Hardware
The Hardware is designed to be a relative generic and reusable Module around the ESP8266 WiFi Plattform. The Schematic is loosley based on the NodeMCU Project, however instead of breaking out all the free pins, all pins are used for a bunch of devices.
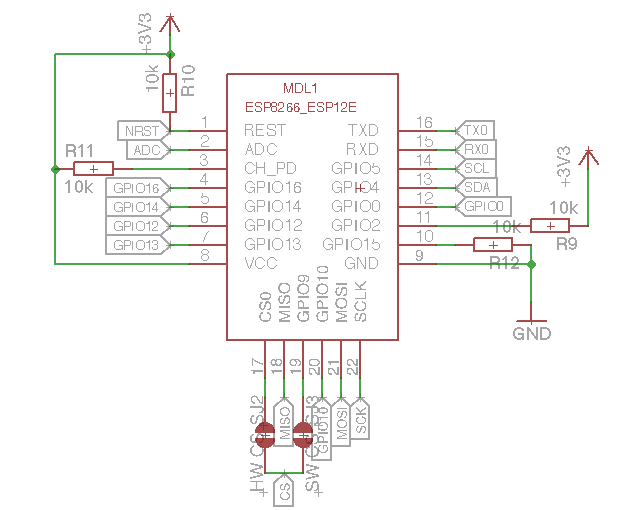
The Device has the following Hardware
- SSD1306 based OLED Display, connected via I2C
- microSD Card Socket connected over the SPI interface
- 3 general purpose buttons
- ESP8266-12E Module
- TPS63031 Buck-/Boost-Converter with an input range from 1.8V - 5.5V
- MCP73831 Single-Cell LiPo Charger Chip
- CP2012 USB to UART converter Chip
Software
The software is of course the part where all the security features are implemented.
It still is under heavy development. A List of planned features are listed here:
- Layer 1:
- Since the ESPs Radio is not really configurable it is not possible to create a WiFi Jammer that works by emitting broadband noise or any other Layer 1 attacks
- Layer 2:
- Deauthentification attack
- collecting authentification frames and save the keys to SD card for later decryption (using a wordlist on a computer, the ESP neither has enough memory nor enough processing power to crack them on the system)
- arp spoofing and session hijacking when connected (needs investigation)
- evil twin hotspot
- Layer 3 (after connecting to an AP):
- Host discovery (IP Scanner)
- Ping flooding (ICMP Pings)
- Layer 4 (after connecting to an AP):
- Port Scan on Host
- Random MAC-Address on Power Up
- Random Mac Address while performing critical Tasks
 Daniel Grießhaber
Daniel Grießhaber














 Paul Andrews
Paul Andrews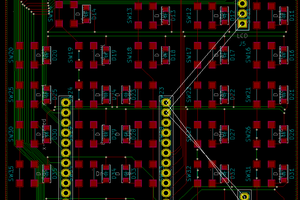
 Timm Murray
Timm Murray
 danjovic
danjovic
 Alexander
Alexander
I briefly worked on capturing the 4-way handshake, but gave up, as I could only get the first 112 bytes of the packets in promiscuous mode. You mention that as one of the planned features. Have you found a way around that limitation?
I'll have a try with the ESP32 next. Espressif claimed "full packet receive" in their current SDK release notes.