The Kim Uno was feeling lonely when all of a sudden a new Hackaday.IO challenge came out, create a program in less than 1kB of code. Most of the enigma machine simulators out there use LED displays and buttons mounted in a PCB. I wanted to create my own without rolling out a custom PCB. Thus the idea was born to write a program to simulate an Enigma Machine in 6502 assembly language.
The Kim Uno has a hexadecimal keyboard and 8 control keys. On top, it has a cluster of 7 segment displays where 6 numbers can be displayed, 4 on the left and 2 on the right. This is not enough for a regular enigma machine which encrypts letters A through Z. Fortunately, a very rare numbers only model, called the Enigma Z30 exists.
Enough information was published by Anders Wik to make this reconstruction attempt possible.
"Enigma Z30 retrieved", Anders Wik, Cryptologia Vol. 40 , Iss. 3,2016
http://dx.doi.org/10.1080/01611194.2015.1055387
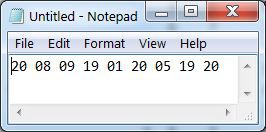
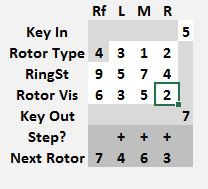
The Z30 machine has 4 settable rotors that show the numbers 0 thru 9 one at a time through a window, a keyboard with 10 keys numbered 0..9 and 10 lamps above the keys.
When a key is pushed, the rotors are first advanced, then electricity is sent through the rotor maze and it comes out to illuminate a lamp. The keys are wired to a stationary set of contacts on the right which send electricity in through the right contacts of the rotor and out through its left side contacts into the next rotor.
The leftmost rotor is a reflector, it receives a signal on the right and returns it through another pin on the right. This sends electricity back through a different path through the rotors and out to the lamps.
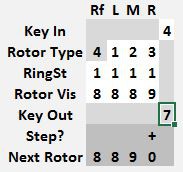
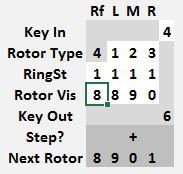
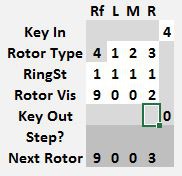
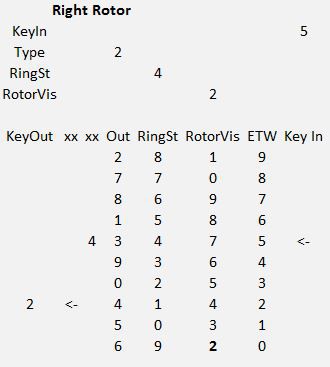
Each rotor, including the reflector has a ring setting that controls the stepping position for that rotor. When set at 1, a rotor at the 9 position will increment the rotor to its left when the next key is pressed. The rotor on the right always moves one step. This results in the sequences: 0088 0089 0090 0101 0102 and 8888 8889 8890 8901 9002 9003 and is known as the double stepping anomaly.
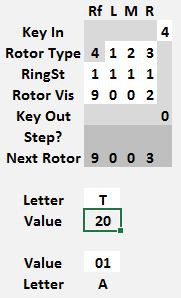
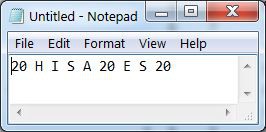
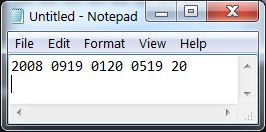
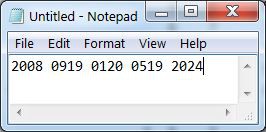
A key will never encrypt to itself. To decrypt the numbers, the machine is re-set to the same starting position and the encrypted sequence typed. The decrypted numbers will be illuminated in the lamp field.
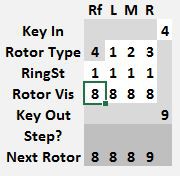
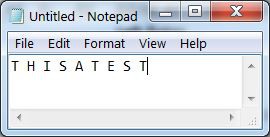
To use the Kim Uno Enigma Z30 machine, enter and execute the program. The rotors will be shown on the left and 00 on the right. Since 0 can never encrypt to 0, this was chosen to represent the machine is ready to encrypt. To encrypt a number, press a 0..9 key. The rotors will be advanced and the key encrypted. The key and its encrypted result will be shown for 1 second on the right two digits and the screen will then return to 00. On a normal enigma machine, the lamps will be lit for as long as the key is pressed. I did not find a way to read that the key is still pressed, so the result is cleared after one second or if another key is pressed.
The top row of keys start and stop a running program. Those cannot be read within a running program.
The next two rows below that have 4 keys each and are used to move the rotors up and down one step.
The remaining keys, 0..9 when pressed, are encrypted. Keys [A] [B] and [GO] are not used.
The default machine settings, Rotor Types 1,2,3, Ring settings 1,1,1,1 and Starting position 4,3,2,1 are copied to memory location 0050 where they can be examined and changed to encrypt. The left rotor is always a reflector, so its type cannot be set.
The basic program uses 460 bytes of code including the rotor substitution and default value tables. It uses the KIM 1 GETKEY and SCANS routines at $1F6A and $1F1F. Those routines and their dependencies add 150 bytes of code for a total of 610 bytes of our own code and dependencies as per the contest rules. The KIM-1 monitor is an unavoidable bootloader that is necessary to enter the program and get it running.
Update:
A full featured user interface was written that allows the user to change the machine settings on the fly without exiting...
Read more » Arduino Enigma
Arduino Enigma
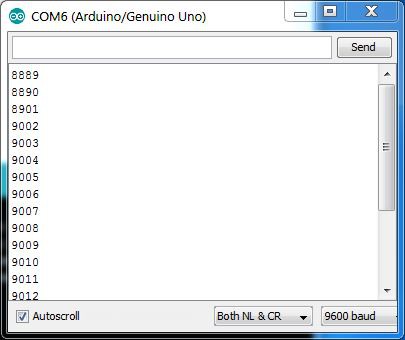
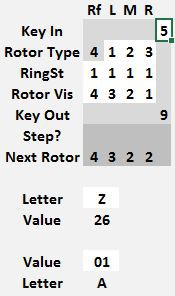
 Note the Next Rotor position is 0 0 0 1. Before starting to encrypt anything, copy that rotor position values from the Next Rotor row to the Rotor Vis row.
Note the Next Rotor position is 0 0 0 1. Before starting to encrypt anything, copy that rotor position values from the Next Rotor row to the Rotor Vis row.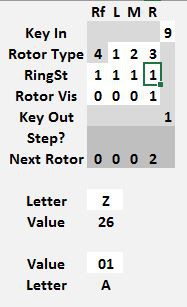



 Mrinnovative
Mrinnovative
 David Boucher
David Boucher
 ptrav
ptrav
 Greg Kennedy
Greg Kennedy