RPi Zero WiFi-Enabled Hardware Password Manager
Codename Hardpass: A Password Manager on the Raspberry Pi Zero...suffering featuritis.
Codename Hardpass: A Password Manager on the Raspberry Pi Zero...suffering featuritis.
To make the experience fit your profile, pick a username and tell us what interests you.
We found and based on your interests.
hardpass-proto.pdfSchematicoctetstream - 42.17 kB - 02/21/2016 at 17:25 |
|
|
old_driver_ignore_this.zipZip Archive - 4.05 kB - 02/15/2016 at 20:06 |
|
|
hardpass.svg.zipmockup in 1:1 scale, for component placement and shows gpio-pins in useZip Archive - 8.96 MB - 02/08/2016 at 07:23 |
|
|
Oh boy, here we go again: an update.
I haven't progressed a lot in the past year with this project. A big part of it was that I wasn't able to get the smart card interface to work. I've spent countless hours planning, designing and otherwise working on hardpass-sci and was in the end defeated by the awful driver situation of the chip I settled on.
I was originally drawn to the Philips/NXP TDA8029 because I've seen a github repository containing the driver for it. I didn't do much research into the driver, and assumed it was OK. However, after getting the hardware ready the true state of the driver came apparent. Not only was the Philips' driver written for an extremely old version of PCSC, it was kept outside of the main PCSC distribution, requiring manual updates to it to keep working. Which of course didn't happen. Then, larytet on github did some changes, the commits were helpfully labelled "Update." After getting in touch with them, they weren't quite sure what they were doing the three years ago when the "updates" were commited, and the driver's implementation wasn't fully finished either.
Well, there goes that into the drain.
Not wanting to write my efforts off as waste, I tried to keep working on the TDA8029, but my motivation was pretty gone.
By sheer luck I found out about the Microchip SEC1210 -- another RS232/UART Smart card interface chip! And guess what: It's driver is in mainline PCSC since last May!
The documentation around this chip is quite nice: I've found the schematics for the evaluation board right on microchip's website, and got to work on implementing a PCB. Right after, I sent the boardfiles to @oshpark and I'm now waiting like a small child on christmas eve for them to arrive.
The SEC1210 is only available in a QFN package -- and I don't have a hot air gun or a reflow oven, so we'll see how that turns out :S (any tips appreciated!)
the pcbs are marked version 0.2.4 -- if this turns out well, the sec1210 will mark the beginning of hardpass 0.3!
I'm still waiting on one. single. capacitor. (-.-), but at least I can have a look at the PCBs. I tried a different manufacturer (easyeda.com, 8€-something for 10, delivered!) just to spice things up.
1) yes, soldering is atrocious. I still haven't bought a good soldering iron. 2) yes, I missed a trace and bodged some magnet wire in.
It really shows the scale - even the sim card looks huge! here it is on top of the smart card that will go in hardpass-SCI.
As of yet, I am still waiting for C13, as evident in the pictures above. So I haven't been able to test my circuit yet.
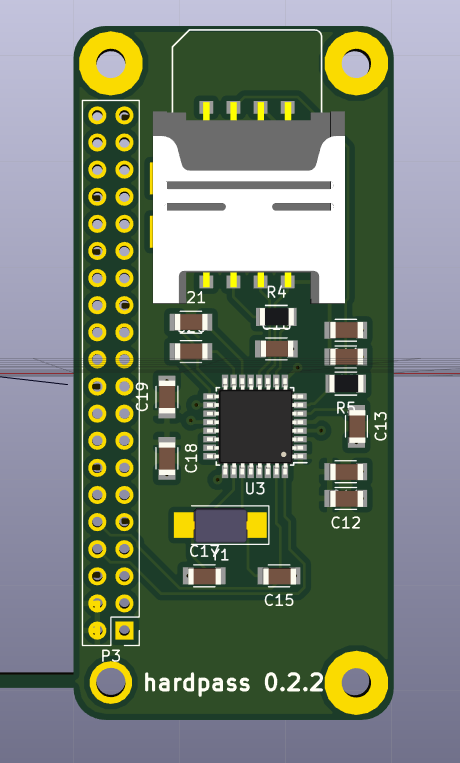
Here I've stacked up hardpass 0.2.2, a Raspberry Pi Zero-W, and hardpass-SCI 0.2.3. As you can see, there is still some air, but I measured the thickness to be 12mm to the top side of the top PCB. I recon I can get it a bit thinner still. Right now, the buttons are the thickest part I can trim down relatively easily, so the current ones will probably have to go in a future revision.
Another angle. hardpass-SCI sits so close to the Pi i am a little worried about shorting out the test pads on it. Nothing a little kapton tape can't solve ;)
Next steps:
* get the hardware finished
* work on the UI (passwordstore has evolved a lot as well)
* design a case: 3d print? laser cut? wood? sheet metal?
So I've been stumped by doing the OLED implementation myself. I couldn't get the screen to reset with the RC circuit, so I finally replaced it with the APX803 circuit, Adafruit used in this schematic.
I really need to get myself access to an oscilloscope :|
For now, I'm using the hacked together PCB you see below, but new ones are ordered. (my iron was way to hot for the flatflex, i know...)
Next step: hardpass-scm - the smart card interface.
I posted them in the new project page for the hackaday prize
already, but for completeness, there they are again.
the new board does not use the OLED breakout board, but instead has all the circuitry on board. the schematic I used is from adafruit's break out, and is linked in the project's github.
I've created a new project for the Smart Card Interface PCB. Check it out!
also, I've created a home page for my stuff, and hardpass is the first thing I started to document there. >> gir.st/hardpass.htm <<
So I might add proper ISO7816 smart card support to this thing now.
My reasoning is that if you were to lose your hardpass, the attacker won't be able to get hold of the (encrypted) private key. And since GnuPG Cards are supported by gpg (duh) and therefore pass, I don't have to implement my own crypto (which is basically the motto for this whole project).
There is a relatively old chip, the Philips/NXP TDA8029, that should be well suited to translate between the card's protocol and serial data. Someone has also written a driver for a reader based on that chip, and I hope I can adapt that one.
The SIM holder can easily obtained from AliExpress by searching for "samsung i9000 sim", and is originally from linkconn.
I managed to not use the backside of that PCB (which shouldn't really be an achievement to more professional designers), so I might fill that up with logos and text :D
The Smartcard I plan on using is the GNUPG card, and kernelconcepts.de sells one that has standard SIM size breakout tabs. (ordered already, but still in shipping **EDIT**: they came! man, a SIM card is huge compared to a Pi 0)
The board is already in the master branch of the github project.
**EDIT**: Now with primitive 3D model (FreeCAD). Yes, a standard SIM card is really that big compared to a Pi Zero.
Once I'll get my old boards from @oshpark and getting comfortable with smart cards in general, I'll continue working on this board.
Thanks to the ZeroPhone I was motivated to take some time and solder a board together.
It works! Now, I should take some more of my time to write some more software...
(please excuse the awful soldering job - I was out of flux and couldn't be bothered to order some)
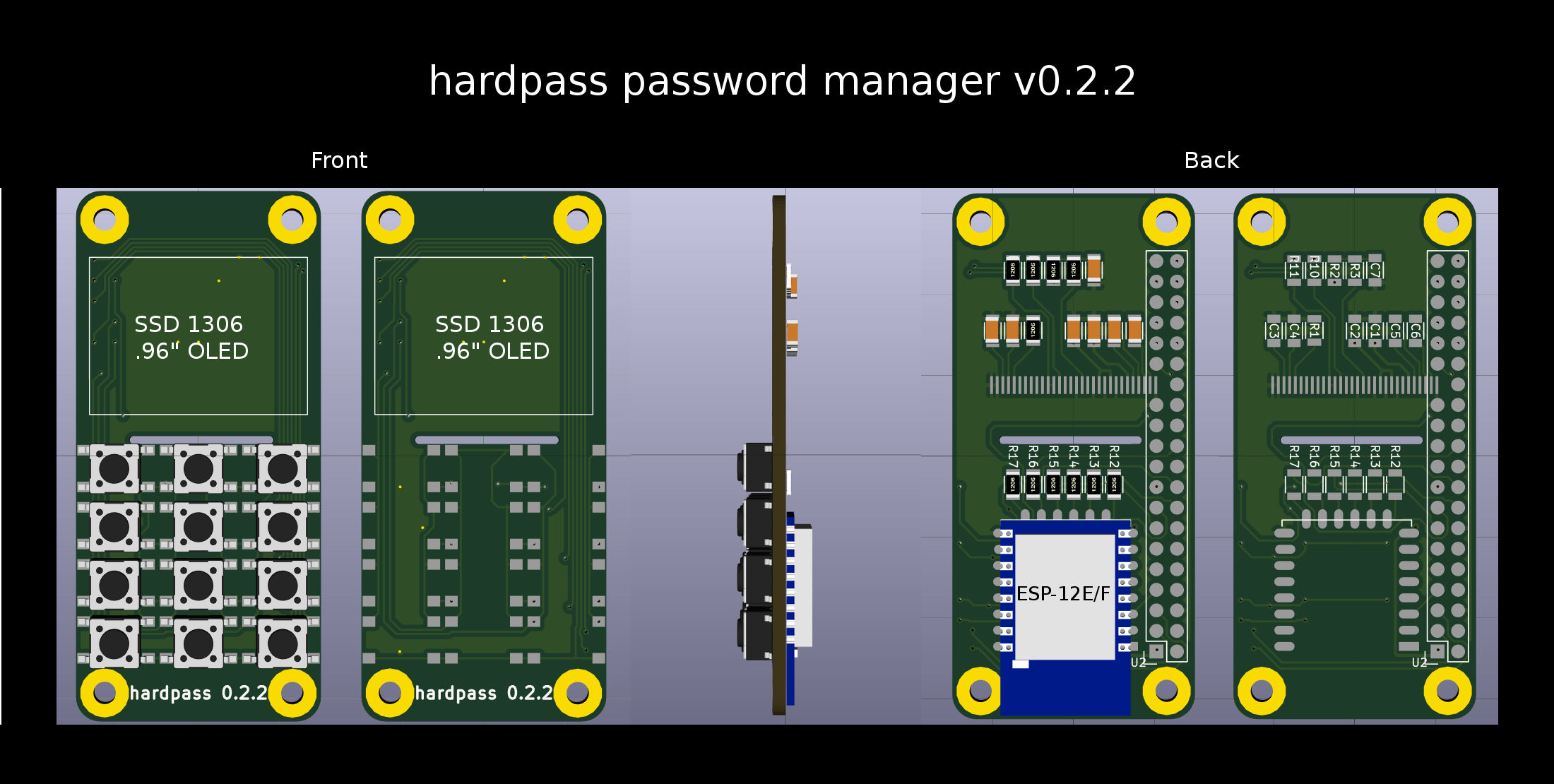
The front. I managed to squeze the ESP completely under the PCB in the `30pin` branch of the git repository.
Since I don't want to sacrifice a Pi for each generation of the hardware, I opted to a header. The height is still tolerable even with the header and makes it about the size and thickness of a typical car keyfob.
Without said header, the thickness can be reduced to roughly 8mm board-to-board. Then, the case of the ESP12 touches the SD card slot. I guess, one could remove that, but I haven't tried. (and yes, my shitty caliper broke and I fixed it with duct tape)
The board from the bottom. I bridged the OLED module over like this, because I couldn't remember the pinout of my module, and a search on AliExpress revealed, that they all have a different one.
As you can see, there isn't much space between the header and the ESP. This is the order of soldering I recommend: start with the header, then solder the ESP and its resistors, continue with the OLED and bridge it over, and finally solder the buttons (put it in a vice or in a Pi).
Hello world! this is the (already working) menu. use `*` as the up arrow, `#` as the down arrow, and `0` to select. I want to make the numbers jump directly to the `n`th item in the list, but that's on the todo list (as well as button debounce :S)
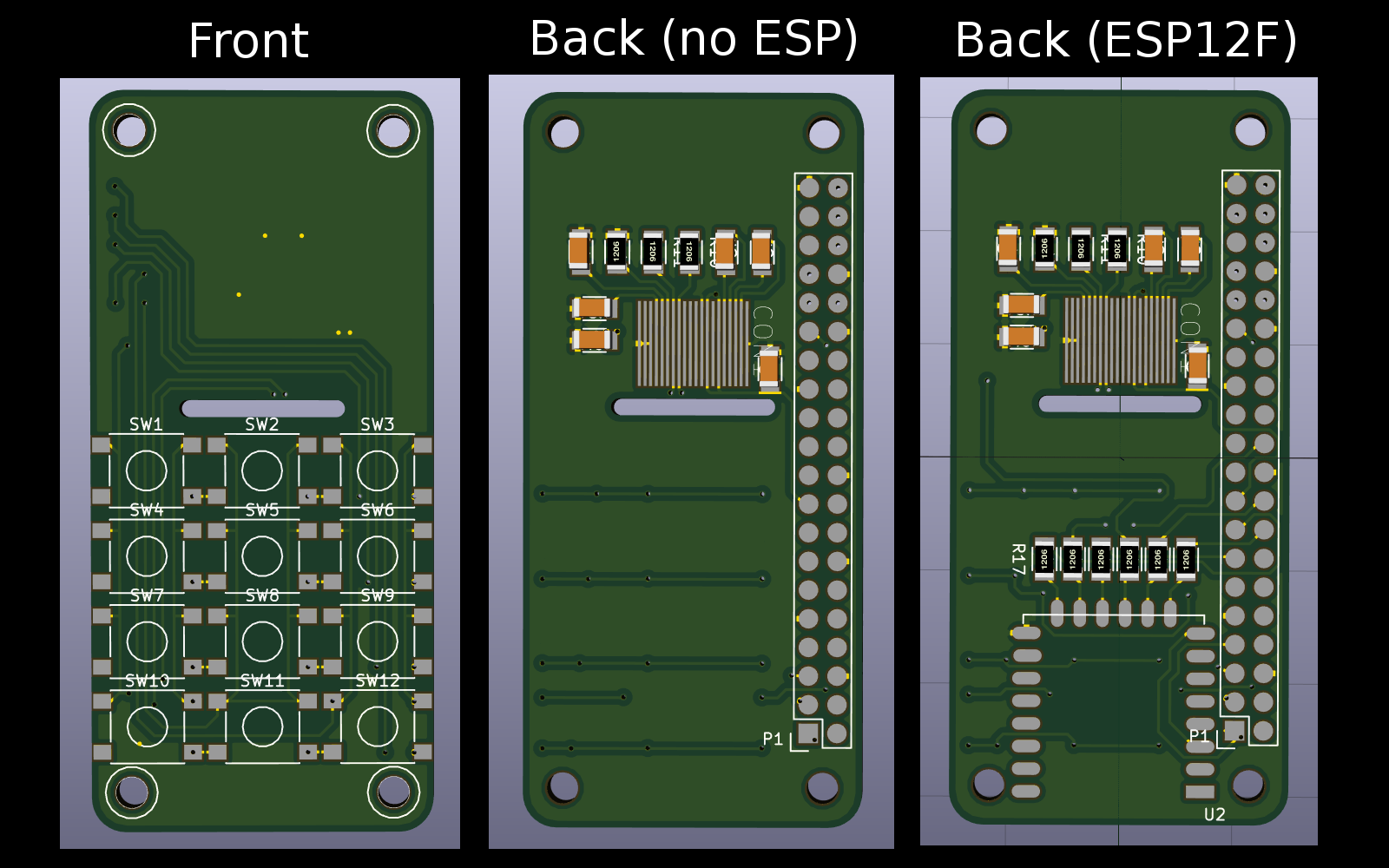
So...I couldn't help myself and completely redid the PCB from scratch. The header should be aligned now (had to modify my footprint with the anchor in the center). For the 30 pin variant of the oled i had to remove one of the unused pins; we'll see if that works out. Something else that needs to be seen to be tested out is the slot for the oled's flat flex. It should be large enough to get one "wing" in at a time, but no promises :s
I shelfed the project for some time, but recently I have been working on it again. The 20-pin OLEDs aren't available on AliExpress any more (the last seller who claimed to have them didn't have them).
So I modified the PCB to take the premade assemblies / modules. (I do plan on modifying the PCB to take 30 pin OLEDs)
I also finally ordered some prototype boards from OSHPark (really streamlined ordering process, just upload the pcbnew-file)
On the top of the back side you see those solder pads under the screen header: While many OLED modules have 4 pins, all of them have different pinouts. I plan on soldering jumper wires to set the correct connections.
On this picture you can see all the components involved (except the .1" header and some resistors, which hvaen't arrived yet)
The one and only [Brian Benchoff] published an article on this project. I took this opportunity to update the GitHub repository, as I have completely neglected that one for way too long (will push later today/tomorrow).
This week I also did work on the PCB again: rerouted some tracks, repositioned the (previously misaligned) header, and added a footprint for an ESP-12 module. You can clearly tell that that is just bodged in by the way all the traces had to be routed. But I managed to stay on two layers, which reduces the price of PCBs massively.
(that should say ESP12E, not ESP12F - sorry)
UPDATE: Code and PCB files are now on a new GitHub repository: https://github.com/girst/hardpass-passwordmanager
The old one is there: https://github.com/girst/hardpass-sendHID
Create an account to leave a comment. Already have an account? Log In.
i abandoned the tda-chip, as the drivers available haven't been updated in over a decade and don't work with modern tools, unfortunately.
So are you using any other means for contact smart card interface ? Let me know as my college work is to authenticate the incoming RFID card data using an already existing iso7816 smartcard digital certificate
Your project is amazing! Congrats! (Sorry about my english isn't very well). I have a question: are you using SPI interface to communicate with the sec1210?
How does this compare to using something like a password manager's database on an encrypted flash drive?
I love how this looks and I want to make one, but I'm concerned about usability. It seems like it would take a long time to scroll to the correct password entry. Are there plans for auto-detection of the current open window (if a program) or current open URL (if in a browser)?
Also, would this have the OS encrypted on the SD card in case it was found and someone tried to break in?
@Arsenijs - it would be awesome to integrate something like this as an app on the #ZeroPhone - a Raspberry Pi smartphone
:-)
See the last log on this project =) Actually, my Reddit and GMail accounts told me about suspicious activity today. I'll go switch all my password to "pass" this week, it seems - then I'll just need to develop a pyLCI-driven interface.
Hi.
This works in Windows machines??? I'm having troubles with drivers. I'm using Windows 8.1
Best Regards,
Daniel Tavares
libcomposite drivers are not available for windows unfortunately. you can use g_hid (the old one) - that'll only give you keyboard/mouse emulation without the ethernet emulation, but if i am not mistaken, windows drivers are available for that one.
as i do not own any windows machine, this is not currently a priority - but a feature to switch drivers is on the to-do-list ;-)
I would love to get my hands on one of these boards for my Zero!
A project I have been wanting to create for a long time now is a portable Pi, which can carry all my Python scripts and can be easily selected and executed using buttons. I had been planning a gameboy style build with an arduino pro micro (ATMega32u4) attached via i2c to allow HID connection to a PC.
Your project design looks a million times better suited than what I had in mind ha ha!
Thanks! There is no board though - just the OLED and ESP-03 modules.
With the mass-storage mode or MTP mode you could probably even transfer your scripts to the pi rather easily.
that sounds absolutely perfect for what I need. Was going go look at FTP to stick files on it. I'm definitely going to have to order some parts on pay day!
Great work so far. I have a question, are you using the stock kernel that comes with Raspbian in order to achieve this? Was there any other preconfiguration that had to happen before you execute your bash script for the libcomposite drivers?
Hi! Yes, it is the stock kernel.
In LadyAda's tutorial she describes how to install a different kernel, but that wasn't necessary. I am also not using the driver she and gbaman used (which was the old one that could only do one gadget at a time), but `libcomposite`.
Where have you run into errors?
I'm an idiot. Of course, there was an extra step!
I use the 4.4 Kernel and dwc2 dtoberlay and driver.
See the ordered list on gbaman's tutorial: https://gist.github.com/gbaman/50b6cca61dd1c3f88f41 only numbers 3, 4, 5!
I also updated the README.md in the repo (thanks for letting me know)
Thanks! That fixed it and now I was able to get it to connect via USB. Still can't seem to get it to work on a Windows machine because I think the composite driver doesn't work on Windows. I'll have to get Linux up and running to see I have better luck there.
Bummer. For me, no windows support isn't that much of a problem, but good to know. There is an alternative to libcomposite though, the legacy single-mode gadgets (g_hid in our case).
you need to use this version and compile it yourself: https://download.plop.at/ploplinux/4.3.1//sources/99-ARM/cubietruck/hid.c
and it goes into drivers/usb/gadget/legacy/hid.c
iirc, it will work witout the initialisation script from my README.md
if you are interested, i will see if i can find the precompiled version for you
I would definitely be interested if there is a precompiled version was available. If not then I would try to compile the g_hid driver (since the one included in kernel 4.4.y doesn't seem to modprobe properly), much appreciate!
https://cdn.hackaday.io/files/9564409186176/old_driver_ignore_this.zip
here you go. copy it to where the foo file in the archive says you should ;)
since you can't ssh into your pi with this driver any more, and you also cant plug a hub into the pi, put this into your /etc/rc.local to test the driver: (if you use a usb to serial cable you are of course fine)
echo -ne "\0\0\4\0\0\0\0\0" # pushes the a button on the keyboard
echo -ne "\0\0\0\0\0\0\0\0" # releases all keys
this should type a lower case letter 'a' into the active window on the host pc.
(also, keep me posted on issues)
Driver works (in Windows too)!! Big help there, as this was one of the biggest hurdles I was having. Next thing I'm experiencing though is after plugging in the device into the PC, the output of the letter "a" didn't work after I put the two echos into the /etc/rc.local file. Question, do I need to compile your git in order to get the output to work?
quite likely: windows probably hasn't loaded the driver yet, when you try to send the 'a' key. put a `sleep 30` before the two echo statements to wait 30 seconds before sending. (maybe you need even longer wait times)
debugging is quite hard with the old driver, as you can't plug in anything but the host pc into the usb port. do you have / can you get hold of a usb to serial cable? then you could connect it to the pi's gpio, enable it in raspi-config and try out stuff. (this kernel doc page has a nice interactive c program for sending keystrokes: https://www.kernel.org/doc/Documentation/usb/gadget_hid.txt (starting from the line below "sample code" to the end of the file; compile with `gcc hid-test.c -o hid-test`))
things i could think of:
- is /etc/rc.local executed? see the output of `systemctl status rc-local.service` and put an `echo "hello world"` into rc.local
- can you give me an output á la `lsusb`, where you can see which usb devices are connected or a `dmesg`-esque syslog or something?
Finally got it to work! I dug up an old Nokia CA-42 USB serial cable and taped the wires (lol) to the GPIO holes. Afterwards, I was able to get the hid-test application to send HID commands. One issue I am still running into (which I really want to get working since I want it to be headless) is that I also tried adding hello world and the sleep to the rc.local file as you said and it did execute properly, but still the test letter "a" was not showing up on the machine which was odd. Maybe there is something wrong with the commands in the rc.local or I have to point it to /dev/hidg0 somehow? Thanks again!
yeah. my fault again. it should have been:
echo -ne "\0\0\4\0\0\0\0\0" > /dev/hidg0 # pushes the a button on the keyboard
echo -ne "\0\0\0\0\0\0\0\0" > /dev/hidg0 # releases all keys
as things seem to work now, you can however now also try my program: (rc.local is executed by root, so no sudo necessary)
i changed the text input from a parameter to a pipe. git the new version and use
echo -n "your text" | /path/to/scan /dev/hidg0 1 3
Success!! I got it to work (almost perfectly). Only thing I noticed is that when I am trying to use the hardpass-demo.sh, the scan application doesn't seem to like the variable on the end:
sudo ./scan /dev/hidg0 2 2 $(PASSWORD_STORE_GPG_OPTS="--passphrase test12" pass show Email/gmail.com|head -n 1)
And it brings up the "Usage Instructions" instead of accepting the variable.
In order to get it to work, instead I echoed the decrypted password variable into scan using this:
echo $(PASSWORD_STORE_GPG_OPTS="--passphrase test12" pass show Email/gmail.com|head -n 1) | sudo ./scan /dev/hidg0 1 2
After that it was able to create the output over hid. I am not sure if the echo is secure though as the initial way. Any idea what went wrong there?
yeah, the example above was the old syntax, the one you gave at the bottom is the new one. (updated on git - thanks (what would i do without you?))
you should however be able to remove the echo and the $(), as mentioned in the lastest project log:
PASSWORD_STORE_GPG_OPTS="--passphrase test12" pass show Email/gmail.com|head -n 1 | sudo ./scan /dev/hidg0 1 2
that will also preserve whitespace correctly (should your password for example contain two consecutive spaces).
Become a member to follow this project and never miss any updates

 natalie
natalie

 Taiwo
Taiwo
Hi gir,
I was seeking the schematic for iso7816 interface using tda8206 as you have mentioned. I am trying to make a contact based smart card authenticator using raspberry Pi. Is there any link for that ?