-
1Step 1
WE GONNA DO IT BACKWARDS?
Okay If you have be watching my project. In the details section. I unboxed the ZMODO NVR Security System. And come to find out the NVR unit doesn't come with any kind of storage nor a password. So I got it coming in the mail. Until then I'm gonna move to the camera side of the system. Go check it out to see how i came to this point.
So here's what i got...
![]()
ZMODO Wired IP Camera
Model: ZP-IDQ13
SKU: ZP-SS76D001-S
That uses a funny cable...
![]()
Female Micro-USB to RJ45 Ethernet Cable. Appx. 100 ft. long. So i decided if the NVR is off the table. I'll just see what i can do with the camera. Well I connected the camera and cable together. Plug it in to my router and guess what ? NOTHING. A big fat zero. Then I decided to plug it in to my laptop's port and guess what? NOTHING. Another big fat zero! Man this thing is as dead as my ex-wife on love making night!!!
After doing some digging I found out this is a sPoE IP CAM. What's that?
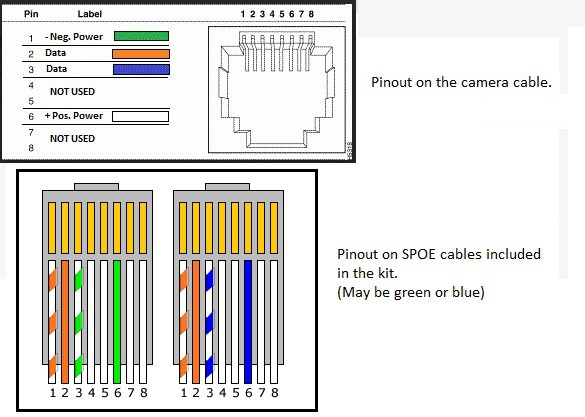
sPoE, an abbreviation for simplified Power Over Ethernet, PoE technology lets network cables carry electrical power in addition to data, making surveillance easier and more affordable.
![]()
As you can see it's based off a 8 pin RJ-45 connector. Power and ground runs off pin 1 & 6. 1 being your negative or GND. 6 being your power or postive. Pin 2 & 3 carries the data or your video. Since I'm talking sPoE. I also want to mention something I found before somebody asks or try to experiment.
[!]And I quote.
" There are 2 reasons that a PoE switch or injector will not work, the first reason being that the sPoE cameras only accept 19V of power, and typical PoE is 48V, the increased voltage will very quickly damage the cameras. The second reason is the pinout configuration on the camera, PoE uses all 8 pins, 4 for power and 4 for data, the sPoE cameras only use 4 pins, 2 for power and 2 for data. " Okay moving on...
If you look at the picture I posted above the camera it's self is pointed all the way over to one side. See how all the IRs are on one side? (If your wondering what a "IR" is hold tight get there in a little while.) This means you can mount the ring that the camera hangs from and install the camera but you have no way to point it. This means you gonna have to take the case apart to aim the camera inside.
![]()
If you will look to where I'm pointing theres a notch. You gonna have get your self a big flat head screwdriver. And pry it apart. It should just unsnap. Be careful not to be to rough. Or you may crack the case.
![]()
This is what it looks like with the case open. Now all you do is lock it into the mount and aim the camera. Snap the case back on. If you want to just finish installing and configuring you will have to skip the next few steps.
-
2Step 2
TIME FOR A REBUILD !!!
Okay for the people that decided to stick around and see what's under the hood. I want you to know this is my first time modding / hacking one of these NVR camera systems. I have tinkered with most any kind of gizmo under the sun. So, Im gonna try to do my best but dont take my word as the gospel. Double check EVERYTHING I say. DO THIS AT YOUR OWN RISK. If you can help. Please do. I will besure to give credit where its due.
This is my first Hackaday.io project and my aim is. For this project to be the goto project for china made junk. With that being said. If you will be kind enough to share methods and code. I will take the time to explain it. Were everybody should be able to understand or atleast be able to complete what we are trying to accomplish. No matter there skill level.
Where should I start? I guess the "Why?" is a good place. Everybody should know the reason for what they are doing something. I could name a 1000 reason why. Just don't have time for all that right now. Companies over seas do not give a damn what they are selling us these days. Some are even using the stuff we buy from them against us. There is NO other way to say it.
Anything from scamming us out of more money. To spying on us. Just go out on a limb with me for a second. Don't you think it's odd that china sales this system and a crap ton more exactly like it. Just with a different name stamped on it. Instead of it saying ZMODO on it. It may have Ying-Yang. Still the same NVR cameras and cables. With NO harddrives included. I think I proved that in the details section. Don't believe me. Look at the pictures yourself. Yet has ready made cloud server preinstalled and ready to rock in roll..... With little to no way to disable or uninstall. I guess just dumb luck. Huh?
Most everybody here has delt with these devices before. It is no secret that hardly ever do you just pull them out the box. Slap it together and even 25% of the stuff work with out having to play with it for 2 days. Some of the features never goes to working. I can tell you the 2 things that has always worked. That cloud server and that call back home script.
lol Omg I just want to see one device that them two things were broke out broke when it got unwrapped. I mean they have managed to brake all 150 other key features. Never either of them two. We all know were our live video goes after it comes out that DVR or NVR. Before it makes it to our TV or hand held. That's right CHINA. Where you think all those cloud and call back servers are located at?
If these companies are not gonna play right. And Nobody here gonna make them play right. We gotta lock em down our selfs. That's all there is to it. Fact of the matter security system are a safety device. Just the same as a bullet proof vest.
If they gonna hack us. We need to make sure they don't cut any corners. Sit your butt down in front of a command line. Pull your sniffers, crackers, injectors, scripts, and handmade tools out. Put them long hours in just like everybody body else. NO FREE PASSES YING.
-
3Step 3
WHAT'S THE PROBLEM?
Ok thanks for reading my disclaimer slash rant. Okay we all know the point of doing this. So lets get in to it. I left off at I just opened the case on the camera. First thing first. Lets figure out how it works and why its broke. That way we will know how to fix it.
The good people in China has built these things to where. When these camera are powered up. It encrypts the video stream before it ever leaves the camera. Not only that. It tries to hide the actual camera's connection. Best i got it figured. Thats to hide the encrypted stream so you can't decode the stream it's self nor all the other info they have stole.
![]()
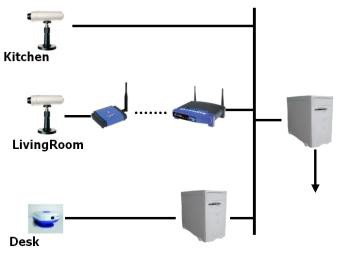
What other information could a camera get you ask? It's like this. Anytime you put a device on the inside of a private network. It inherits certain privileges. This is just how a network works. If every device was totally locked down and hidden. None of the network devices could see each other. Trade data among each other etc....
So when a device is added there a certain level trust that it is given. So it can coexist with all the things connected to the network. Back to the information theft. It knows what your internal ip address is for sure. It can be made to take a look around. To see how many and what kinds of devices is on the network. Not only that it can even tell what the devices are doing. Aww I'm just crazy. If so prove it. If all the data is encrypted and hidden. They is no way to prove what it is or isn't sending and receiving. None the less if you look above this what a network kind looks like. This Is pretty much the easiest way i can explain it.
Okay now we have this piece of junk from china sitting on our network. That has encrypted and hidden it's self. I mean total lock down. Since it don't have all the hardware needed to get whatever it's holding out of the private home network on to the public internet. It has to ask for help. This is where the NVR DVR comes in. First of all the camera need to stay hidden. So we cant get a hold of the stream. So the NVR and the camera makes a encrypted / hidden connection. Very little of this can be seen by other devices on the SAME network.
![]()
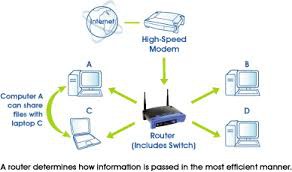
Ok now think about this. Pretty much the NVR and how ever many camera on the network. Has made there own network where it's just China device talking to other China devices. Inside YOUR network. So pretty much all these little China machines can say and do what they want. It's all up to whoever programmed them wanted them to do at the time. Without you being able to control them in anyway. As long as they don't try to pass though the networks router where you have the control.
The router in most cases acts like the boss of the network. It hands out the ip addresses. Says who comes and who goes. If it catches a device doing what it shouldn't. It can block the internet connection. If the device is really being bad it can blacklist the device. Kick it out the network and refuse to let it back in. Just like mama use to do.
Not the case with "Ying" the camera from China. And "Yang" the NVR/DVR from China. They have got there own network going inside your network. Because Yang the NVR has a little secret he is half router too. Yang gets is IP address / internet from your router. Then makes a door for Ying the IP camera from china. By sharing his address and connection! Nice huh?
Okay the camera has got video stream and whatever else it's decided it wants. Nobody knows it's all encrypted and hidden. Now it need to get the data off your network. On to the public internet. But there's one thing stopping it. Your network router / boss. The camera can't do it. Heck the router doesn't even know it's on the local network.
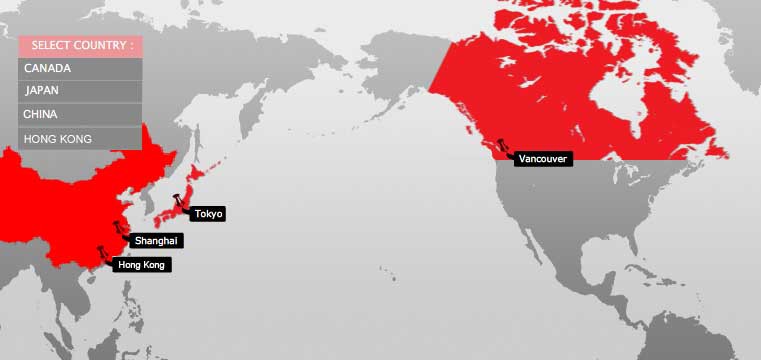
Here comes the trick read closely... The camera passes the data to the NVR / DVR from china. The NVR tells you. "Hey I got the feed from the camera. But before I can show it to you. I need a password to unencrypt it." Now I'm gonna stop right here for a second take a look below.
![]()
It is 11,671km or 7252.0232 mi from the capital of China to the capital of the US.
It took a 7200 miles trip one way with your data to ask for a password. The software on the NVR and the firmware has totally locked out the end user. The only way to stop this from happening is to unlock the software / firmware. Or replace it with different software / firmware combo
-
4Step 4
WE KNOW THE PROBLEM WHAT NOW? GETTING TO KNOW THE Hi3518
Okay we know the problem our camera and NVR has the end user locked and sending our data to the other side of the world. We Need to unlock it or replace it.
First thing to do it figure out how the camera is built. Important things to note. As we take a look at the device. What runs it? Were is it being store at? How did it get loaded on the device? How can we get a copy? If so can it be unlocked? If not can it be replaced?
![]()
Ok we already had the top of the case open. Now the actual camera needs to be remove from the sweval. I removed the two screws. one from each side.
![]()
![]()
remember the pinout diagram i show you? 4 wire total. 2 for power. 2 for data. I'm counting 6. Need to figure out what the other 2 do...
![]()
Here's the other side and it had to more wires.
![]()
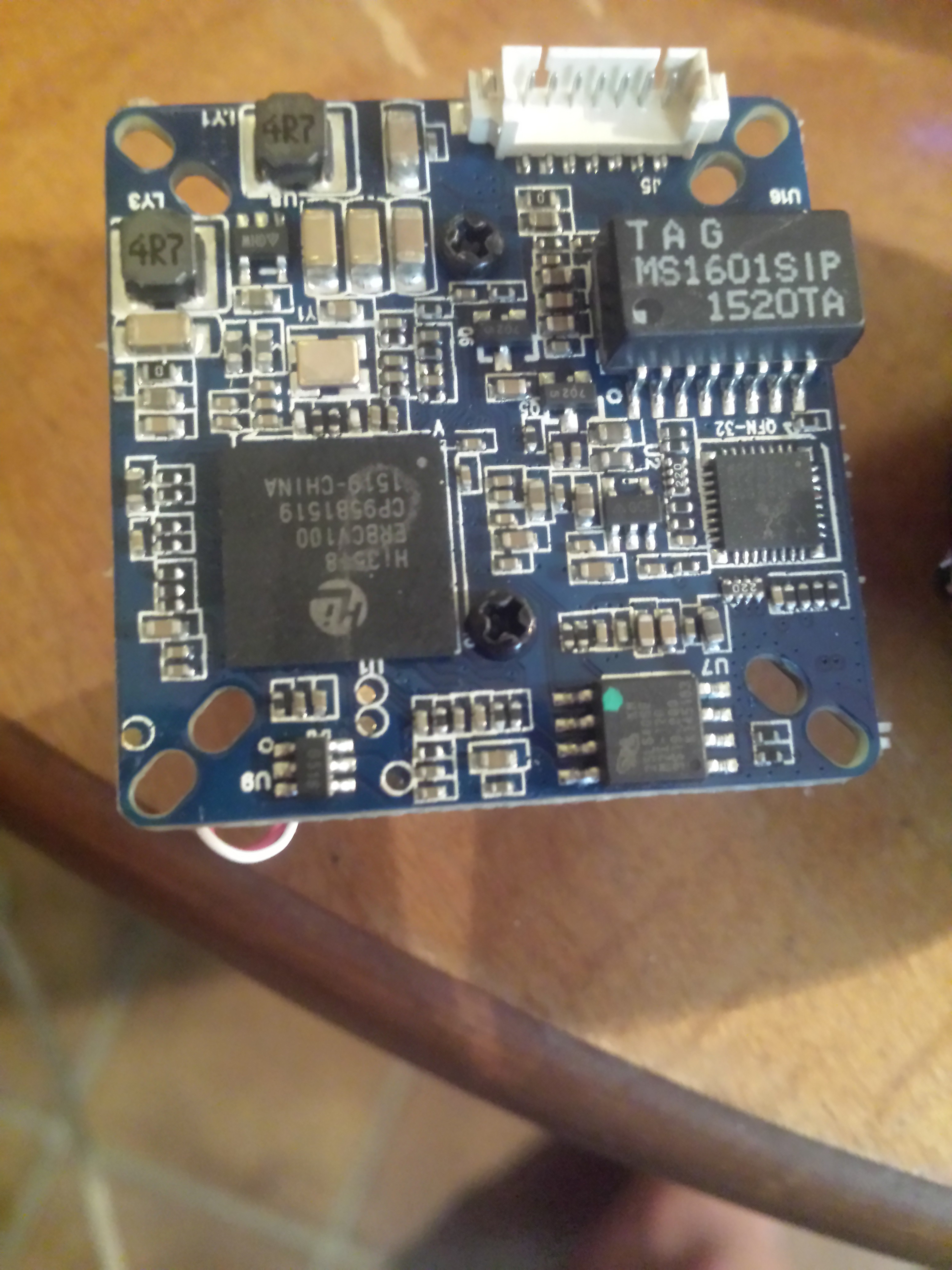
Here's a close up of the PCB. This I can way check what each chip is. I already see a couple things jumping out at me.
![]()
![]()
![]()
Exploring China Made NVRs DVRs & Cameras
Goal: Modding china made security systems. DVRs NVRs IP Cams
 Dr.Query
Dr.Query








Discussions
Become a Hackaday.io Member
Create an account to leave a comment. Already have an account? Log In.
OPENIPC look into your cameras chip and find it on the OpenIPC website.
Are you sure? yes | no
Just in case you didn't figure out the cabling, here goes:
RJ45 side - camera side
Orange/White - Green
Orange - Brown
Blue/White - Blue
Blue - White
My cable got wet in a rainstorm and the SPoe connector got wet internally. Ended up hardwiring around the interface connector at the camera.because the connector pins corroded off.
Are you sure? yes | no