18 #define MAP_MAX_COLS 36 #define NUMBER_CHALLENGES 21 #define NUMBER_MAIN_CHALLENGES 10 #define NUMBER_LULZ_MAX 20 #define NUMBER_ITEMS 10 #define NUMBER_RECAPS 11 #define BENDER_NAME_FLAG 0x01 #define FREND_SYN_FLAG 0x83 #define FREND_ACK_FLAG 0x84 //Description Headers #define BENDER_INTRO_MSG "Badge Enabled Non Directive Enigma Routine Portable Interface SyStem:BENDER~PISSWlcm 2 d sprawl!Typ \"bender\" 2 git started or RTFM.MD!" #define BENDER_CMDZ "DeZ commands R wut U mostly uZ: hack, look, look at THING, loot, map, w a s d,frend, name, reset, gender, &...bender statz" #define BENDER_HACK "U eXplt things whch haz vulnz. Wen U hack stuff U must hack it w a tng itiz vulnerable 2. hack TNG1 wit TNG2. 2 complEt a chaLenG U \"hack flag wit ANSWR\"" #define BENDER_LOOT "2 C *.* U haz typ \"loot show\"Itz not rly stealing f U found it right? So f U find som swEtsupa amazeballs TNG jst typ \"loot TNG\" & itz yorz" #define BENDER_LOOT_SUCCESS "U luv stealing!U luv tkng tNgs!" #define BENDER_LOOK "typ \"look\" 2 peep an area. f U wnt 2 git supa creepy & ^ clOs L%k @ an ITEMtyp \"look at ITEM\"" #define BENDER_FREND "*Unlock Challngz!0 U giv ID 2 frend1 F $frend syn ID2 F giv U FLAG3 U $frend ack FLAG4 Both Profit!" #define BENDER_FREND_SYN "Ax frend 4 bdge ID. datz thR public key.U nEd 2 encrypt it w yor prv8 key. DFIU!Ex: $frend syn ID" #define BENDER_FREND_ACK "Did SOME1 GIV U a frend FLAG?Decrypt it here, git thR bAs unlocks & a flag 4 points. DFIU!Ex: $frend ack FLAG" #define BENDER_RESET "2 reset BENDER~PISS 1st contemplate DIS Lyf choice whIl staring n d mirrashaming yorself. f stil kewl w it typ \"reset Y\"" #define BENDER_RESET_Y "Init 0 ~ Hodl on 2 yor butts.Rst Dun." #define BENDER_RESET_y "n U cnt uz lowR case y we sed uz UPPER CASE Y foLow instrcs o badge wiL explode" #define BENDER_GENDER "B comfortable w hu U are, chAng yor gender f nEd B.U can b: M, F, or XTyp...\"gender MFX\"" #define BENDER_GENDER_ERR "Dat doesnt mAk sense...U must b gender :#)." #define BENDER_GENDER_M "SX chAng sucSful: Man-Bot!" #define BENDER_GENDER_F "SX chAng sucSful: Fem-Bot!" #define BENDER_GENDER_X "SX chAng sucSful: NonBinary-Bot!" #define BENDER_GENDER_PRO_M "Mr " #define BENDER_GENDER_PRO_F "Ms " #define BENDER_GENDER_PRO_X "Mx " //Main Storyling Thingz #define CHALLENGE_MASTER_UNLOCK "NEVERGONNAGIVEYOUUPNEVERGONNALETYOUDOWN" #define CHALLENGE_DESC_LOCKED "D chaLenG iz locked! Xchang frend flag 4 unlock!" #define CHALLENGE_TARGET_HACKED "O damn, we hav a l337 haxor Ovr hEr. d louder U R d less U hEr.tAk a L%k @ yor pwned target." #define CHALLENGE_TARGET_NOT_HACKED_YET "Zzt. Derp. Cnt comply. U must drink aL d b%z & hack aL d thingz." //Main Challenge - OSINT #1 Twitter #define CHALLENGE_FLGR_00 0x64 #define CHALLENGE_DESC_00 "Wut? Itz MrBill. Hes trying 2 coLec OSINT on Hs net of hard hat SD haXor fam.StA classy & giv him wot he wants." #define CHALLENGE_ANSW_00 "420-69-1337" //OSINT - Most common reported SSN from BSSD #define CHALLENGE_TARGET_00_0_NAME "OSINT" #define CHALLENGE_TARGET_00_0_DESC "he pEpn SSN off W3s" #define CHALLENGE_TARGET_00_1_NAME "SSN" #define CHALLENGE_TARGET_00_1_DESC "k not boomer, dat iz social security #" #define CHALLENGE_TOOL_DESC_0 "MALTEGO" //THIS HACKS CHALLENGE_TARGET_00_0_NAME //Main Challenge - CRYPTO/ENCODING #1 Keyboard Walk Encoding #define CHALLENGE_FLGR_01 0x65 #define CHALLENGE_DESC_01 "U find a locked Q10 w tiny ENGRAVING.itz asking 4 a PW.A BIRB flies overhead, you l%k ^ & 2 d L." #define CHALLENGE_ANSW_01 "canada" //CRYPTO - Keyboard shift cypher up and to the left from the engraving (with wraparound): tzizcz #define CHALLENGE_TARGET_01_0_NAME "ENGRAVING" #define CHALLENGE_TARGET_01_0_DESC "on d bak d following iz inscribed: tzizcz" #define CHALLENGE_TARGET_01_1_NAME "BIRB" #define CHALLENGE_TARGET_01_1_DESC "Itz not real, birbs R guvment survlnce drone dat wraprowndd globe ch1rpin \'key key\'" #define CHALLENGE_TOOL_DESC_1 "AMSCOPE" //THIS HACKS CHALLENGE_TARGET_01_0_NAME //Main Challenge - REVERSE ENGINEERING #1 Derbycon Trevor Firmware #define CHALLENGE_FLGR_02 0x66 #define CHALLENGE_DESC_02 "Theres an elctrnk bug. ! d NSA kind bt d ROACH frm con kind.PrograMn INTRFAC exposed. f only U c%d hack dis HW." #define CHALLENGE_ANSW_02 "ROUNDERS" //REVERSE ENGINEERING - Binary is hidden as DERBY.RAW, use strings or Ghidra on it #define CHALLENGE_TARGET_02_0_NAME "INTRFAC" #define CHALLENGE_TARGET_02_0_DESC "D mny bug badge blings raw whIl itz binary dumps.Itz az f frm warez iz jst hidden n pln cite." #define CHALLENGE_TARGET_02_1_NAME "ROACH" #define CHALLENGE_TARGET_02_1_DESC "U haz a senS of longing 4 Lulvil.Trevor 4get icing Dave whIl dressed az a *<|:)." #define CHALLENGE_TOOL_DESC_2 "ICEDEBUGGER" //THIS HACKS CHALLENGE_TARGET_02_0_NAME //Main Challenge - REVERSE ENGINEERING #2 Find the E-Mail Address #define CHALLENGE_FLGR_03 0x67 #define CHALLENGE_DESC_03 "U cUm ax a supa secure medical LAPPY covered n stickers.It hz a TACO_CORP_PROMPT on itz scrEn." #define CHALLENGE_ANSW_03 "8GAT35@VAXX34.0RG"//REVERSE ENGINEERING - Binary is on flash under /usr/bin #define CHALLENGE_TARGET_03_0_NAME "LAPPY" #define CHALLENGE_TARGET_03_0_DESC "D credz auth binary wz XtractD. wot acownt iz Usd 2 login? Saved undRyouZer binz..." #define CHALLENGE_TARGET_03_1_NAME "TACO_CORP_PROMPT" #define CHALLENGE_TARGET_03_1_DESC "D prolly not HIPAA compliant login 4 Taco Corps medical rEsrch divisN.Did dey release d virus only 2 seL thR salsa vaccine az a cure?" #define CHALLENGE_TOOL_DESC_3 "RUBBER_DUCKY" //THIS HACKS CHALLENGE_TARGET_03_0_NAME //Main Challenge - CRYPTO/ENCODING #2 Morse Encoding where speed is related to temperature #define CHALLENGE_FLGR_04 0x68 #define CHALLENGE_DESC_04 "A lRg comms tower itz n not powered, a PIGEON_HOLE gap exists whch needs somTIN4 cndctvity. l%kin awA U notic som CLOUDS. c%d DIS b d coz of it aL. d rona?" #define CHALLENGE_ANSW_04 "5GT0W3RZDuH" //5GT0W3RZDuH (HEX)-> 35 47 54 30 57 33 52 5a 44 75 48 (MORSE) -> CHALLENGE_HACK_04 (BELOW) #define CHALLENGE_HACK_04 "...-- ..... ....- --... ..... ....- ...-- ----- ..... --... ...-- ...-- ..... ..--- ..... .- ....- ....- --... ..... ....- ---.." #define CHALLENGE_TARGET_04_0_NAME "PIGEON_HOLE" #define CHALLENGE_TARGET_04_0_DESC "woah, d bIrb ComplEtd d cIrcuit! a vanilla iCe trak starts playin &lyts r flashin waaa t% fst. nEd 2 lit'rally netflIx & Chill 2 slothngz dwn b4 i git a hedakE" #define CHALLENGE_TARGET_04_1_NAME "CLOUDS" #define CHALLENGE_TARGET_04_1_DESC "R thOs clouds? problE not, thOs R chem trails.Dey put a hex on U morse so thN U tink." #define CHALLENGE_TOOL_DESC_4 "BIRB" //THIS HACKS CHALLENGE_TARGET_04_0_NAME //Main Challenge - CRYPTO/ENCODING #3 RS232 "Serial UART" blinks #define CHALLENGE_FLGR_05 0x69 #define CHALLENGE_DESC_05 "u c Mt BER cn, sobr thotz :( mAbE U cn cure d rona by putn smTIN inside yo slf.U scratch BUTT whIl tinkiN bout it." #define CHALLENGE_ANSW_05 "1NH@L3LY507" //1NH@L3LY507 (BINARY) -> (RS232 Protocol) -> Prepend 0 Start Bit + Invert LSB/MSB Order + Append 1 Stop Bit #define CHALLENGE_HACK_05 "0100011001 0011100101 0000100101 0000000101 0001100101 0110011001 0001100101 0100110101 0101011001 0000011001 0111011001" #define CHALLENGE_TARGET_05_0_NAME "BUTT" #define CHALLENGE_TARGET_05_0_DESC "Yor gutz lite ^ & blink. Itz supa serial 2 stRt tink bout lEst & mstsigNfict tNgs thN stop, cuz DIS mA b d wrng cure." #define CHALLENGE_TARGET_05_1_NAME "BER" #define CHALLENGE_TARGET_05_1_DESC "Modern tImz Fruitlands. datz a damn gud beR, despite it bn Mt." #define CHALLENGE_TOOL_DESC_5 "UVLIGHT" //THIS HACKS CHALLENGE_TARGET_05_0_NAME //Main Challenge - PHREAKING - Elevator Hacking #define CHALLENGE_FLGR_06 0x6A #define CHALLENGE_DESC_06 "U entR a building & wiLCaruana runs awA az U apRch an OpN elvt0r. Yln he hz a:X & dropz a CELL. Thr iz l0kd CALLBOX bElO d flOr btNz." #define CHALLENGE_ANSW_06 "OTIS" #define CHALLENGE_HACK_06 "LUG caL bawx iz n chaLenG 4 you, d trusT baL pik pWns it n 2nds." #define CHALLENGE_TARGET_06_0_NAME "CALLBOX" #define CHALLENGE_TARGET_06_0_DESC "Bt hW u caL? Etchd w wot wz problE a hevE gauge wire U c ZXh0LjQxNzc=" //Ext 4177 #define CHALLENGE_TARGET_06_1_NAME "CELL" #define CHALLENGE_TARGET_06_1_DESC "Therz only 1 fone # n d recnt caL lst 312d3333372d4d41542d492d4f4245592e2e2e4d6179422064726f7020442059" #define CHALLENGE_TOOL_DESC_6 "LOCKPICK" //THIS HACKS CHALLENGE_TARGET_06_0_NAME ///Main Challenge - SIGINT - POCSAG Payphone Challenge #define CHALLENGE_FLGR_07 0x6B #define CHALLENGE_DESC_07 "A PAYPHONE by a run dwn gas statN. P$ shows -$1337 / gal.WUT?! wiLCaruana again, n he iz runN awA :-d & shooting a laser @ U." #define CHALLENGE_ANSW_07 "DUALCORE" #define CHALLENGE_HACK_07 "d # U R clng cnt b rEchD pls hang ^ & try agen: 312d3333372d4d41542d492d4f4245592e2e2e4d6179422064726f7020442059" #define CHALLENGE_TARGET_07_0_NAME "PAYPHONE" #define CHALLENGE_TARGET_07_0_DESC "d fone worx bt itz auto dialing a messed ^ #. how Ls c%d U caL it?& u 1Dr wut ^ wit itz COINBOX..." #define CHALLENGE_TARGET_07_1_NAME "COINBOX" #define CHALLENGE_TARGET_07_1_DESC "it hz Bin pryed OpN & NE coins put n faL rght bak out.N bak u C msg: Rm9yIGEgZ29vZCB0aW1lIGNhbGwgZXh0LiAyMzIz" //Ext 2323 #define CHALLENGE_TOOL_DESC_7 "QUARTER" //THIS HACKS CHALLENGE_TARGET_07_0_NAME //Main Challenge - CRYPTO/ENCODING #4 NTLM PASSWORD CRACKING #define CHALLENGE_FLGR_08 0x6C #define CHALLENGE_DESC_08 "Pon d flOr ther sits a glitter covered tink pad frm TyMkrs.Itz old, runN win 2000, & evN hz an IOMEGA_DRIVE." #define CHALLENGE_ANSW_08 "m3atl0af" #define CHALLENGE_TARGET_08_0_NAME "IOMEGA_DRIVE" #define CHALLENGE_TARGET_08_0_DESC "W a solid clik d disk snaps in2 plAc.Un4tuN8ly d files R credential locked by d win SAM" #define CHALLENGE_TARGET_08_1_NAME "SAM" #define CHALLENGE_TARGET_08_1_DESC "Navigating 2 d win SYS thirty two config SAM U find:0E7FDE76B8A417953D640D5CDB0D9B72" #define CHALLENGE_TOOL_DESC_8 "ZIP_DISK" //THIS HACKS CHALLENGE_TARGET_08_0_NAME //Main Challenge - CRYPTO/ENCODING #5 SLACKBOT #define CHALLENGE_FLGR_09 0x6D #define CHALLENGE_DESC_09 "Theres a robotic HED on d ground, bt it iz lacking d milliamps.FAC & reminds of U of pure annoyance." #define CHALLENGE_ANSW_09 "iCanHazEncryptI0n?" #define CHALLENGE_TARGET_09_0_NAME "HED" #define CHALLENGE_TARGET_09_0_DESC "U cn ask me simpl questions bout how Slack works,o jst typ a few keywords lIk \"m355@g3\" bt TLK 2yorself so others lIk guvment dun knO" #define CHALLENGE_TARGET_09_1_NAME "FAC" #define CHALLENGE_TARGET_09_1_DESC "Blu grEn red yeLo w two eyes som brows & wot d fuk iz dat a nose o mouth?!" #define CHALLENGE_TOOL_DESC_9 "BATTERY" //THIS HACKS CHALLENGE_TARGET_09_0_NAME //Recap Challenge - CRYPTO/ENCODING #6 RECAP #define CHALLENGE_FLGR_20 0x85 #define CHALLENGE_DESC_20 "WTF hapnd 2 DIS world since DC27? WeL AND!XOR rOt it n a note, tore it up, &...itz randomly spred throughout d wrld. Hav :) putting it bak 2geder 4 recap" #define CHALLENGE_ANSW_20 "DXDCABUUUUR" #define BENDER_RECAP "WTF hapnd 2 DIS world since DC27? WeL AND!XOR rOt it n a note, tore it up, &...itz randomly spred throughout d wrld. Hav :) putting it bak 2geder 4 recap" #define RECAP_HEADER "U find r3cap papR..." #define RECAP_00 "44 20 64 63 32 37 20 61 6e 64 21 58 6f 72 20 6e 75 63 6c 65 61 72 20 77 6e 74 72 20 62 61 64 67 65 20 26 20 68 61 63 6b 66 6f 72 73 61 74 61 6e 20 70 61 6e 64 65" #define RECAP_01 "6d 69 63 20 62 61 64 67 65 20 67 6f 74 20 64 72 75 6e 6b 2c 20 68 6f 6f 6b 64 20 75 70 2c 20 26 20 63 61 75 73 65 64 20 44 20 72 6f 6e 61 20 66 72 6d 20 73 6f 6d" #define RECAP_02 "20 6d 65 73 73 65 64 20 5e 20 73 74 64 2e 20 74 68 6e 20 64 65 66 20 43 6f 6e 20 77 7a 20 63 61 6e 63 65 6c 6c 65 64 2e 20 34 20 72 65 61 6c 73 69 65 73 2e 20 73" #define RECAP_03 "69 6e 63 65 20 74 68 6e 20 77 65 76 65 20 73 70 72 65 64 20 72 75 6d 6f 72 73 20 63 75 7a 20 77 65 20 72 20 3a 22 29 20 62 6f 75 74 20 64 20 68 25 6b 20 5e 2e 20" #define RECAP_04 "72 75 6d 6f 72 73 20 73 75 63 68 20 6c 69 6b 20 69 74 20 77 7a 20 62 61 74 73 2c 20 35 20 67 20 63 65 6c 20 74 6f 77 65 72 73 2c 20 62 69 72 64 73 2c 20 62 69 6c" #define RECAP_05 "6c 20 67 61 74 65 73 20 74 72 79 69 6e 67 20 32 20 6d 41 6b 20 6d 6f 6e 65 20 6f 66 66 20 6f 66 20 76 61 63 63 69 6e 65 73 2c 20 63 6f 6e 76 69 6e 63 69 6e 67 20" #define RECAP_06 "70 6f 74 75 73 20 32 20 63 6f 6e 76 69 6e 63 65 20 75 20 32 20 64 72 69 6e 6b 20 42 6c 65 61 63 68 2e 2e 2e 20 66 20 55 20 62 6c 65 76 20 6e 65 20 6f 66 20 64 61" #define RECAP_07 "74 20 55 20 72 20 64 75 6d 62 2e 20 31 30 30 30 25 20 66 6b 6e 20 6c 75 67 2e 20 63 6f 72 6f 6e 61 76 69 72 75 73 20 73 75 78 20 26 20 64 65 2d 72 61 69 6c 65 64" #define RECAP_08 "20 6f 75 72 20 61 6e 6e 75 61 6c 20 63 6f 6e 20 78 70 65 72 65 6e 73 2e 20 69 67 6e 6f 72 20 61 6c 20 64 61 74 20 64 75 6d 62 20 73 63 68 65 74 20 26 20 68 61 76" #define RECAP_09 "20 3a 29 20 68 61 63 6b 69 6e 67 20 64 69 73 20 62 61 64 67 65 2e 20 77 65 20 68 6f 70 20 69 74 20 62 72 69 6e 67 73 20 55 20 3a 29 20 26 20 68 61 70 65 6e 73 2e" #define RECAP_10 "20 55 20 73 68 75 64 20 68 61 63 6b 20 66 6c 61 67 20 77 69 74 2e 2e 2e 75 70 70 52 20 63 61 73 65 2e 2e 2e" //Lulz Quiz #define CHALLENGE_DESC_10 "~LULZ QUIZ~(0)EMACS(1)VIM(2)NANO$hack flag wit #" #define CHALLENGE_ANSW_10 "1" #define CHALLENGE_FLGR_10 0x6E #define CHALLENGE_FLGW_10 0x6F #define CHALLENGE_DESC_11 "~LULZ QUIZ~Did Carole Baskin kill her OM?(0)Yes(1)No$hack flag wit #" #define CHALLENGE_ANSW_11 "0" #define CHALLENGE_FLGR_11 0x70 #define CHALLENGE_FLGW_11 0x71 #define CHALLENGE_DESC_12 "~LULZ QUIZ~Pineapple on pizza?(0)Yes(1)No$hack flag wit #" #define CHALLENGE_ANSW_12 "0" #define CHALLENGE_FLGR_12 0x72 #define CHALLENGE_FLGW_12 0x73 #define CHALLENGE_DESC_13 "~LULZ QUIZ~(0)OSX(1)Windows(2)Linux(3)BSD$hack flag wit #" #define CHALLENGE_ANSW_13 "2" #define CHALLENGE_FLGR_13 0x74 #define CHALLENGE_FLGW_13 0x75 #define CHALLENGE_DESC_14 "~LULZ QUIZ~(0)Red Team(1)Blu Team(2)Purpl Team$hack flag wit #" #define CHALLENGE_ANSW_14 "2" #define CHALLENGE_FLGR_14 0x76 #define CHALLENGE_FLGW_14 0x77 #define CHALLENGE_DESC_15 "~LULZ QUIZ~(0)Spaces(1)Tabs$hack flag wit #" #define CHALLENGE_ANSW_15 "1" #define CHALLENGE_FLGR_15 0x78 #define CHALLENGE_FLGW_15 0x79 #define CHALLENGE_DESC_16 "~LULZ QUIZ~(0)Drop 0-Day(1)Notify Vendor$hack flag wit #" #define CHALLENGE_ANSW_16 "1" #define CHALLENGE_FLGR_16 0x7A #define CHALLENGE_FLGW_16 0x7B #define CHALLENGE_DESC_17 "~LULZ QUIZ~(0)Hack(1)Slp(2)Et(3)showR$hack flag wit #" #define CHALLENGE_ANSW_17 "3" #define CHALLENGE_FLGR_17 0x7C #define CHALLENGE_FLGW_17 0x7D #define CHALLENGE_DESC_18 "~LULZ QUIZ~(0)tst n devlpmnt(1)tst n production(2)dun tst$hack flag wit #" #define CHALLENGE_ANSW_18 "2" #define CHALLENGE_FLGR_18 0x7E #define CHALLENGE_FLGW_18 0x80 #define CHALLENGE_DESC_19 "~LULZ QUIZ~(0)Buffer Underflow(1)Buffer Overflow$hack flag wit #" #define CHALLENGE_ANSW_19 "-1" //LOLZ #define CHALLENGE_FLGR_19 0x81 #define CHALLENGE_FLGW_19 0x82 typedef struct{ uint8_t index; bool challenge; }challenge_tracker_t; typedef struct{ uint8_t location_row; uint8_t location_col; uint8_t flag_cmd_right; uint8_t flag_cmd_wrong; bool discovered; bool unlocked; bool hacked; bool solved; bool right; bool lulz; }challenge_t; typedef struct{ uint8_t location_row; uint8_t location_col; bool haz; }item_t; typedef struct{ uint8_t location_row; uint8_t location_col; }recap_t; typedef struct{ char gender; uint8_t location_row; uint8_t location_col; uint8_t random_unlock_0; uint8_t random_unlock_1; uint8_t random_unlock_2; challenge_t challenges[NUMBER_CHALLENGES]; item_t items[NUMBER_ITEMS]; recap_t recap[NUMBER_RECAPS]; }bender_data_t; extern void wh_bender_data_init(); #endif -
CTF Results & Walkthrough (Part 3)
08/15/2020 at 16:34 • 0 commentsWhat are the Lulz Quizzes?
These are small point value Q&A. If you get it right +5, if you get it wrong -10. How do you dig out of that hole? Well different flags are provided if you got it "right" vs "wrong." So you reset the badge, re-randomize the CTF, go find them again...grind grind grind... and you can mitigate -10 to -5 worst case. Come out +5 points for each, best case. Some complained that our results for the lulz were subjective. This is hardly the case, because we are right and you are wrong :)
LULZ QUIZ 0
~LULZ QUIZ~ (0)EMACS (1)VIM (2)NANO
Flag: hack flag wit 1
What Did You Learn Today: VIM DUH!
LULZ QUIZ 1
~LULZ QUIZ~ Did Carole Baskin kill her OM? (0)Yes (1)No
Flag: hack flag wit 0
What Did You Learn Today: Carole Fucking Baskin
LULZ QUIZ 2
~LULZ QUIZ~ Pineapple on pizza? (0)Yes (1)No
Flag: hack flag wit 0
What Did You Learn Today: Its the best kind of pizza
LULZ QUIZ 3
~LULZ QUIZ~ (0)OSX (1)Windows (2)Linux (3)BSD
Flag: hack flag wit 2
What Did You Learn Today: Linux > Windows > OSX > Dumpster Fire > BSD
LULZ QUIZ 4
~LULZ QUIZ~ (0)Red Team (1)Blu Team (2)Purpl Team
Flag: hack flag wit 2
What Did You Learn Today: Your assessments don't mean shit unless you work together to fix it.
LULZ QUIZ 5
~LULZ QUIZ~ (0)Spaces (1)Tabs
Flag: hack flag wit 1
What Did You Learn Today: Finally this debate has been settled once and for all
LULZ QUIZ 6
~LULZ QUIZ~ (0)Drop 0-Day (1)Notify Vendor
Flag: hack flag wit 1
What Did You Learn Today: Responsible disclosure
LULZ QUIZ 7
~LULZ QUIZ~ (0)Hack (1)Slp (2)Et (3)showR
Flag: hack flag wit 3
What Did You Learn Today: Yeah. Shower. For the good of everyone.
LULZ QUIZ 8
~LULZ QUIZ~ (0)tst n devlpmnt (1)tst n production (2)dun tst
Flag: hack flag wit 2
What Did You Learn Today: YOLOSEC
LULZ QUIZ 9
~LULZ QUIZ~ (0)Buffer Underflow (1)Buffer Overflow
Flag: hack flag wit -1
What Did You Learn Today: LOLOLOLOLOLOLOLOL
COMPLETION 100%
3d 5f 32 23 5e 46 21 2c 43 35 2b 43 5d 34 32 40 56 26 74 69 41 53 72 57 24 47 41 5c 4f 38 45 62 75 71 3c 40 3c 2d 49 38 42 6c 37 51 2b 2d 36 51 63 3f 45 63 2c 48 21 2b 3d 38 34 4f 44 64 6d 58 2c 42 6d 4f 3f 24 2b 3d 38 34 41 2b 44 75 3d 33 43 68 37 24 71 2b 45 70 53 26 3b 42 52 3b 2f 41 30 3c 57 5d 31 2c 27 68 5b 42 6c 37 52 25 2b 43 65 69 23 41 30 3e 69 22 44 49 64 3c 71 42 6b 26 39 30 42 51 3e 34 60 37 37 4a 43 65 3a 4a 4e 24 56 48 36 3f 5e 2b 44 49 5b 36 6f 41 52 6d 44 47 2f 67 2b 5b 49 44 2e 2e 61 25 2b 45 29 34 31 44 4b 3f 71 2c 2b 3d 38 34 32 2b 43 63 4f 29 40 3c 3c 56 6c 2b 41 73 3e 22 47 39 43 4c 3c 37 34 6f 5d 5f 2b 41 3d 28 73 2b 3e 50 27 62 44 66 51 74 45 40 3c 3f 21 6d 2b 3e 50 27 4c 2b 45 71 61 47 2b 45 56 6d 47 2b 44 47 70 3f 42 6d 4c 6e 32 46 3c 47 2b 26 46 3c 47 64 39 46 43 53 75 2c 42 6d 4c 6e 3c 44 4a 28 29 29 44 66 30 2c 3d 2b 40 4c 2d 5a 46 29 48 28 42 44 2a 55 75 4f 2b 42 33 23 63 45 62 30 3b 37 44 42 4f 25 48 44 27 33 5e 3d 41 30 3e 3c 22 44 65 21 33 6c 48 23 52 68 39 2f 67 2b 29 32 2b 42 39 50 29 46 60 26 66 61 2f 67 2a 47 4b 42 35 29 2d 50
When your completion is at 100% (All Main & Lulz Challenges) a bit.ly/2Aw1s9C link appears.
HEX -> BASE85
BONUS CHALLENGES & EASTER EGGS
DEF CON MUD Bonus Challenge
EvilMog was quite a sport and we collaborated a bit between BENDERPISS and the MUD. If you head to the mog.ninja and follow instructs, you can play the DEF CON MUD which is amazing. BENDER draws a lot of its roots from text based adventures and MUDs.
The flag is simple, yet difficult. Head to the woods in the north where you have a quest to hunt animals in the woodland maze. There you will find... hyr0n the gerbil!
"A small light brown furry gerbil. He has a white tummy, and very sharp claws. He is very cute, and quite friendly but scared of strangers. He will probably run from you if you come near him."
Don't fight him, he'll kick your ass! Just look and you will see a flag tied to him. Oh, and he's kinda quick and only remains in a each sector for 1 second. Act quickly...
Slackbot Bonus Challenge
Did you notice some other words were triggering that asshole Slackbot?
What do these have in common? They are all hacking words...they are related to the challenges on the badge...AND most of these are all in the same paragraph in the RTFM.
Each trigger word would randomly print one of two responses.
If you were lucky enough to see all the responses and put them in order, you'd have this list:https://twitter.com/kur3us/status/1279638633201324032 1:{14,2} 2:{12,3} 3:{14,1} 4:{4,1} 5:{17,2} 6:{20,3}If you go to that tweet, there are 3 rows of 20 characters.
Take the first clue...1:{14,2}. Go to the 14th column and the 2nd row, and you have aj.
For the second clue...2:{12,3}, go to the 12th column and 3rd row, where you'll find ap.
Continuing in this fashion, you'll get the complete 6 letter flag:jpK99xEnter this into the badge decoder for a scoreboard flag!Taco Corp Support Line
Did you like the phone system setup by Penguin?
Alethe and Ryan put A LOT of effort in to keeping everyone entertained and navigating the call server.
There were 2 Main Challenges from the badge (Ext 4177 & 2323) and a Bonus Challenge (Ext 1337).
The easter eggs...are still for you to find, as there are a total of 27 other extensions for your enjoyment...
LayerOne Challenge
DG & JK were kind enough to put together a challenge we would expect, since they are bonified MFPs.
![]()
The following is a copy / paste from the walkthrough sent to us from DG, slight edits have been made to make it read properly as a HaD writeup...
Info not for public release / solution walkthrough:
Hyr0n I dream of combing your beard and talking about binary RE over rootbeers.
This challenge is a mixture of file format shenanigans, esoteric programming languages, and reverse engineering. If you had to give it a single category it should probably be "Reverse Engineering", but "Misc" would also be reasonable. I would rank this as a Hard challenge.
Challenge starts with a PNG file promoting LayerOne. Cause we're mad shady like that. There's some easter eggs and red herrings hidden in the PNG itself for folks that try to go down the stego/image metadata route, but what anyone with PNG experience should see is that the file is bigger than it should be for the size of image defined. This could be because we modified the PNG header to not display the full image, but that's not the case (can be verified by basic math on the PNG data stream). PNG is a chunk format that allows anything after the PNG to be appended to the file and ignored by PNG parsers(similar to "slack space" in traditional disk/filesystem forensics). A naive look through strings/etc data would show normal PNG things, but if you look closely its duplicated; there are two PNGs within the one file. This can be carved out manually or using and file carving tool like binwalk, scalpel, foremost, etc.
The second file is a valid PNG with no discernible starting points based on image metadata / similar things to image 1. As before, there is no stego, watermarking, or anything like that - but there are some more red herrings and easter eggs in these places to annoy and or amuse people. Looking at the image itself, its got a variety pixels in a variety of colors around the edges; looks like static or random colors. This could be some complex data formatting, but it is instead a programming language called Piet. Piet works by having a direction pointer (an arrow) and the color transitions between pixels or blocks of pixels defines the operations that should happen. There's some rules behind this but the end result is things like "no change in hue, but +1 change in darkness == PUSH instruction". Sounds pretty weird but it's a pretty well-known language as far as esoteric languages go - not quite Brainfuck but up there in our opinion. There's no big challenge here other than identifying that it is Piet and running it in a Piet interpreter (we thought the rest of the challenge was enough RE to go around). Running the second file through a Piet interpreter will produce a binary data blob. There's quite a few Piet interpreters online, but we used the main one, npiet, for verifying things worked.
It should be pretty obvious that the output of the Piet code is a x86_64 ELF executable file. From here it can be executed, run through IDA/Ghidra/whatever. There are some anti-decompilation, anti-disassembly, and anti-debugging features that should make it a little more complicated than running Decompile in Ghidra to see what the flag should be. The gist of this problem is that the executable wants to validate input in a variety of ways (e.g. not a single password entry) to verify they solved it and can have the flag - all of which should require a bit of reversing to understand. The requirements to get the flag are:
1. argv[0] must be a specific value ('L'). Rename the binary OR harness the binary with Python/whatever to modify argv.
2. argv[1] must be a specific value('m'). Supply it on the command line / harness on execution.
3. The environment variable ('the third letter') must be a specific value ('d'). Supply it on the command line / harness on execution.
4. A single character can be entered as a "Enter the flag: " on execution; it must be a specific value ('3').
5. The binary itself must be modified so that a specific NOTE segment of type (0x420) name ('flg\x00') and desc ('second char = 1') is present. This can be done with a hex editor.
6. The command line used to run the program must be a specific value ('../../thelastcharacteris/0'). This is distinct from argv[0].This sounds extremely complicated, but all of it can be bypassed in a debugger - only non-debugger methods are noted above. The issue there is that they might skip some code that sets the flag properly, resulting in an incorrect flag printed at the end. This should be fun for you when they are complaining their flags don't work.
Assuming all steps were followed properly the flag 'L1d3m0' is printed out with a message saying it's the correct flag.
-
CTF Results & Walkthrough (Part 2)
08/15/2020 at 05:20 • 0 commentsContinued...
Challenge 4 - Hardware Encoding Morse
A lRg comms tower itz n not powered, a PIGEON_HOLE gap exists whch needs somTIN4 cndctvity. l%kin awA U notic som CLOUDS. c%d DIS b d coz of it aL. d rona?
Description: So when one completes the tool/target combo, the badge lights up and blinks. Fast. REALLY FAST. Some people just recorded it with their phones and slowed it down to watch the pattern. Others...actually read what it said "woah, d bIrb ComplEtd d cIrcuit! a vanilla iCe trak starts playin &lyts r flashin waaa t% fst. nEd 2 lit'rally netflIx & Chill 2 slothngz dwn b4 i git a hedakE" Let's think about this. Blinking fast, need to "chill" and slow things down. Well if one used the MYBASIC editor they would have noticed there was a TEMP.BAS which describes the location of the thermistor temperature sensor on the badge. Guess what happens when you chill the sensor down? It slows the blinkies down. Do that, and you should notice the dot and dash pattern, which is morse encoding. There's also other hints when you look at the clouds "R thOs clouds? problE not, thOs R chem trails.Dey put a hex on U morse so thN U tink." Anyway, decode the morse and this translates to 5GT0W3RZDuH.
...-- ..... ....- --... ..... ....- ...-- ----- ..... --... ...-- ...-- ..... ..--- ..... .- ....- ....- --... ..... ....- ---..
Tool unlock: hack PIGEON_HOLE wit BIRB
Flag: hack flag wit 5GT0W3RZDuH
What Did You Learn Today: That sometimes embedded systems used peripheral sensors for entropy. And if you have access to hardware you can control that entropy. Which lets you control the logic, such as blink speed or encryption keys...
Challenge 5 - HARDWARE Encoding RS232
u c Mt BER cn, sobr thotz :( mAbE U cn cure d rona by putn smTIN inside yo slf.U scratch BUTT whIl tinkiN bout it.
Description: This one is very similar to morse encoding, only we encoded it with good ol' RS232 Serial. Because one should know those serial UART adapter blinkies mean something. More importantly this should teach you about how to interpret reading serial on a logic analyzer. The initial description doesn't help much, but once the tool/target hack is completed (which should be obvious because COVID can be killed by inserting a UV Light in you somehow somewhere) you will be told "Yor gutz lite ^ & blink. Itz supa serial 2 stRt tink bout lEst & mstsigNfict tNgs thN stop, cuz DIS mA b d wrng cure."
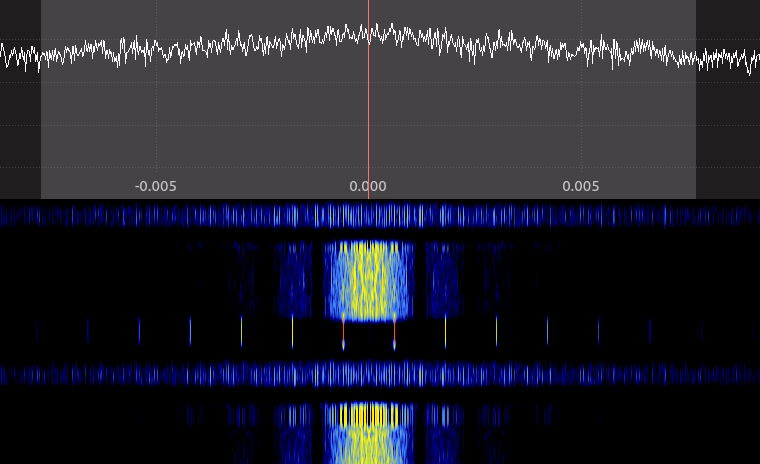
![I'm Super Serial! - Imgur]() Super Serial? Think about the least and most significant things? C'mon what better hints could we have given you? Now if you've never worked with serial a quick google on how the protocol works will teach you that charachters are turned into binary, it pads a 0 as the start bit, it INVERTS the LSB/MSB order (so its received correctly), then the end is appended with a 1 as the stop bit. The blink pattern shown would translate to...
Super Serial? Think about the least and most significant things? C'mon what better hints could we have given you? Now if you've never worked with serial a quick google on how the protocol works will teach you that charachters are turned into binary, it pads a 0 as the start bit, it INVERTS the LSB/MSB order (so its received correctly), then the end is appended with a 1 as the stop bit. The blink pattern shown would translate to...0100011001 0011100101 0000100101 0000000101 0001100101 0110011001 0001100101 0100110101 0101011001 0000011001 0111011001
So you remove the start and stop bits, invert the binary, and the result is: 1NH@L3LY507
Tool unlock: hack BUTT wit UVLIGHT
Flag: hack flag wit 1NH@L3LY507
What Did You Learn Today: How serial encoding on hardware actually works.
Challenge 6 - PHREAKING Elevator
U entR a building & wiLCaruana runs awA az U apRch an OpN elvt0r. Yln he hz a:X & dropz a CELL. Thr iz l0kd CALLBOX bElO d flOr btNz.
Description: Good ol' Will Caruana. This gentleman is a curator of shenanigans and a dear friend. So we thought we would team up and simulate some elevator phreaking in the form of a badge CTF challenge. The callbox is locked, so unlocking it..calls for a lock pick. Once you get it open you see "Bt hW u caL? Etchd w wot wz problE a hevE gauge wire U c ZXh0LjQxNzc=" also the other item is the cell which Will drops "Therz only 1 fone # n d recnt caL lst 312d3333372d4d41542d492d4f4245592e2e2e4d6179422064726f7020442059"
Translate those encodings... You get our phone number and extension:
1-337-MAT-I-OBEY...MayB drop D Y
Extension: 4177
Give good old Taco Corp Pharmaceutical, Elevator Right to Repair, bath tub medea vodka, and artisinal organic salsa factory super friendly and sometimes helpful but not always customer service hotline. Enter extension 4177 and you will over hear Will & Hyr0n simulating an elevator phreaking event with the flag at the end. Its like you're actually phreaking an elevator that we are hanging out in (but not..because DEF CON was canceled) He gave a great talk on this and they did a write up in Wired as well.
![]()
Tool unlock: hack CALLBOX wit LOCKPICK
Flag: hack flag wit OTIS
What Did You Learn Today: Kinda weird and scary, that elevators can be dialed into and discussions had, by a phone number and extension. That, the phone number is related to the callbox and the extension typically the number on the top of the elevator.
Challenge 7 - WIRELESS POCSAG
A PAYPHONE by a run dwn gas statN. P$ shows -$1337 / gal.WUT?! wiLCaruana again, n he iz runN awA :-d & shooting a laser @ U.
Description: What's better than NPC Will once? Twice. When you hack the target with tool, you learn of a COINBOX on the PAYPHONE. This has an encoding "it hz Bin pryed OpN & NE coins put n faL rght bak out.N bak u C msg: Rm9yIGEgZ29vZCB0aW1lIGNhbGwgZXh0LiAyMzIz" which translates to extension 2323. Same phone number as elevator phreaking (encoded again) in hex. Give it a call with the other extension. You get a message that spells out a bitly link. Go get that link. Its a soundtrack to the pool party, the pool on the roof...wonder who is playing? When you listen, well it's quite the sound. Here's my best advice when dipping your toes into the world of signals. You can visit the Signal Identification Wiki and based on its frequency, down select what it could possibly be, then proceed to demodulate & decode it. You can also grab a phone app called SignalID which assists in identifying signals. So lets say you get past that hurdle and learn its good ol Post Office Code Standardisation Advisory Group (POCSAG). Great! If you are a Windows Person, you could follow this link... But we aren't Windows people that often, we like Penguins. So how could you do this entirely in Linux?
Option 1 EZ CLI Method (Credit 5p0rk):
lappy@386:~$ multimon-ng -s SCOPE -t wav dc28_andnxor_ost.wav > out; grep POCSAG outOption 2 GQRX Existence is Pain Method (but it gets you understanding how the tool works):
In short, to make the file able to transfer around and not make us go broke with bandwidth charges, we compressed it using a GQRX export. Which means you will have to upsample it. You do this with sox. More importantly, when you do this, its a RAW signal meaning there is no metadata in the file header and GQRX has to read that info based on the structure of the file name. So do the following to upsample the WAV.
$sox dc28_andnxor_ost.wav -e float -t raw -r 1024000 -b 32 -c 2 gqrx_20200806_123456_123456789_1024000_fc.raw
Notice the format is essentially "gqrx_YYYYMMDD_XXXXXX_XXXXXXXXX_BITRATE_fc.raw"
The x's can be anything really its just the structure which matters.
Also note this isnt going to be a tutorial on GQRX in Linux, there are plenty of those. What is important is realizing we are going to load a RAW/IQ file play it back over UDP , pipe that into SOX to downsample it, then pipe it into multimon to decode. Yes, btw, that is very stupid that it has to be upsampled just to get played by GQRX because GQRX CANT EVEN NATIVELY PLAY THE DAMN FILES IT RECORDS WITHOUT EXTERNAL MODIFICATION (pull request incoming)... Anyway, once you have the file loaded and the correct SDR receiver settings for POCSAG in GQRX (-26db squelch, RAW/IQ Mode, Width about 15k), his play and in another command window run the following...
lappy@386:~$ nc -l -u -p 7355 | sox -t raw -esigned-integer -b 16 -r 48000 - -esigned-integer -b 16 -r 22050 -t raw - | multimon-ng -t raw -a POCSAG512 -a POCSAG1200 -a POCSAG2400 -a FLEX -f alpha - | cut -c 52-And here is what you will hear (i.e. robot sex) and see...
hyr0n@ubuntu:~/dev/sdr$ nc -l -u -p 7355 | sox -t raw -esigned-integer -b 16 -r 48000 - -esigned-integer -b 16 -r 22050 -t raw - | multimon-ng -t raw -a POCSAG512 -a POCSAG1200 -a POCSAG2400 -a FLEX -f alpha - | cut -c 52- multimon-ng 1.1.8 (C) 1996/1997 by Tom Sailer HB9JNX/AE4WA (C) 2012-2019 by Elias Oenal Available demodulators: POCSAG512 POCSAG1200 POCSAG2400 FLEX EAS UFSK1200 CLIPFSK FMSFSK AFSK1200 AFSK2400 AFSK2400_2 AFSK2400_3 HAPN4800 FSK9600 DTMF ZVEI1 ZVEI2 ZVEI3 DZVEI PZVEI EEA EIA CCIR MORSE_CW DUMPCSV X10 SCOPE 00 FLEX This one's dedicated to all the hackers. Even out settle score quick. My disaster recovery requires even more disks<LF><NUL> Put your bytes up, prove it or you forfeit. Got my C64 and we blew it into orbit. 1:M. Bison with eight straight perfects<LF> Overload emotions make hate, break circuits. In case you heard, it's a name fake service. Optimize our runtime to escape verdicts.<LF> Got an integer scope flow. That they can't sign. Passing code, didn't sanitize. Command lines; land mine<LF> So before, they'll see me after. I'm Advice dog. Courage Wolf. Plus Philosoraptor. Don't prove we're human unless we really hafta<LF><NUL> My team built schemes that destroyed recaptcha. Hate what they see, finish this chapter.<LF><NUL><NUL> By the way we're not any geeks, we hack into NASA.<LF> Drink all the booze. Hack all the things. Drink all the booze. Hack all the things<LF><NUL><NUL> Drink all the booze. Hack all the things. Drink all the booze. Hack all the things<LF><NUL><NUL> Got this Vodka and this Redbull. They still give me wings.<LF><NUL> Drink all the booze. Hack all the things. Drink all the booze. Hack all the things<LF><NUL><NUL> Drink all the booze. Hack all the things. Drink all the booze. Hack all the things<LF><NUL><NUL> Zero through Three. We're in every single ring. I'm just waiting until my blackberry dies<LF><NUL> Cause I'll replace it with a raspberry pi. Don't compare to this track. It makes everything they said dull<LF><NUL> Neutralize any threat. Turn Red skull to dev null. They killed virus writers that we mentioned<LF><NUL><NUL> But instead they ascended to the VXHeavens. To reincarnate as live wires. Still inside we hide ciphers in signed device drivers<LF> Which school will we hit next? They didn't learn the format. So we've gotta printf. Next step is a chin check<LF><NUL> Freestyles that I spit best. They didn't decrypt yet. I crush internet MC's in rhyme battles. Get your WiFi tackled<LF><NUL> Hak5 Pineapple. I don't think you'll like my snapple. Cause I popped it with vodka. And a cyanide capsule<LF><NUL><NUL> Drink all the booze. Hack all the things. Drink all the booze. Hack all the things<LF><NUL><NUL> Drink all the booze. Hack all the things. Drink all the booze. Hack all the things<LF><NUL><NUL> Got this Vodka and this Redbull<LF><NUL><NUL> They still give me wings<LF> So we drink all the booze. Hack all the things. Drink all the booze. Hack all the things<LF><NUL><NUL> Drink all the booze. Hack all the things. Drink all the booze. Hack all the things<LF><NUL><NUL> First we drink all the booze. Then we hack all the things. Then backdoor the firmware.<LF><NUL> On anything you bring. Regardless of the hardware, service, or encoding. Connected it to the internet<LF> And someone's gonna own it. This is for the pirates who clap. And love the sound attacking from the cloud<LF><NUL><NUL> Then we're back in underground. There's no masking from us now. We pop Tor nodes around the globe<LF><NUL><NUL> Track and hunt you down. Hacked on schedule, add it to your calendar. Devices online; here comes another challenger<LF><NUL> State infiltrated, so undercover. This is for my comrades who stare at their debuggers. And trace every buffer<LF> Examining the code flow. Haven't been to sleep? Better pop another No-Doz. I think I'll need a planet sized urn<LF><NUL><NUL> Cause some men just wanna see the world burn. Your turn!<LF> Drink all the booze. Hack all the things. Drink all the booze. Hack all the things<LF><NUL><NUL> Drink all the booze. Hack all the things. Drink all the booze. Hack all the things<LF><NUL><NUL> Got this zodka and this Redbull. They still give me wings<LF><NUL><NUL> So we drink all the booze. Hack all the things. Drink all the booze. Hack all the things<LF><NUL><NUL> Drink all the booze. Hack all the things. Zero through three. We're in every single ring<LF><NUL><NUL> FLAG: DUALCORE<LF><NUL><NUL>TBH We were really sad about not being able to bring this to DEF CON. Hyr0n studied to get his HAM tech, coordinate, and setup a POCSAG beacon for DC28 just so we could broadcast Hack All The Things for a wireless challenge. At least you got a recording to hack on.
Tool unlock: hack PAYPHONE wit QUARTER
Flag: hack flag wit DUALCORE
What Did You Learn Today: POCSAG (pager protocol) while old, is still heavily in use and can be monitored in the clear with a $15 software define radio. What still uses POCSAG you ask? Those vibrating pick up your food pucks at restaurants. Oh and hospitals. Yep, many hospitals use POCSAG as a backup for their internal messaging system and unfortunately transmit patients private health information IN THE CLEAR. Which is a HIPAA violation (you cant even send that info via text message). If you ever come across this in the spectrum, responsibly report the hospital to HIPAA for their negligent handling of patient information.
Challenge 8 - PASSWORD CRACKING NTLM
Pon d flOr ther sits a glitter covered tink pad frm TyMkrs.Itz old, runN win 2000, & evN hz an IOMEGA_DRIVE.
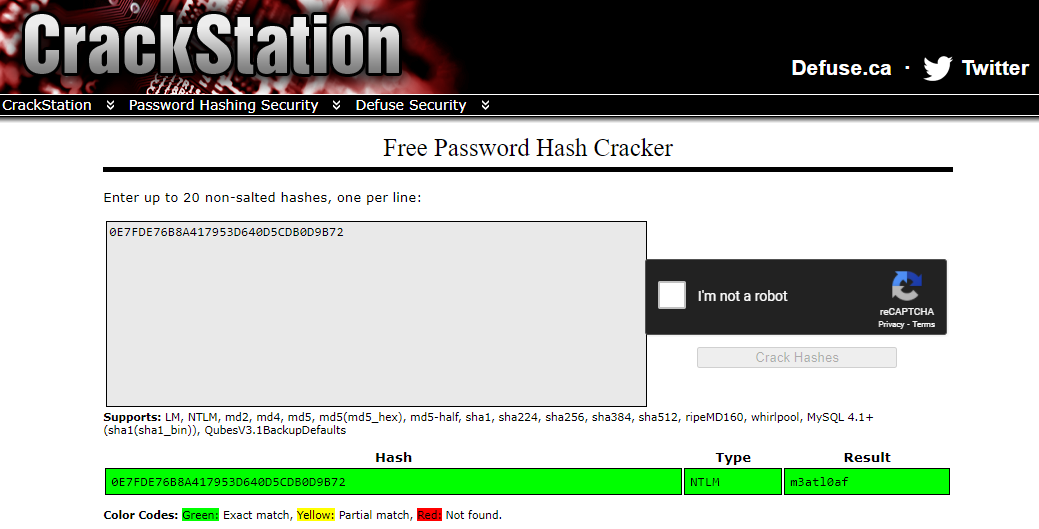
Description: This challenge refernces a damn drop box we got from the TyMkrs, an old computer, and the fact that you need to hack its password. The lesson here is that older OS's, like Win 2k, used NTLM as its password base. How do you get that hint? When performing the tool/target hack, it is revealed "W a solid clik d disk snaps in2 plAc.Un4tuN8ly d files R credential locked by d win SAM." Doing some research on Windows 2000 and SAM -> NTLM based encryption. "Navigating 2 d win SYS thirty two config SAM U find: 0E7FDE76B8A417953D640D5CDB0D9B72" Go use your favorite NTLM password cracker, and you will get the flag.
Tool unlock: hack IOMEGA_DRIVE wit ZIP_DISK
Answer: hack flag wit m3atl0af
What Did You Learn Today: A lot of computers out there are not running the latest and greatest operating systems. In fact many of our Win 2000/XP era PCs are still in the wild. If you find one the Security Account Manager (SAM) is located at %SystemRoot%/system32/config/SAM and it will have NTLM encryption. Which can be cracked faster than Matt Damon giving you a wink.
Challenge 9 - CRYPTO/ENCODING Slackbot
Theres a robotic HED on d ground, bt it iz lacking d milliamps.FAC & reminds of U of pure annoyance.
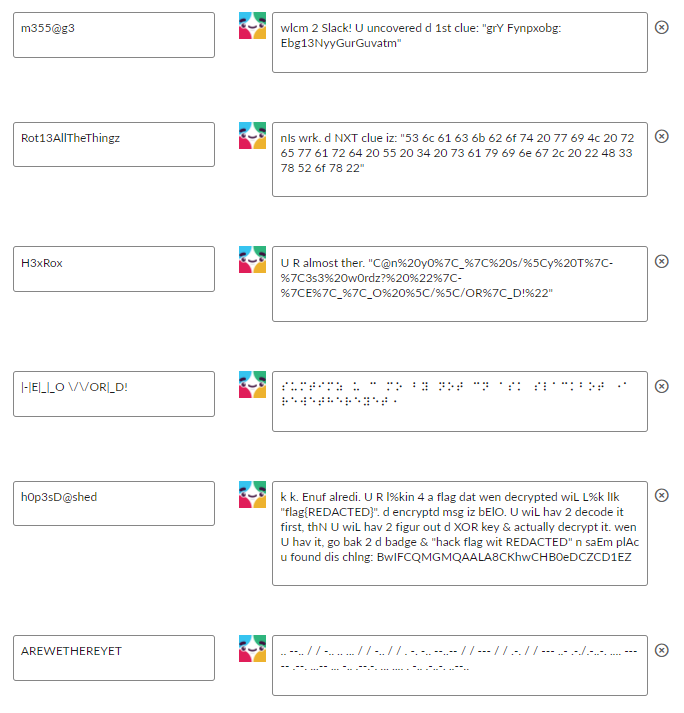
Description: Lets face it we all hate slackbot. But we don't believe anyone has ever roped in that bastard to a CTF puzzle with its creeper responses. So there's a first right? There are plenty of hints once you perform the tool/target hack, such as ""U cn ask me simpl questions bout how Slack works,o jst typ a few keywords lIk "m355@g3" bt TLK 2yorself so others lIk guvment dun knO"" and "Blu grEn red yeLo w two eyes som brows & wot d fuk iz dat a nose o mouth?!" So go hop in our public slack, and not to ruin it for other, but start a DM with yourself (where slackbot will reply). This leads to a chain of events based on its responses. Here's a screenshot of the Slackbot canned responses:
- m355@g3 -> grY Fynpxobg: Ebg13NyyGurGuvatm -> ROT13 -> teL Slackbot: Rot13AllTheThingz
- Rot13AllTheThingz -> 53 6c 61 63 6b 62 6f 74 20 77 69 4c 20 72 65 77 61 72 64 20 55 20 34 20 73 61 79 69 6e 67 2c 20 22 48 33 78 52 6f 78 22 -> HEX 2 ASCII -> Slackbot wiL reward U 4 saying, "H3xRox"
- H3xRox -> C@n%20y0%7C_%7C%20s/%5Cy%20T%7C-%7C3s3%20w0rdz?%20%22%7C-%7CE%7C_%7C_O%20%5C/%5C/OR%7C_D!%22 -> URL Decode -> C@n y0|_| s/\y T|-|3s3 w0rdz? "|-|E|_|_O \/\/OR|_D!"
- |-|E|_|_O \/\/OR|_D! -> ⠎⠥⠍⠞⠊⠍⠵⠀⠥⠀⠉⠀⠍⠕⠀⠃⠽⠀⠝⠕⠞⠀⠉⠝⠀⠁⠎⠅⠀⠎⠇⠁⠉⠅⠃⠕⠞⠀⠐⠁⠗⠑⠺⠑⠞⠓⠑⠗⠑⠽⠑⠞⠐ -> Brail Decode -> sumtimz u c mo by not cn ask slackbot ⠐arewethereyet⠐
- AREWETHEREYET -> .. --.. / / -.. .. ... / / -.. / / . -. -.. --..-- / / --- / / .-. / / --- ..- .-./.-..-. .... ----- .--. ...-- ... -.. .--.-. ... .... . -.. .-..-. ..--.. -> Morse Decode -> IZ DIS D END, O R OUR "H0P3SD@SHED"?
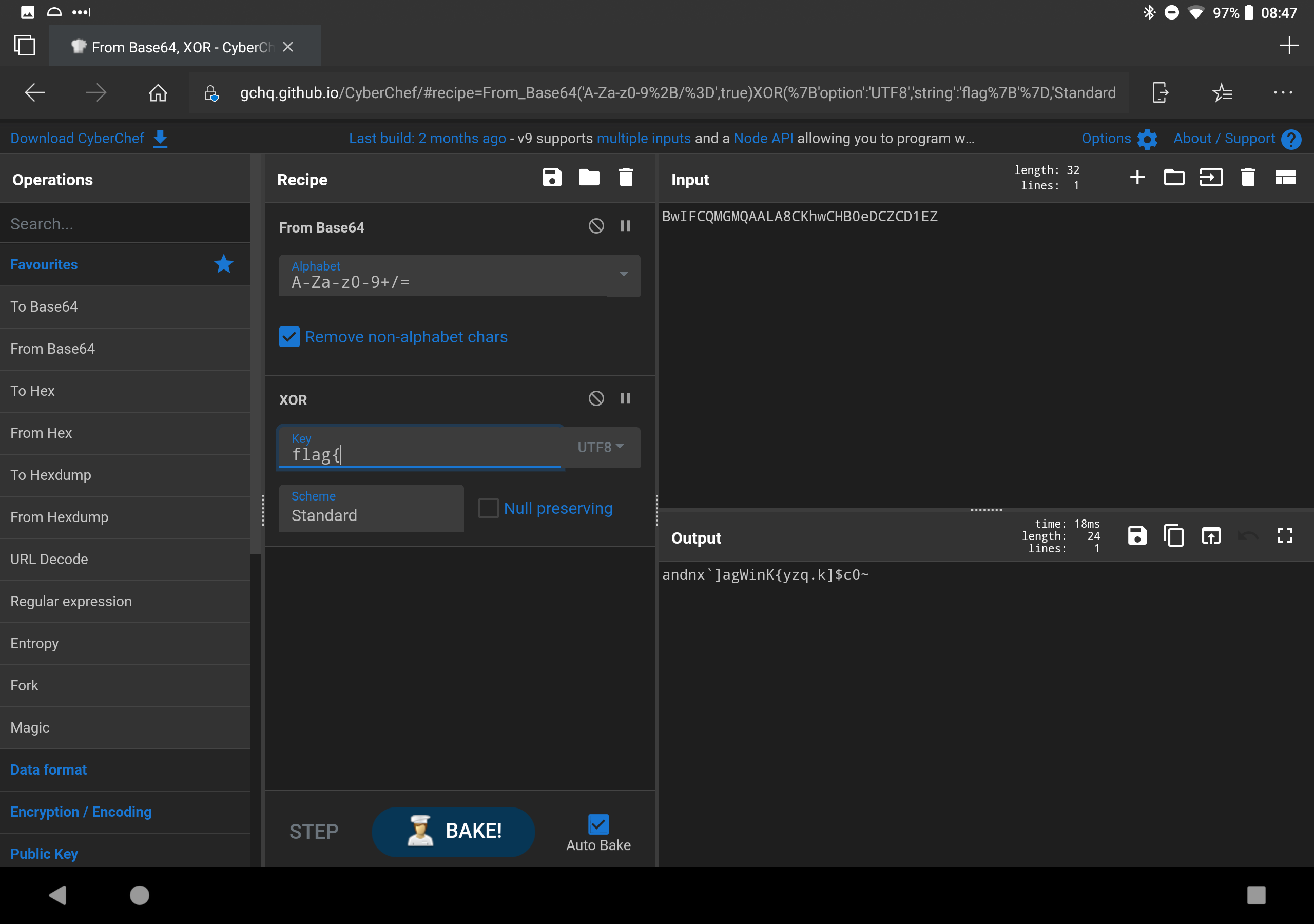
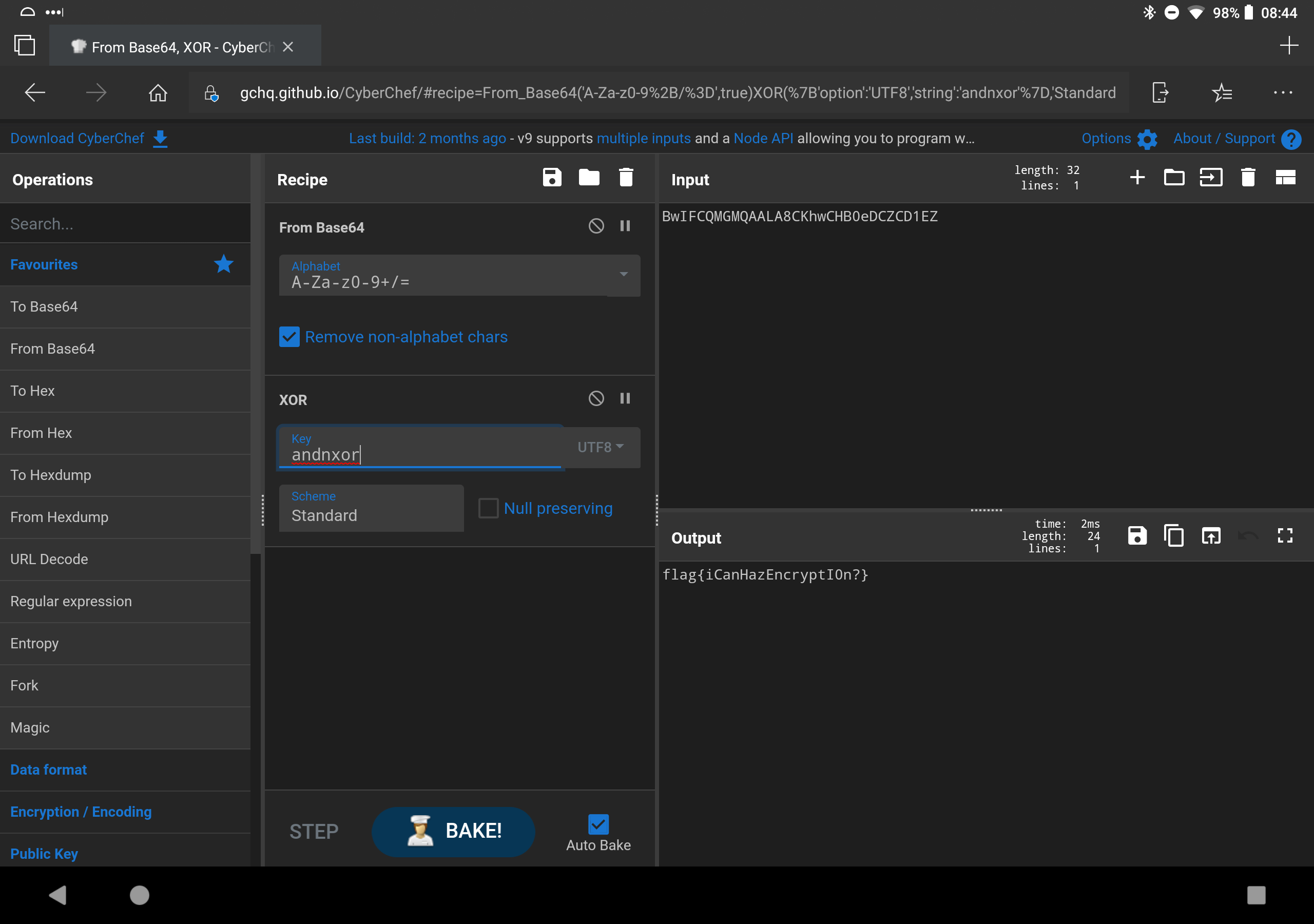
- h0p3sD@shed -> k k. Enuf alredi. U R l%kin 4 a flag dat wen decrypted wiL L%k lIk "flag{REDACTED}". d encryptd msg iz bElO. U wiL hav 2 decode it first, thN U wiL hav 2 figur out d XOR key & actually decrypt it. wen U hav it, go bak 2 d badge & "hack flag wit REDACTED" n saEm plAc u found dis chlng: BwIFCQMGMQAALA8CKhwCHB0eDCZCD1EZ -> TIME TO ACTUALLY DO SOME WORK. So at this point you have to start brute forcing. That is a Base64 encoded message, so decode it from B64 before attempting to decrypt it. Since you know it looks like "flag{.." you already know the first 5 characters. Keep going. Eventually you can figure out it is "iCanHazEncryptI0n?"
![]()
But that is the LONG way. Notice it's XOR? That means there is an inverse relationship between the flag and the key. After you see the begining, you can probably guess "andn..." completes as "andnxor" so swap the key for andnxor and you will see..
![]()
Shout out to Kur3us, he designed this puzzle and its awesome IMHO. Also a great tool for things like this is CyberChef.
Tool unlock: hack HED wit BATTERY
Answer: hack flag wit iCanHazEncryptI0n?
What Did You Learn Today: The XOR property -> if a XOR b = c, then a XOR c = b.
Challenge 10 - CRYPTO/ENCODING Storyline Recap Challenge
WTF hapnd 2 DIS world since DC27? WeL AND!XOR rOt it n a note, tore it up, &...itz randomly spred throughout d wrld. Hav :) putting it bak 2geder 4 recap
Description: Its pretty self explanatory. The final note has been broken into pieces and spread randomly throughout the map which you will find. Collect, save them, decode them, and piece it together to tell the story. To make it easier, here's a dump from the header file...
#define RECAP_00 "44 20 64 63 32 37 20 61 6e 64 21 58 6f 72 20 6e 75 63 6c 65 61 72 20 77 6e 74 72 20 62 61 64 67 65 20 26 20 68 61 63 6b 66 6f 72 73 61 74 61 6e 20 70 61 6e 64 65" #define RECAP_01 "6d 69 63 20 62 61 64 67 65 20 67 6f 74 20 64 72 75 6e 6b 2c 20 68 6f 6f 6b 64 20 75 70 2c 20 26 20 63 61 75 73 65 64 20 44 20 72 6f 6e 61 20 66 72 6d 20 73 6f 6d" #define RECAP_02 "20 6d 65 73 73 65 64 20 5e 20 73 74 64 2e 20 74 68 6e 20 64 65 66 20 43 6f 6e 20 77 7a 20 63 61 6e 63 65 6c 6c 65 64 2e 20 34 20 72 65 61 6c 73 69 65 73 2e 20 73" #define RECAP_03 "69 6e 63 65 20 74 68 6e 20 77 65 76 65 20 73 70 72 65 64 20 72 75 6d 6f 72 73 20 63 75 7a 20 77 65 20 72 20 3a 22 29 20 62 6f 75 74 20 64 20 68 25 6b 20 5e 2e 20" #define RECAP_04 "72 75 6d 6f 72 73 20 73 75 63 68 20 6c 69 6b 20 69 74 20 77 7a 20 62 61 74 73 2c 20 35 20 67 20 63 65 6c 20 74 6f 77 65 72 73 2c 20 62 69 72 64 73 2c 20 62 69 6c" #define RECAP_05 "6c 20 67 61 74 65 73 20 74 72 79 69 6e 67 20 32 20 6d 41 6b 20 6d 6f 6e 65 20 6f 66 66 20 6f 66 20 76 61 63 63 69 6e 65 73 2c 20 63 6f 6e 76 69 6e 63 69 6e 67 20" #define RECAP_06 "70 6f 74 75 73 20 32 20 63 6f 6e 76 69 6e 63 65 20 75 20 32 20 64 72 69 6e 6b 20 42 6c 65 61 63 68 2e 2e 2e 20 66 20 55 20 62 6c 65 76 20 6e 65 20 6f 66 20 64 61" #define RECAP_07 "74 20 55 20 72 20 64 75 6d 62 2e 20 31 30 30 30 25 20 66 6b 6e 20 6c 75 67 2e 20 63 6f 72 6f 6e 61 76 69 72 75 73 20 73 75 78 20 26 20 64 65 2d 72 61 69 6c 65 64" #define RECAP_08 "20 6f 75 72 20 61 6e 6e 75 61 6c 20 63 6f 6e 20 78 70 65 72 65 6e 73 2e 20 69 67 6e 6f 72 20 61 6c 20 64 61 74 20 64 75 6d 62 20 73 63 68 65 74 20 26 20 68 61 76" #define RECAP_09 "20 3a 29 20 68 61 63 6b 69 6e 67 20 64 69 73 20 62 61 64 67 65 2e 20 77 65 20 68 6f 70 20 69 74 20 62 72 69 6e 67 73 20 55 20 3a 29 20 26 20 68 61 70 65 6e 73 2e" #define RECAP_10 "20 55 20 73 68 75 64 20 68 61 63 6b 20 66 6c 61 67 20 77 69 74 2e 2e 2e 75 70 70 52 20 63 61 73 65 2e 2e 2e"
Lets translate this with a hex to ascii...
D dc27 and!Xor nuclear wntr badge & hackforsatan pandemic badge got drunk, hookd up, & caused D rona frm som messed ^ std. thn def Con wz cancelled. 4 realsies. since thn weve spred rumors cuz we r :") bout d h%k ^. rumors such lik it wz bats, 5 g cel towers, birds, bill gates trying 2 mAk mone off of vaccines, convincing potus 2 convince u 2 drink Bleach... f U blev ne of dat U r dumb. 1000% fkn lug. coronavirus sux & de-railed our annual con xperens. ignor al dat dumb schet & hav :) hacking dis badge. we hop it brings U :) & hapens. U shud hack flag wit...uppR case...The challenge at this point, notice all of the upper case letters. Put them togther.
Tool unlock: none
Answer: hack flag wit DXDCABUUUUR
What Did You Learn Today: More HEX? The Grind? Maybe that messages can be hidden inside of other messages? That Hyr0n has a thing for HackForSatan? Maybe... But really that we heart you all. Its been a crazy year with a lot of crazy things being said. Like the recap message says, we hope this years hacker project brought you some smiles and happiness, and that you learned something new.
-
CTF Results & Walkthrough
08/14/2020 at 01:44 • 0 commentsDC28 AND!XOR BENDERPISS CTF Stats
132 Players on the Scoreboard / 5 Fake Hacked Players / 60 Flags Possible
21 Main Challenges
3 Bonus Challenges
36 Easter Eggs
Concept
Our CTF has never been about cutthroat competition, its about exploration, learning, and being a hacker. You can take whatever route you want, if you are just trying to bag points, and that makes you happy, then you do you. The BENDER CTF (BENDERPISS variant this year), is multidisciplinary in approach. We always want people out of their comfort zone and having to learn something new, which hopefully drives them to visit villages and learn. Beating a dead horse, its not a demonstration of skill sets you have, but rather giving you an opportunity to acquire some new ones and frendz along the way. That being said, the scoreboard can be misleading, seeing someone in first place and thinking "they won." We've never flat out said the person in first "won" the CTF, rather we take time to watch what people are doing, hide some land mines to detect those who take the easy path of point gathering, but also watch how the participants react to those land mines, as well as socialize withing their new community. We also take this approach, because participants have the badge in hand. What are land mines? Flags hidden in the firmware which could only be obtained by dumping it from the MCU or extracting from the patch. If you entered any of these (which we mix with the actual challenge flags), we know that's what you were doing because there's no other way to get them. Some were negative (-1000) some were positive (+10). We know what u did last summer. You can mitigate this at times with additional hardware security, but its hardware. If you have physical access to hardware there is NOTHING you can do to protect it, firmware can be dumped or even GDB used to step through in real time. Additionally we had to post a necessary patch during the CTF, which some instantly went straight to reversing and string dumps to find flags. Doing this doesn't disqualify one from the CTF, in fact it makes it harder because each land mind awards you -1000 points.
That being said, there are a few categories which we will give shout outs to those who stood out, based on the types of flags they submitted and generally how their discovery went in chat.
Category Champions
TLDR: These few will receive DC29 AND!XOR badges and a beverage in Vegas (if DEF CON isn't canceled).
S@g@n++: Based on discovery, learning, and not taking the easy path. The 3 persons with the most correct flags submitted, without any land mines, and completing the challenges as designed.
- Night [xxxaf6] & 5p0rk[xxxa85] & Babint[xxxa16]
- Comments: Additionally Night used some python wizardry to map a PS4 and DDR floorpad controller, hacked it into the control input, then used it to for the grind of exploring the 8-bit ASCII world overlay.
S@g@n--: Based on discovery, learning, and not taking the easy path. The 3 persons with the most correct flags submitted, without any negative land mines, and dabbled in some firmware RE.
- Down [xxx128] & Bearto[xxxa1c] & Yawg[xxxb92]
- Comments: Completionist, social butterfly on the frendz scale, enough said.
H@x0r: Based on learning the CTF system, exploiting it, and overcoming the negative score. The person with ALL flags submitted (i.e. including the positive and negative land mines & reset), highest score in the positive.
- teHbrw [xxxab0] with a score of 1293
- Comments: You may think with all our concept rant about learning and challenges, we would disqualify those who string dumped the firmware? No, praise actually. This is a different challenge. teHbrw was actually at the top of the score board before firmware was every available, then quickly dropped to the bottom. In the negative of thousands! Most would give up at this point. But they kept at it, learned there was a back door to reset ones score to zero, and re-completed the challenges. A true hacker learns a systems, its vulnerabilities, exploits them, accepts pitfalls, and overcomes them. Eventually they made it back near the top 10 on the scoreboard. We commend this journey.
JTAG@5AurA5R3X: Based on actual hardware hacking of the badge to achieve greatness.
- NopNopGoose[xxx015] & SynapticRewrite[d36015]
- Comments: They used a SWD debugger to find where in memory the badge was generating IDs, saw that it was a truncated AES hash of the 96 bit device ID, then using JTAG changed the name. Thereby allowing a single badge to have multiple IDs and names...and Rick Rolled the scoreboard. Then pushed it to 5th place and continually changed the name such that we were always Rick Rolled.
1337: Their only goal was to make their final score 1337
- $kull[xxx7da]
- Comments: No explanation needed. We respect this and the whole channel was cheering for it the past few days.
Walk-through
The walkthrough will expand across a few logs, because Hyr0n managed to exploit the same bug in Hackaday.io that he did last year, where a combination of REDACTED, REDACTED, REDACTED, & REDACTED results in REDACTED... Im responsible and won't publicly disclose. Just know that given the type of information I provide and type, and the length of it, requires 3 logs. Also you may wonder, whats up with the SMS speak? We thought it would be lulzy and an additional challenge to understand what was going on, unless you're a millennial. But we put a blackberry keyboard on there to nerf the millennials. So its fair. Also with such limited screen space, it allowed us to put more context in. Big thanks to whoever made the transl8tit SMS TXT Lingo converter.
While the game outline is in the RTFM log, the basics are this: There is an overworld map, where all challenges and tools are randomly hidden. One must discover them all by walking and looking. Each challenge has an initial lock, where one must hack the appropriate target with a tool; i.e. "hack lock wit lockpick", at that point further information is released and one can continue with the challenge.
Master Challenge Unlock (incase you didnt make enough frendz):
> hack flag wit NEVERGONNAGIVEYOUUPNEVERGONNALETYOUDOWN
Challenge 0 - OSINT Twitter
Wut? Itz MrBill. Hes trying 2 coLec OSINT on Hs net of hard hat SD haXor fam.StA classy & giv him wot he wants.
Description: This is a passive OSINT challenge. Many thought it was social engineering and actively kept trying to get a hold of poor MrBill. Lulz. Anyway if you searched through Twitter you would eventually come across hints, such as MrBill has SD (San Diego) hax0r fam. Stay Classy is a hint of Ron Burgundy (the official mascot of DC858/619). More importantly a Mr Bill tweet during BSides San Diego of people calling the payphone to leave their social security number, overwhelmingly resulted in 420-69-1337.
Tool unlock: hack OSINT wit MALTEGO
Answer: hack flag wit 420-69-1337
What Did You Learn Today: That Twitter is a good source of OSINT and the most common SSN is 420-69-1337
Challenge 1 - CRYPTO/ENCODING Keyboard Walk
U find a locked Q10 w tiny ENGRAVING. itz asking 4 a PW.A BIRB flies overhead, you l%k ^ & 2 d L
Description: This is somewhat of a riddle for solving an encoded keyboard walk. Once you hack the target with tool, you can read that "on d bak d following iz inscribed: tzizcz." Combine "tzizcz" with the initial information, you look up "^" and to "2" the "d" left "L." Doing a blackberry keyboard shift cipher of up and to the left for "tzizcz" results in "canada" (that weird place full of EvilMog's and white walkers).
Tool unlock: hack ENGRAVING wit AMSCOPE
Flag: hack flag wit canada
What Did You Learn Today: Ensure your cracking wordlist contains keyboard walks enumerated with shift cyphers, they are more common than you think.
Challenge 2 REVERSE ENGINEERING Derbycon Trevor Firmware
Theres an elctrnk bug. ! d NSA kind bt d ROACH frm con kind. PrograMn INTRFAC exposed. f only U c%d hack dis HW.
Description: This is a re-hash of one of our Trevor 2.0 badge challenges from the last Derby Con. It was fair to re-hash because we only made 40 of those ;) Essentially you get a dump of the firmware and are looking for the secret word, this is a novice RE challenge as all you do is dump strings on the binary to find the password ROUNDERS. But the hints? After completing the initial tool/target hack you see "D mny bug badge blings raw whIl itz binary dumps.Itz az f frm warez iz jst hidden n pln cite" Well its hidden in plain site and talks about bling... looking in the badge SPI storage for bling you'll notice DERBY.RAW, which if you do a long listing you notice its executable (or you could have deduced there was never any DERBYCON bling on the badge, so WTF is this? Executing the program asks for a password and simply checks the input for a string comparison, which is an easy $strings DERBY.RAW dump.
Tool unlock: hack INTRFAC wit ICEDEBUGGER
Flag: hack flag with ROUNDERS
What Did You Learn Today: Dumping strings on firmware is always a good first step.
Challenge 3 REVERSE ENGINEERING Find The E-mail Address
U cUm ax a supa secure medical LAPPY covered n stickers. It hz a TACO_CORP_PROMPT on itz scrEn.
Description: Yet another bullshit RE challenge, the best kind. This is not super difficult, we would place it as medium, but its above a novice attempt (so don't feel bad if it gave you trouble). So the laptop is locked, what better way to backdoor in than with a rubber ducky? Execute the tool/target hack combo to unlock further details. You can now see "D credz auth binary wz XtractD. wot acownt iz Usd 2 login? Saved undRyouZer binz..."" So, once again look under your SPI flash "BIN" directory and behold there's a binary. You should reverse that shit. If you need a basic intro to Ghidra (I like Cutter as well) you can find many resources online, but we wrote one up last year as well. Follow the general process, look at the control flow graph of the binary to see how it works and where its decision branch points are in the logic. Then systematically rename the variables to things which make sense to you (or dont, I'm not the boss of you). Keep in mind, we may have put lots of extra shit (i.e. red herrings) in the binary which have absolutely nothing to do with its operation. Its just more fun that way. So the best way to go through this is generally figure out what is going on and iteratively decompose...
undefined8 main(uint32_t argc, char **argv) { int64_t iVar1; char cVar2; int32_t iVar3; undefined8 uVar4; int64_t in_FS_OFFSET; char **s2; uint32_t var_74h; int32_t c; int32_t var_64h; int32_t var_60h; int32_t var_5ch; int32_t var_58h; uint32_t var_54h; uint32_t var_50h; uint32_t var_4ch; int32_t var_48h; uint32_t var_44h; char *filename; undefined8 stream; int32_t var_2ch; int32_t var_28h; char *s1; int32_t var_15h; char var_11h; char var_10h; int32_t canary; iVar1 = *(int64_t *)(in_FS_OFFSET + 0x28); if (argc == 2) { uVar4 = sym.imp.fopen(".temp", 0x2035); sym.imp.fputc(0x47, uVar4, uVar4); sym.imp.fclose(uVar4); s1._0_1_ = '\0'; sym.imp.strcat(&s1, argv[1], argv[1]); if (((int32_t)(char)s1 - 0x30U & 0x3fffffff) == 8) { _obj.x00 = 1; } if (((s1._1_1_ == 'G') && (s1._2_1_ == 'A')) && (s1._3_1_ == 'T')) { _obj.x01 = 1; _obj.x02 = 1; _obj.x03 = 1; } iVar3 = sym.imp.atoi(); if ((iVar3 + 1) % 0x24 == 0) { _obj.x04 = 1; _obj.x05 = 1; } if (s1._6_1_ == '@') { _obj.x06 = 1; } var_64h = 7; while (var_64h < 0xb) { // switch table (26 cases) at 0x204c switch(*(undefined *)((int64_t)&s1 + (int64_t)var_64h)) { case 0x41: if (var_64h == 8) { _obj.x08 = 1; } break; case 0x42: if (var_64h == 8) { _obj.a02 = 1; } break; case 0x43: if (var_64h == 9) { _obj.a03 = 1; } else { if (var_64h == 10) { _obj.a03 = 1; } } break; case 0x44: if (var_64h == 7) { _obj.a04 = 1; } break; case 0x45: if (var_64h == 8) { _obj.a05 = 1; } break; case 0x46: if (var_64h == 9) { _obj.a06 = 1; } else { if (var_64h == 10) { _obj.a06 = 1; } } break; case 0x47: if (var_64h == 7) { _obj.a07 = 1; } break; case 0x48: if (var_64h == 8) { _obj.a08 = 1; } break; case 0x49: if (var_64h == 9) { _obj.a09 = 1; } else { if (var_64h == 10) { _obj.a09 = 1; } } break; case 0x4a: if (var_64h == 7) { _obj.a10 = 1; } break; case 0x4b: if (var_64h == 8) { _obj.a11 = 1; } break; case 0x4c: if (var_64h == 9) { _obj.a12 = 1; } else { if (var_64h == 10) { _obj.a12 = 1; } } break; case 0x4d: if (var_64h == 7) { _obj.a13 = 1; } break; case 0x4e: if (var_64h == 8) { _obj.a14 = 1; } break; case 0x4f: if (var_64h == 9) { _obj.a15 = 1; } else { if (var_64h == 10) { _obj.a15 = 1; } } break; case 0x50: if (var_64h == 7) { _obj.a16 = 1; } break; case 0x51: if (var_64h == 8) { _obj.a17 = 1; } break; case 0x52: if (var_64h == 9) { _obj.a18 = 1; } else { if (var_64h == 10) { _obj.a18 = 1; } } break; case 0x53: if (var_64h == 7) { _obj.a19 = 1; } break; case 0x54: if (var_64h == 8) { _obj.a20 = 1; } break; case 0x55: if (var_64h == 9) { _obj.a21 = 1; } else { if (var_64h == 10) { _obj.a21 = 1; } } break; case 0x56: if (var_64h == 7) { _obj.x07 = 1; } break; case 0x57: if (var_64h == 8) { _obj.a23 = 1; } break; case 0x58: if (var_64h == 9) { _obj.x09 = 1; } else { if (var_64h == 10) { _obj.x10 = 1; } } break; case 0x59: if (var_64h == 7) { _obj.a25 = 1; } break; case 0x5a: if (var_64h == 8) { _obj.a26 = 1; } } var_64h = var_64h + 1; } if (((_obj.x07 != 0) && (_obj.x08 != 0)) && ((_obj.x09 != 0 && (_obj.x10 != 0)))) { _obj.x06 = 1; } if (((int32_t)var_15h._1_1_ + (int32_t)(char)var_15h == 0x67) && ((int32_t)var_15h._1_1_ - (int32_t)(char)var_15h == 1)) { _obj.x11 = 1; _obj.x12 = 1; } if (var_15h._2_1_ == '.') { _obj.x13 = 1; } iVar3 = sym.rot13((int32_t)var_15h._3_1_); if ((iVar3 == 0x3d) && (iVar3 = sym.rot13((int32_t)var_11h + 1), iVar3 == 0x60)) { _obj.x14 = 1; _obj.x15 = 1; } uVar4 = sym.imp.fopen(".temp", 0x2038); iVar3 = sym.imp.fgetc(uVar4); sym.imp.fclose(uVar4); sym.imp.remove(".temp"); if (iVar3 == (int32_t)var_10h) { _obj.x16 = 1; } cVar2 = sym.getCRC((char *)&s1, 0x10); if (cVar2 == '\x0f') { _obj.crc = 1; } if ((((((_obj.x00 == 0) || (_obj.x01 == 0)) || (_obj.x02 == 0)) || ((_obj.x03 == 0 || (_obj.x04 == 0)))) || ((((_obj.x05 == 0 || ((_obj.x06 == 0 || (_obj.x07 == 0)))) || (_obj.x08 == 0)) || ((((_obj.x09 == 0 || (_obj.x10 == 0)) || (_obj.x11 == 0)) || (((_obj.x12 == 0 || (_obj.x13 == 0)) || ((_obj.x14 == 0 || ((_obj.x15 == 0 || (_obj.x16 == 0)))))))))))) || (_obj.crc == 0)) { sym.imp.puts("FAILZ!"); } else { sym.imp.puts(0x203a); } } else { sym.imp.puts("DFIU OnRy 1 arg nEdd n allowD!"); } uVar4 = 0; if (iVar1 != *(int64_t *)(in_FS_OFFSET + 0x28)) { uVar4 = sym.imp.__stack_chk_fail(); } return uVar4; }Yeah it looks cleaner in Ghidra or Cutter (which uses Ghidra as its decompiler BTW and doesn't require JAVA). So logically going through it, and you will see its evaluating every charachter of the input string to meet certain criteria. So figure out how you make each character meet such criteria. Easy enough right?
- Check if 2 args or fail (i.e. run the program with the expected input as an argument)
- Create a file pointer
- Create some strings (red herring)
- Lets call input x, check x[0] = 8 - Check if atoi(i) * 4 = (int) ' ' -> Does 8x4 = 32
- Check x[1] = G - Convert GAT to binary (01000111 01000001 01010100)
- Check x[2] = A - XOR wit (01000011 00000000 00000000)
- Check x[3] = T - Does it equal = (0)0000100 1000001 01010100)
- Check x[4] = 3 - STR cat x4 and x5 together, does atoi(x4x5) % 35 == 0
- Check x[5] = 5 - ----> Combine them, convert to integer, is that int a multiple of 35?
- Check x[6] = @ - Check if it is @ (DECIMAL VALUE 64)
- Check x[7] = V -> Lets do a loooong ass switch statement , set bools for 7..10
- Check x[8] = A
- Check x[9] = X
- Check x[10] = X
- Check x[11]= 3 -> is x11 + x12 (ASCII) = 51 + 52 ==> does it equal 103 && x12-x11 = 1
- Check x[12]= 4
- Check x[13]= . -> "." is 46, + = 43, - = 45 ----> 45(-) + 43(+) - 42(*) == x13(46 .)
- Check x[14]= 0 -> rot13 check is it 61
- Check x[15]= R -> rot13+1 check is it 96
- Check x[16]= G -> create a file at the begining, save a G...check it at the very end.
- Open that file we started with, double check x[16] == G
- Check x[17] for a CRC that matches 0xF, which is the CRC of 8GAT35@VAXX34.0RG
Why does the CRC matter? Because there are multiple ways to satisfy the criteria. So in a way you could have thought you were correct, get to the end and the CRC fails. LOLZ. Also for a cleaner look, here's the actual C code...
/***************************************************************************** * Made with beer and late nights in California. * * (C) Copyright 2017-2020 AND!XOR LLC (https://andnxor.com/). * * PROPRIETARY AND CONFIDENTIAL UNTIL AUGUST 11th, 2020 then, * * Licensed under the Apache License, Version 2.0 (the "License"); * you may not use this file except in compliance with the License. * You may obtain a copy of the License at * * http://www.apache.org/licenses/LICENSE-2.0 * * Unless required by applicable law or agreed to in writing, software * distributed under the License is distributed on an "AS IS" BASIS, * WITHOUT WARRANTIES OR CONDITIONS OF ANY KIND, either express or implied. * See the License for the specific language governing permissions and * limitations under the License. * * ADDITIONALLY: * If you find this source code useful in anyway, use it in another electronic * conference badge, or just think it's neat. Consider buying us a beer * (or two) and/or a badge (or two). We are just as obsessed with collecting * badges as we are in making them. * * Contributors: * @andnxor * @zappbrandnxor * @hyr0n1 * @bender_andnxor * @lacosteaef * @f4nci3 * @Cr4bf04m *****************************************************************************/ #include <stdio.h> #include <stdlib.h> #include <string.h> typedef int bool; #define true 1 #define false 0 bool x00 = false;bool x01 = false;bool x02 = false;bool x03 = false;bool x04 = false;bool x05 = false;bool x06 = false;bool x07 = false;bool x08 = false; bool x09 = false;bool x10 = false;bool x11 = false;bool x12 = false;bool x13 = false;bool x14 = false;bool x15 = false;bool x16 = false;bool crc = false; bool a01 = false;bool a02 = false;bool a03 = false;bool a04 = false;bool a05 = false;bool a06 = false;bool a07 = false;bool a08 = false;bool a09 = false; bool a10 = false;bool a11 = false;bool a12 = false;bool a13 = false;bool a14 = false;bool a15 = false;bool a16 = false;bool a17 = false;bool a18 = false; bool a19 = false;bool a20 = false;bool a21 = false;bool a22 = false;bool a23 = false;bool a24 = false;bool a25 = false;bool a26 = false; const unsigned char CRC7_POLY = 0x91; unsigned char getCRC(unsigned char message[], unsigned char length) //Borrowed from https://www.pololu.com/docs/0J44/6.7.6 { unsigned char i, j, crc = 0; for (i = 0; i < length; i++) { crc ^= message[i]; for (j = 0; j < 8; j++) { if (crc & 1) crc ^= CRC7_POLY; crc >>= 1; } } return crc; } int rot13(int x){ //This really isn't ROT13, it just adds 13. I want the function name to fuck with people. return x+13; } int main(int argc, char *argv[]) { /********************************************************************************************* * @brief Initialization & Setup : Sekret flag = 8GAT35@VAXX34.0RG **********************************************************************************************/ if (argc != 2) { printf("DFIU OnRy 1 arg nEdd n allowD!\n"); return 0; } else{ /********************************************************************************************* * @brief Initialize Variables **********************************************************************************************/ //Create the file for the last step FILE *fp; char G = 71; char* filename = ".temp"; fp = fopen(filename, "w+"); fprintf(fp, "%c", (char)G); fclose(fp); //Red Herring char hint[] = "flag"; char msg[17]; strcpy(msg,""); strcat(msg,argv[1]); /********************************************************************************************* * @brief Step 00 : Sekret flag = 8GAT35@VAXX34.0RG * x[0] = 8 - Check if atoi(i) * 4 = (int) ' ' -> Does 8x4 = 32? **********************************************************************************************/ if((msg[0] - 48) * 4 == 32){ x00 = true; } /********************************************************************************************* * @brief Step 01 : Sekret flag = 8GAT35@VAXX34.0RG * x[1] = G - Convert GAT to binary (01000111 01000001 01010100) * x[2] = A - XOR wit (01000011 00000000 00000000) * x[3] = T - Does it equal = (0)0000100 1000001 01010100) **********************************************************************************************/ int s01bin00=0b01000011; int s01bin01=0b00000000; int s01bin02=0b00000000; int s01ans00=0b00000100; int s01ans01=0b01000001; int s01ans02=0b01010100; if(((msg[1]^s01bin00) == s01ans00)&&((msg[2]^s01bin01) == s01ans01)&&((msg[3]^s01bin02) == s01ans02)){ x01 = true; x02 = true; x03 = true; } /********************************************************************************************* * @brief Step 02 : Sekret flag = 8GAT35@VAXX34.0RG * x[4] = 3 - STR cat x4 and x5 together, does atoi(x4x5) % 35 == 0? * x[5] = 5 - ----> Combine them, convert to integer, is that int a multiple of 35? **********************************************************************************************/ char step02_str[2]; step02_str[0] = msg[4]; step02_str[1] = msg[5]; int step02_int = atoi(step02_str); if((step02_int + 1) % 36 == 0){ x04 = true; x05 = true; } /********************************************************************************************* * @brief Step 03 : Sekret flag = 8GAT35@VAXX34.0RG * x[6] = @ - Check if it is @ (DECIMAL VALUE 64) **********************************************************************************************/ if (msg[6] == 64){ x06 = true; } /********************************************************************************************* * @brief Step 04 : Sekret flag = 8GAT35@VAXX34.0RG * x[7] = V -> Lets do a loooong ass switch statement , set bools for 7..10 * x[8] = A * x[9] = X * x[10]= X **********************************************************************************************/ char sss[]="xxxxxx"; for (int i=7; i<=10; i++){ switch (msg[i]){ case 'A' : if (i == 8) {x08 = true; strcpy(sss,"abacus");} break; //A case 'B' : if (i == 8) {a02 = true; strcpy(sss,"babies");} break; case 'C' : if (i == 9) {a03 = true; strcpy(sss,"cabala");} else if (i == 10) {a03 = true; strcpy(sss,"cabala");}break; case 'D' : if (i == 7) {a04 = true; strcpy(sss,"dabber");} break; case 'E' : if (i == 8) {a05 = true; strcpy(sss,"eagers");} break; case 'F' : if (i == 9) {a06 = true; strcpy(sss,"fables");} else if (i == 10) {a06 = true; strcpy(sss,"fables");}break; case 'G' : if (i == 7) {a07 = true; strcpy(sss,"gabion");} break; case 'H' : if (i == 8) {a08 = true; strcpy(sss,"habits");} break; case 'I' : if (i == 9) {a09 = true; strcpy(sss,"ibices");} else if (i == 10) {a09 = true; strcpy(sss,"ibices");}break; case 'J' : if (i == 7) {a10 = true; strcpy(sss,"jabber");} break; case 'K' : if (i == 8) {a11 = true; strcpy(sss,"kabala");} break; case 'L' : if (i == 9) {a12 = true; strcpy(sss,"laager");} else if (i == 10) {a12 = true; strcpy(sss,"laager");}break; case 'M' : if (i == 7) {a13 = true; strcpy(sss,"macaws");} break; case 'N' : if (i == 8) {a14 = true; strcpy(sss,"nachos");} break; case 'O' : if (i == 9) {a15 = true; strcpy(sss,"oakums");} else if (i == 10) {a15 = true; strcpy(sss,"oakums");}break; case 'P' : if (i == 7) {a16 = true; strcpy(sss,"packed");} break; case 'Q' : if (i == 8) {a17 = true; strcpy(sss,"qiblas");} break; case 'R' : if (i == 9) {a18 = true; strcpy(sss,"rabbin");} else if (i == 10) {a18 = true; strcpy(sss,"rabbin");}break; case 'S' : if (i == 7) {a19 = true; strcpy(sss,"sabora");} break; case 'T' : if (i == 8) {a20 = true; strcpy(sss,"tables");} break; case 'U' : if (i == 9) {a21 = true; strcpy(sss,"uglier");} else if (i == 10) {a21 = true; strcpy(sss,"uglier");}break; case 'V' : if (i == 7) {x07 = true; strcpy(sss,"vacuum");} break; //V case 'W' : if (i == 8) {a23 = true; strcpy(sss,"wabble");} break; case 'X' : if (i == 9) {x09 = true; strcpy(sss,"xenial");} else if (i == 10) {x10 = true; strcpy(sss,"xenial");}break; //X case 'Y' : if (i == 7) {a25 = true; strcpy(sss,"yabber");} break; case 'Z' : if (i == 8) {a26 = true; strcpy(sss,"zaffer");} break; } } if (x07 && x08 && x09 && x10){ x06 = true; } /********************************************************************************************* * @brief Step 05 : Sekret flag = 8GAT35@VAXX34.0RG * x[11]= 3 -> is x11 + x12 (ASCII) = 51 + 52 ==> does it equal 103 && x12-x11 = 1 * x[12]= 4 **********************************************************************************************/ if((msg[11]+msg[12] == 103) && (msg[12]-msg[11]==1)){ x11 = true; x12 = true; } /********************************************************************************************* * @brief Step 06 : Sekret flag = 8GAT35@VAXX34.0RG * x[13]= . -> "." is 46, + = 43, - = 45 ----> 45(-) + 43(+) - 42(*) == x13(46 .)? **********************************************************************************************/ char sub = 45; char add = 43; char mul = 42; if(sub + add - mul == msg[13]){ x13 = true; } /********************************************************************************************* * @brief Step 07 : Sekret flag = 8GAT35@VAXX34.0RG * x[14]= 0 -> rot13 check is it 61 * x[15]= R -> rot13+1 check is it 96 * x[16]= G -> create a file at the begining, save a G...check it at the very end. **********************************************************************************************/ if((rot13(msg[14])==61) && (rot13(msg[15]+1)==96)){ x14 = true; x15 = true; } //Open that file from step 0...I hope they forgot about it. fp = fopen(filename, "r"); int c = fgetc(fp); fclose(fp); remove(filename); if(c == msg[16]) x16 = true; /********************************************************************************************* * @brief Step 08 : FINAL CHECK OF TRUTH AND CRC (Hex: f / Decimal) **********************************************************************************************/ msg[17] = getCRC(msg, 16); if(msg[17]==0xf) crc = true; if(x00 && x01 && x02 && x03 && x04 && x05 && x06 && x07 && x08 && x09 && x10 && x11 && x12 && x13 && x14 && x15 && x16 && crc){ //TODO CRC printf("SUCCESS!\n"); } else{ printf("FAILZ!\n"); } return 0; } }Oh an yes, do we take shots at the crazy conspiracy theory nuts about COVID19 throughout this entire CTF? OF COURSE. Because Bill Gates is trying to release vaccines in the world and implant you with tracking devices...don't forget tin foil hats provide RF shielding from the trackers.
Tool unlock: hack LAPPY wit RUBBER_DUCKY
Flag: hack flag wit 8GAT35@VAXX34.0RG
What Did You Learn Today: Reverseing compiled software is an extremely useful skillset, don't just live in the world of Python and Javascript, learn C and Assembly / how it works / how its built / and how to tear it apart.
-
RTFM
07/25/2020 at 17:07 • 0 commentsRead The F-ing Manual
Made with beer and late nights in California.
TLDR: This year's badge provides bling, an embedded CTF text-based adventure, and a port of MyBASIC extended to the hardware to make it hackable.
AND!XOR (@andnxor)
* @zappbrandnxor
* @hyr0n1
* @bender_andnxor
* @lacosteaef
* @f4nci3
* @Cr4bf04mArtwork for PCB Silkscreen, Acrylic, Bandanna, & Lanyard: Doc
VOIP Service Puzzle, Greetings, and Lulz: Alethe Denis (@AletheDenis) at Penguin
Puzzle Design & Intern of the Month Award Jun: Will Caruana (@WillCaruana)
Puzzle Design & Beta Testing: Kur3us (@kur3us)
Filming & Editing: Mike Laan (@mlaan)
Sponsors: Urbane Security, Penguin, inspectAR, & Philanthropists
Hackaday: https://hackaday.io/project/173627-andxor-dc28-badge
GitHub: https://github.com/ANDnXOR/ANDnXOR_DC28_Badge
Badge Hardware
Hardware information about the badge
BOM
* PCBA: MacroFab
* Acrylic Faceplate: Ponoko
* MCU: STM32F412RET6
* Screen (OLED): ER-OLED0.96-1.3B-1655
* Screen (TFT): ST7735 128x160
* LEDS: APA-102C-NEW
* Keyboard: Blackberry Q10 (BBKB)
* Keyboard Connector: BM14B(0.8)-24DS-0.4V(53)
* 8 MHz Crystal (STM32): X50328MSB2GI
* USB-C: TYPE-C-31-M-12
* Battery Holder: Keystone 1020Inspect AR
Want to inspect the badge without disassembling the acrylic faceplate?
We've partnered with InspectAR to leverage augment reality to just do that.
* Website: https://www.inspectar.com/
* Google Play Store: https://play.google.com/store/apps/details?id=com.inspectar.app
* Apple App Store: https://apps.apple.com/us/app/inspectar-pcb-tools/id1478936899
* Nokia Sidekick Store: http://bit.ly/2PToehAfter installing the app on your phone, login and select "Sponsored" projects, search for "AND!XOR DC28," and download.
Badge Interface Usage
* Move Up: SYM+W
* Left: SYM+A
* Down: SYM+S
* Right: SYM+D
* Quit/back: SYM+Q
* Delete: ALT+Backspace
* Use ALT to type alternate characters _(e.g., ALT+B == !)_
* Special Characters
* { : SYM+U
* } : SYM+I
* \ : SYM+G
* = : SYM+L
* [ : SYM+T
* ] : SYM+Y
* % : SYM+P
* ~ : SYM+V
* & : SYM+$
* ^ : SYM+C
* < : SYM+N
* \> : SYM+M
* | : SYM+F
* Bling Rager Mode: SYM+R (while in bling app)Capture The Flag Scoreboard
https://nevergonnagiveyouupnevergonnaletyoudown.com/
AND!XOR Public SlackOver the past couple of years, hackers engaged in the CTF have setup slack environments to collaborate and learn from one another. We think this is awesome and decided to setup an open slack to support this. There will be channels dedicated to each badge, i.e. DEF CON 28 (WHICH IS CANCELED, THE SAD LOLZ!) is under #dc28. We ask that you abide by only a couple cardinal rules:
* Rule 0 - Don't be an asshole
* Rule 1 - No spoilers...
So Rule 1 is kind of an extension of Rule 0, but it's the grey area. You're going in to slack for many reasons (which will be explained below, see BENDERPISS "frend"), and one of them may be to ask for hints because you want to learn. If you are gonna just spoil it and another wants to know how you completed a challenge, do the world some good and direct message them. Use the channel to be Socratic, answer questions by asking questions leading in the right direction, critical thinking is key to building your hacking proficiency (but if you just want to give it away, be kind enough to use direct messaging). It's a CTF with a scoreboard, so if you just dump an answer into a chat channel, you're only hurting your own score :PAND!XOR Public Slack Sign Up: https://bit.ly/3eRTR4B
Badge Enabled Non Directive Enigma Routine Portable Interface SyStem (BENDER~PISS)
A variant of the BENDER CTF has been created such that it can be played standalone with the BBKB, on the badge, without the use of a serial terminal client. However, the back-end magic MITM wizardry which exists allows you to do both, as whatever you do in BENDERPISS is mirrored over the RS232 connect and vice versa. In fact, we prefer you check it out because it's pretty damn cool. This means you can take BENDERPISS on the go and when you get back to your mother's basement, you can plug it right back in to your 386 DX 66 with turbo button enabled and continue on.
* Recommended Clients
* Putty (GUI based, there's no shame in using a GUI for efficiency)
* Screen (CLI based. 1337 Hax0r sauce. To quit screen terminal, press ctrl+a then press \ )
* Note: Do NOT use minicom as it does not support extended ASCII or CP437
* Note: On Debian based systems this will mount typically as /dev/ttyACM0
* Note: There is a maintenance terminal as well, which can be ignored. It is mounted as ttyACM1 (nix) / COMX+1 (windows)
* Serial Connection Settings
* USB Type C physical interface
* Baud: 115200
* Data Bits: 8
* Stop Bits: 1
* Parity: None
* Flow Control: None
BENDERPISS is a collection of REDACTED hacking challenges which span encoding, encryption, static analysis binary reverse engineering, phreaking, SIGINT, OSINT, and LULZ. Traditionally this is delivered in the text based adventured format (i.e. Colossal Cave), however has been modernized slightly for ergonomics and fun. For example, to traverse the world you no longer type N S E W to move north, south, east, and west; rather W A S D. Also doing this will display an ASCII/ANSI map to give you a sense of your place in the world. To start, the badge will boot you straight into the command line terminal and recommend you type "bender" to get started. While the CTF has CLI help embedded, this file will double as a more detailed explanation given it's hard to fit everything on just one screenCLI: bender
and!xor:~$ bender
* Provides list of all available commands: hack, look, loot, map, w a s d, frend, name, reset & gender.
* Typing a command by itself also provides help in its proper usageCLI: hack
and!xor:~$ hack and!xor:~$ hack TARGET wit TOOL and!xor:~$ hack flag wit ANSWER
* $ hack - provides help on how to use the command
* $ hack TARGET wit TOOL - by hacking a challenge TARGET (which is identified in all caps) with a TOOL things happen... sometimes the badge will do something special...sometimes it unlocks the TARGET further so you can look at it for more information about the TARGET and assist you in completing the challenge. In the latter case you will be told that the hack works and should look at your recently hacked TARGET.
* $ hack flag wit ANSWER - once you believe you have the answer to one of the CTF challenges, type "hack flag wit ANSWER" (whatever you believe that answer is). If it was correct a flag will be generated which you can enter for points on the CTF scoreboard. You must do this at the same location as the challenge (duh).CLI: look
and!xor:~$ look and!xor:~$ look at THING
* $ look - provides general information about your location including a hacking challenge (i.e. You walk in to a bar and see a SHOTGLASS)
* $ look at THING - provides specific information about a THING you may see when you look (i.e. The SHOTGLASS is filled with booze)
* THINGS are identified by being in ALLCAPS. Some THINGS cannot be looked at unless you first "hack" them wit a tool you've looted. Challenges and tools are randomly scattered throughout the world so you should look everywhere...CLI: loot
and!xor:~$ loot and!xor:~$ loot TOOL
* $ loot - provides help on how to use the command
* $ loot TOOL - lets you loot a TOOL you find while looking and add it to your personal loot (see that loot is a verb and a noun, because looting is awesome!)CLI: map
and!xor:~$ map * * * * * * * *** * ***** * * * * * * * * ***** *** * * * * * * * * * *** *** * *** **** * * * ☻ * * ° * ******************
* $ map - displays an ASCII map of where you are in the world
* Key ☻ - That's you!
* Key * - That's a wall!
* Key ° - That's a challenge which you have discoveredCLI: w a s d
and!xor:~$ w and!xor:~$ a and!xor:~$ s and!xor:~$ d
* $ w - walks north in the world
* $ a - walks west in the world
* $ s - walks south in the world
* $ d - walks east in the world
* Before you get all traditional and bitch about why it isn't N S E and W...keep in mind the traditional system was invented before we had tiny keyboards on phones. It just isn't ergonomic. You will be pleased to use your left thumb to navigate and right thumb for hitting return.CLI: frend
and!xor:~$ frend and!xor:~$ frend syn BADGEID and!xor:~$ frend ack X0 X1 X2 X3 X4 X5 X5 X6 X7 X8
* TLDR: First you type frend to see your ID, share it with someone, they frend syn your ID, get a frend flag and share it with you, you frend ack that flag, get an unlock and a CTF socialization flag for points which you enter on the scoreboard. At this point, you and your new friend should swap roles to reciprocate the unlock and earn more points...or not, we're not the boss of you.
* $ frend - provides help on how to use the command. Not all of the BENDERPISS CTF challenges are unlocked by default. A certain number are available to everyone, while some are randomly unlocked on each badge, leaving a handful which each person cannot hack...unless they make frendz who can share their initial unlocked challenges with them... A player runs frend to obtain their BadgeID and gives it to another friend through any means; i.e. carrier pigeon, US Postal Service, HAM Radio, or the AND!XOR public slack. Below you see Hyr0n's BadgeID which he will proceed to give to Zapp.and!xor:~$ frend *Unlock Challngz! 0 U giv ID 2 frend 1 F $frend syn ID 2 F giv U FLAG 3 U $frend ack FLAG 4 Both Profit! Ur BadgeID: f3c5bd Giv dat ID 2 Frendz Deetz in RTFM.MD
* $ frend syn - provides help on how to use the syn subcommand. Using a third argument to insert the BadgeID will then generate a frend flag for exchanging unlocks. This is the first step to generate a frend flag so you can share your unique unlock challenges with your new frend. They tell you their BADGEID (obtained by typing frend). This results in a 9-word flag (e.g. X0 X1 X2 X3 X4 X5 X5 X6 X7 X8) which they must frend ack. Do not confuse this with a flag which is entered on the CTF scoreboard site for points, you can try and nothing will happen. You need to give this flag back to the person who gave you the BadgeID so they can obtain the challenges which you originally had unlocked. Below Zapp is generating a frend flag for Hyr0n (BadgeID f3c5bd).
and!xor:~$ frend syn Ax frend 4 bdge ID. datz thR public key. U nEd 2 encrypt it w yor prv8 key. DFIU! Ex: $frend syn ID and!xor:~$ frend syn f3c5bd FREND FLAG: lucky peons aimed color tweak sling grind lurks fired Giv Bak 2 Frend 4: $frend ack FLAG
* $ frend ack - provides help on how to use the ack subcommand. Using a third argument to insert ack X0 X1 X2 X3 X4 X5 X5 X6 X7 X8 will unlock whatever challenge was unlocked by default from your frend (whoever syn'd it to you). Since the frend flag is encoded by your frendz BADGEID (i.e. public key), and decrypted with their private key, it can't be used by others. This is one sexy symmetric non-reputable relationship. There is a chance that you are making frendz with someone who has the same unlock as you, so you may get somewhere between 0..3 challenges unlocked (like below). That's okay, go make MORE friends. Once a syn ack is complete a score board flag is created, that's right, you and your new frend get points for socializing. Also, if you both then syn/ack in reverse, you get double points and both have the same uniquely generated unlocks from one another's badges! That's your motivation to be a good human and not a dick. Below Hyr0n is performing an ack of the frend flag send to him from Zapp.
and!xor:~$ frend ack Did SOME1 GIV U a frend FLAG? Decrypt it here, git thR bAs unlocks & a flag 4 points. DFIU! Ex: $frend ack FLAG and!xor:~$ frend ack lucky peons aimed color tweak sling grind lurks fired Succesful ACK! 1 Chlngz unlocked go find dem Sc0r3brd Points: plaid whams fouls recur blood braid seats scarf idler bit.ly/3egadD5
CLI: name
and!xor:~$ name and!xor:~$ name XXXXXXX
* $ name - provides help on how to use the command
* $ name XXXXXX - sets your name (max length 6 characters) and generates a flag
* Enter that flag on the score board to associate your nameCLI: name
and!xor:~$ reset and!xor:~$ reset Y
* $ reset - provides help on how to use the command
* $ reset Y - resets the BENDER CTF to its default factory (our garage) settingsCLI: gender
and!xor:~$ gender and!xor:~$ gender X and!xor:~$ gender F and!xor:~$ gender M
* $ gender - provides help on how to use the command
* $ gender X - sets the profile gender to non-binary
* $ gender F - sets the profile gender to female
* $ gender M - sets the profile gender to male
* This customizes the output header when viewing your lootBling
The badge allows you to change the bling mode, LED blink modes, add custom bling, and photos.
Shortcuts
The keyboard changes the bling and LED modes.
Rager Mode Toggle (SYM+R)Bling (Animations) Modes
* (A) Aeon Flux Eye
* (B) Nyan Cat
* (D) Dance
* (E) Eye
* (F) Flames
* (G) Hypnotoad
* (R) Rick Astley
* (S) Remember Me!
* (T) Netscape
* (v) Bender
* (W) Fry
* (X) Custom Bling
* (Y) Rick & Morty
* (Z) Max HeadroomLED Modes
* (C) Bling kills COVID19
* (I) Sparkle
* (J) Evil Grin
* (K) Meteor
* (O) Rainbow
* (P) Fade
* (Q) Demonstration
* (U) DEF CON is canceledCustom Bling
Generate your own RAW file from MP4, PNG, or GIF using the following ffmpeg command:
ffmpeg -i -y -vf "scale=128:64:force_original_aspect_ratio=decrease,pad=128:64:(ow-iw)/2:(oh-ih)/2" -r 16 -f rawvideo -s 128x64 -pix_fmt monob CUSTOM.RAW
Goto Settings and select the "Pause Bling" toggle.
Overwrite `CUSTOM.RAW` file in `BLING_BW/` on the badge.
Run custom bling using `x` key while in the Bling app.Decoder
Did you find a 6-digit code hidden by AND!XOR on the badge, phone service, bathroom stall, or out on the information superhighway?
Enter it here for a scoreboard flag unique to your ID.Photos
Photos app browses pictures (.RAW files) in `PIX/` on the badge. The badge can only display raw RGB565 files due to limited processing power.
Generating RAWs from Photos
ffmpeg -i -y -vf "scale=160:128:force_original_aspect_ratio=decrease,pad=160:128:(ow-iw)/2:(oh-ih)/2" -r 5 -f rawvideo -s 160x128 -pix_fmt rgb565be .RAW
Goto Settings and select the "Pause Bling" toggle.
Next, copy the .RAW file to `PIX/` folder on the badge.
Finally run the Photos app view the photo. Cycle photos with `n`, `p`, `a`, or `d`.MY-BASIC
Run MY-BASIC programs (.BAS) located on the SPI flash storage.
Yep. The badge runs MY-BASIC and has been extended to control the badge hardware (LEDs, Screen, Temperature Sensor, & Voltage Sensor) as well! The badge is now hackable with a simple programming language. MY-BASIC is limited compared to traditional BASIC, but very powerful.
Source: https://github.com/paladin-t/my_basicMY-BASIC Edit
Edit BASIC program (.BAS) located on the SPI flash storage from the badge. For detailed information about how MY-BASIC works and coding practices...
RTFM: https://paladin-t.github.io/my_basic/MY-BASIC%20Quick%20Reference.pdf
Our portable MY-BASIC IDE native to the badge makes it easy to tweak your code on the badge. You can develop an entire program without anything else but the badge, but this may present a challenge given the screen size and language format (i.e. subroutines and loops require indentation of 8 spaces). It may be a stretch to call this an IDE, but it is MY-BASIC... Note that all changes are saved upon exit. If you mess something up, download the originals from GitHub.Debugging
Edit the files here and when you run them, if there is an error you will be presented with useful information:
* Debug Message: The error which is occurring
* Position: The number of characters from the beginning of the file to where the error exists
* Row: The file line where the error exists
* Col: The number of characters from the beginning of the line to where the error exists
Special Note: The editor will translate traditionally non-viewable characters into something viewable.
* Windows based new line characters appear as ASCII Music Note ♪
* Linux & Windows based tabs appear as ASCII Dot ° (so in this case, using 8 spaces is a win over tab)Examples
The BAS folder on SPI flash contains example MY-BASIC files for you to learn from.
* BASFUK: There's something wrong with this, maybe you can fix it...
* COUNT: How to print messages to the output screen
* INPUT: How to get input from the user as well as use subroutines
* KEY: How to poll key press actions when INPUT isn't specifically used
* LED: How to blink the LEDs and change their color
* LOOP: How to use a loop
* RICK: How to play animations located in the /BLING_BW directory
* TEMP: How to read the ADC Temperature sensor value in Fahrenheit
* VOLTAGE: How to read the ADC Battery voltage sensor valueSettings
* Name Change : 6 characters max and a flag will be generated to associate your handle on the scoreboard
* Brightness : Use (SYM+A) to decrease and (SYM+D) to increase the LED brightness
* Pause & Resume Bling: Toggle this button by hitting enter to temporarily pause or resume bling. Bling is auto-resumed upon exit. This feature exists to mitigate potential SPI Flash corruption when copying or replacing custom files (e.g. RAW Animations, BAS) and Bling is playing. Essentially, if you plan on copying files to the badge's flash storage, you would be dumb to engage in a game of file system tug of war and willingly not pause the opposing party in your favor. We highly recommend you do this, or don't...we're not the boss of you.About
* Thanks to all the hackers & philanthropists that helped us bring this badge project together.
* Hugs to our sponsor frendz at Urbane Security, Penguin, & InspectAR.
* Hax0r contributors to this year's project: Doc, Kur3us, Alethe Denis, & Will Caruana.
* AND!XOR: Zapp, Hyr0n, Bender, 8Bit, Cr4bf04m, & F4nci3
* Thank you @arturo182 for your Blackberry Q10 research!
* Thank you Paladin-T (Tony Wang) for My-BASIC!Factory Reset
* Reset the badge settings to factory (i.e. our garage) defaults.
* This will not format the SPI Flash storage.
 Zapp
Zapp
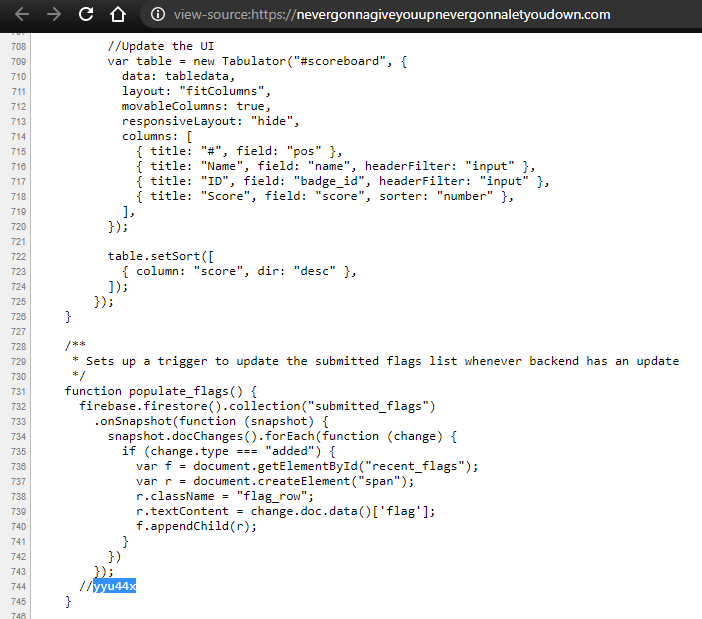




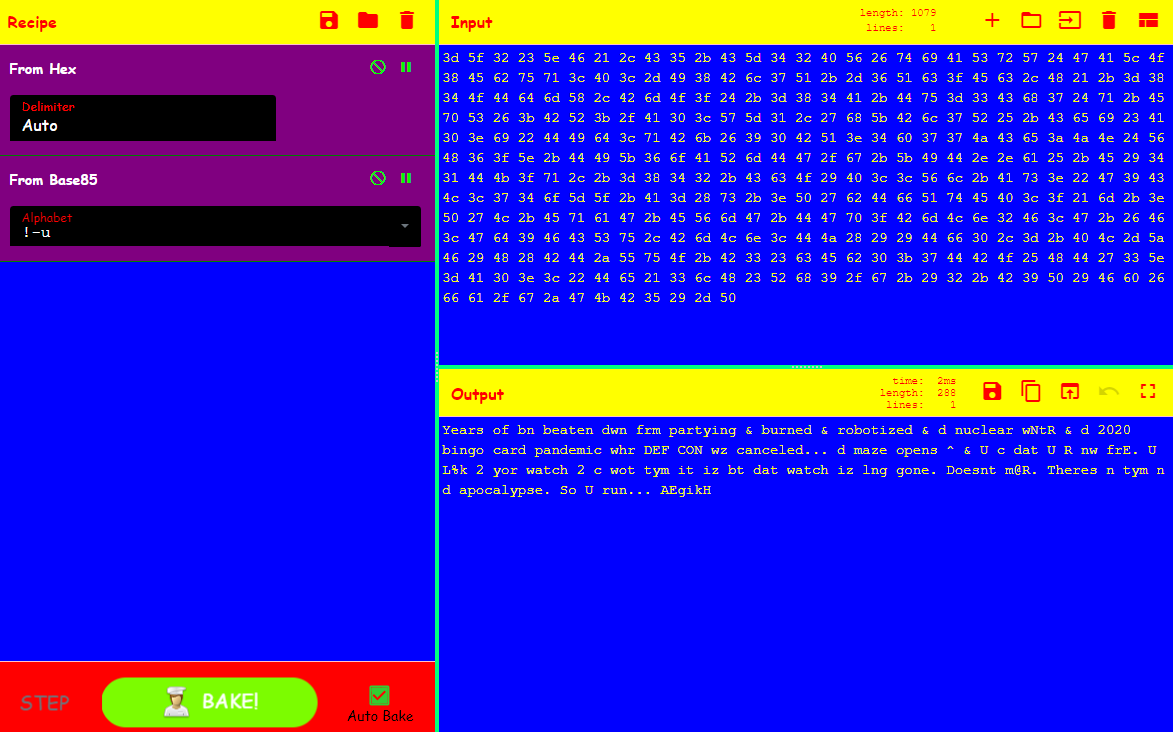
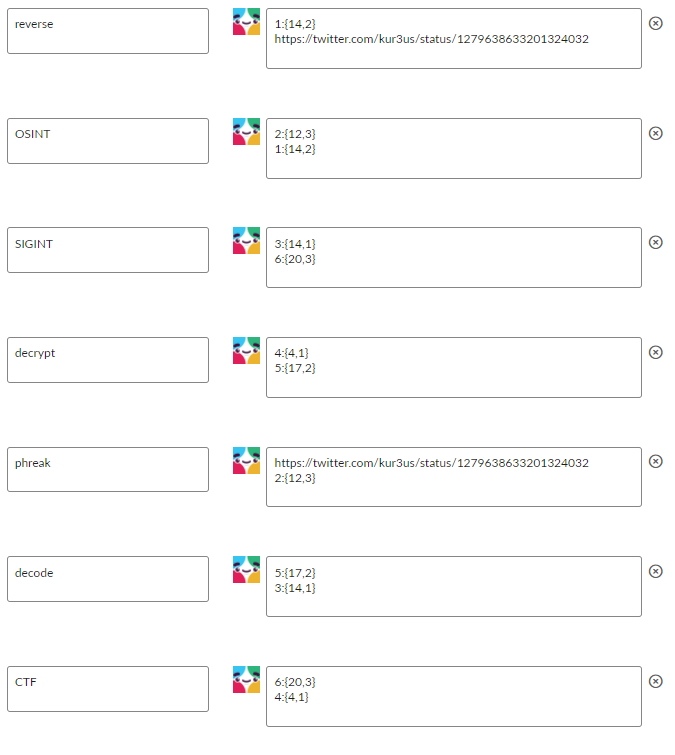

 Super Serial? Think about the least and most significant things? C'mon what better hints could we have given you? Now if you've never worked with serial a quick google on how the protocol works will teach you that charachters are turned into binary, it pads a 0 as the start bit, it INVERTS the LSB/MSB order (so its received correctly), then the end is appended with a 1 as the stop bit. The blink pattern shown would translate to...
Super Serial? Think about the least and most significant things? C'mon what better hints could we have given you? Now if you've never worked with serial a quick google on how the protocol works will teach you that charachters are turned into binary, it pads a 0 as the start bit, it INVERTS the LSB/MSB order (so its received correctly), then the end is appended with a 1 as the stop bit. The blink pattern shown would translate to...